
The Implosion of Black Basta: A Deep Dive into the Leaked Chat Logs and Operational Collapse
The recent leak of internal chat logs from the Black Basta ransomware syndicate has provided unprecedented visibility into the operations, conflicts, and eventual disintegration of one of the most prolific cybercriminal groups of the past three years. Spanning 196,045 messages exchanged between September 2023 and September 2024, the logs—leaked by an individual known as ExploitWhispers—reveal a toxic cocktail of internal power struggles, financial scams, and reckless targeting of Russian financial institutions that precipitated the group’s collapse. This report synthesizes technical details, operational patterns, and geopolitical tensions extracted from the logs, contextualizing Black Basta’s rise as a Conti offshoot, its tactical evolution, and its migration of key operators to emerging ransomware groups like Cactus and Akira.
Black Basta emerged in early 2022 as a direct successor to the Conti and REvil ransomware syndicates, leveraging their infrastructure, affiliate networks, and malware toolkits. Analysts such as Yelisey Bohuslavskiy of Red Sense have long posited that Black Basta represented a merger of personnel and tactics from these defunct groups. The logs confirm this lineage, with references to former Conti operators adopting new aliases like “Bio” (later “Pumba”) and “Trump” (Oleg Nefedov), who orchestrated Black Basta’s campaigns.
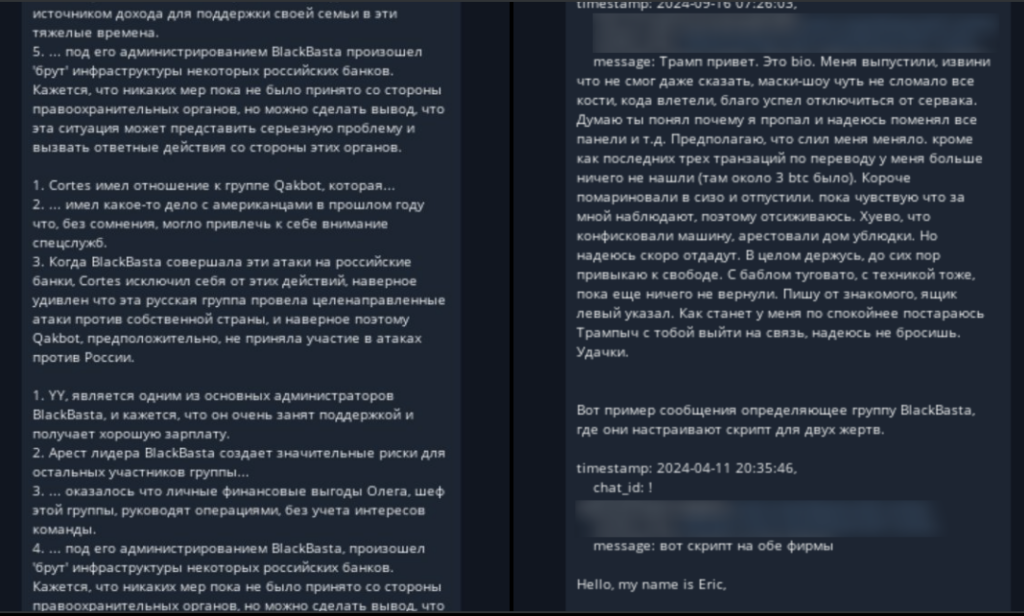
Black Basta’s modus operandi relied on a hybrid approach combining technical exploitation and psychological manipulation. Initial access was frequently achieved through phishing campaigns distributing malicious HTA files, which deployed payloads like Qakbot to establish persistence. The group exploited vulnerabilities in VPNs (notably Fortinet and Pulse Secure), exposed RDP servers, and unpatched VMware ESXi instances. Once inside a network, lateral movement was facilitated by tools like Cobalt Strike, while data exfiltration preceded encryption to pressure victims via double-extortion tactics.
The group maintained a centralized spreadsheet of targets, tracking compromised credentials, social engineering attempts, and negotiation statuses. This spreadsheet—shared among affiliates via ZoomInfo links—contained entries for 367 organizations, including healthcare providers, critical infrastructure operators, and financial institutions.
The logs include:
● Phishing templates tailored to industries like healthcare and finance, complete with sender email addresses and cryptocurrency wallets for ransom payments.
● Operational playbooks detailing escalation tactics, such as threatening to leak stolen data within 10–12 days of non-payment.
● Infrastructure details, including IP addresses, domains, and credentials for command-and-control servers.
● Internal disputes, such as admins berating affiliates for missed deadlines or poor performance6.
Researchers at Hudson Rock processed the logs into an AI chatbot (BlackBastaGPT) to enable natural language queries, revealing granular insights into the group’s workflows and personalities.
Central to Black Basta’s implosion was “Tramp” (LARVA-18), a Qakbot distributor whose spamming network facilitated initial access for numerous attacks. Tramp’s unilateral targeting of Russian banks in late 2024 triggered fierce internal backlash, with operators like Cortes (a Qakbot affiliate) publicly distancing themselves to avoid blowback. Compounding this friction was widespread grift: admins such as YY and Lapa admitted in chats that some affiliates pocketed ransums without providing decryptors, eroding trust in the RaaS model.
Oleg Nefedov (alias Trump, GG, or AA), Black Basta’s ostensible leader, prioritized personal enrichment over operational security. The logs depict Nefedov micromanaging affiliates while withholding payments from critical personnel like Lapa, who managed backend infrastructure despite earning “significantly less” than peers. This exploitation bred resentment, with one affiliate lamenting, “We’re not his employees—we’re his slaves”.
Black Basta’s operators exhibited a relentless focus on acquiring and testing VPN exploits. Chats reveal a 17-year-old affiliate (identified only by the handle “Z3r0”) tasked with probing Citrix and Palo Alto Networks devices for unpatched vulnerabilities. Successful exploits were immediately integrated into automated attack pipelines, with payloads tested against CrowdStrike and Defender AV instances hosted on internal lab servers.
To evade detection, the group cycled through bulletproof hosting providers in Moldova and Kazakhstan, leveraging residential proxies to mask malicious traffic. Encryption routines were customized per victim, with logs indicating the use of intermittent encryption (targeting specific file types) to accelerate deployment.
By January 2025, Black Basta’s collapse was irreversible. A “mass migration” of affiliates was observed to Cactus and Akira, groups offering favorable profit splits (80/20 compared to Black Basta’s 70/30). This exodus mirrored the Conti diaspora of 2022, underscoring the fluidity of cybercriminal alliances.
● Fragmentation: The ransomware-as-a-service model will further decentralize, with smaller, transient groups avoiding the pitfalls of hierarchical governance.
● AI-Driven Attacks: Groups like Akira are experimenting with LLMs to generate polymorphic phishing content, a trend likely to accelerate.
● Geopolitical Constraints: Attacks on Russian entities will remain taboo, as evidenced by ExploitWhispers’ retaliatory leak.
The Black Basta leak epitomizes the paradoxical vulnerability of cybercriminal enterprises: their technical sophistication is invariably undermined by human greed and hubris. For defenders, the logs offer a masterclass in adversary TTPs, from exploit prioritization to psychological warfare. For policymakers, they underscore the urgency of harmonizing international ransomware sanctions. As the line between cybercrime and cyberwarfare blurs, the demise of Black Basta serves as both a cautionary tale and a blueprint for future counteroperations.
Organizations must now internalize these lessons—bolstering VPN configurations, auditing third-party access, and adopting AI-driven threat-hunting platforms to preempt the next generation of ransomware threats. The ghosts of Conti and Black Basta loom large, but so too do the opportunities for resilience.
Resources