Vulnerability Management
What is the ThreatMon Approach to Vulnerability Management?
Vulnerability management is a process that aims to manage vulnerabilities in an organization's information systems effectively. This process involves identifying vulnerabilities, assessing their potential risk, and taking steps to mitigate or remediate them. It aims to minimize the organization's security risk and enhance its resilience against cyber threats. ThreatMon provides Vulnerability Management support to its customers. This process focuses on identifying, assessing, remediating, and continuously monitoring potential vulnerabilities in information systems, enabling client companies to address security issues on their digital assets. ThreatMon makes sense of the vulnerabilities identified through security analysts and automated processes and provides a detailed risk assessment to determine the potential risks of these vulnerabilities to the organization. This feature helps customers prioritize the most critical vulnerabilities.
Get Free Premium Access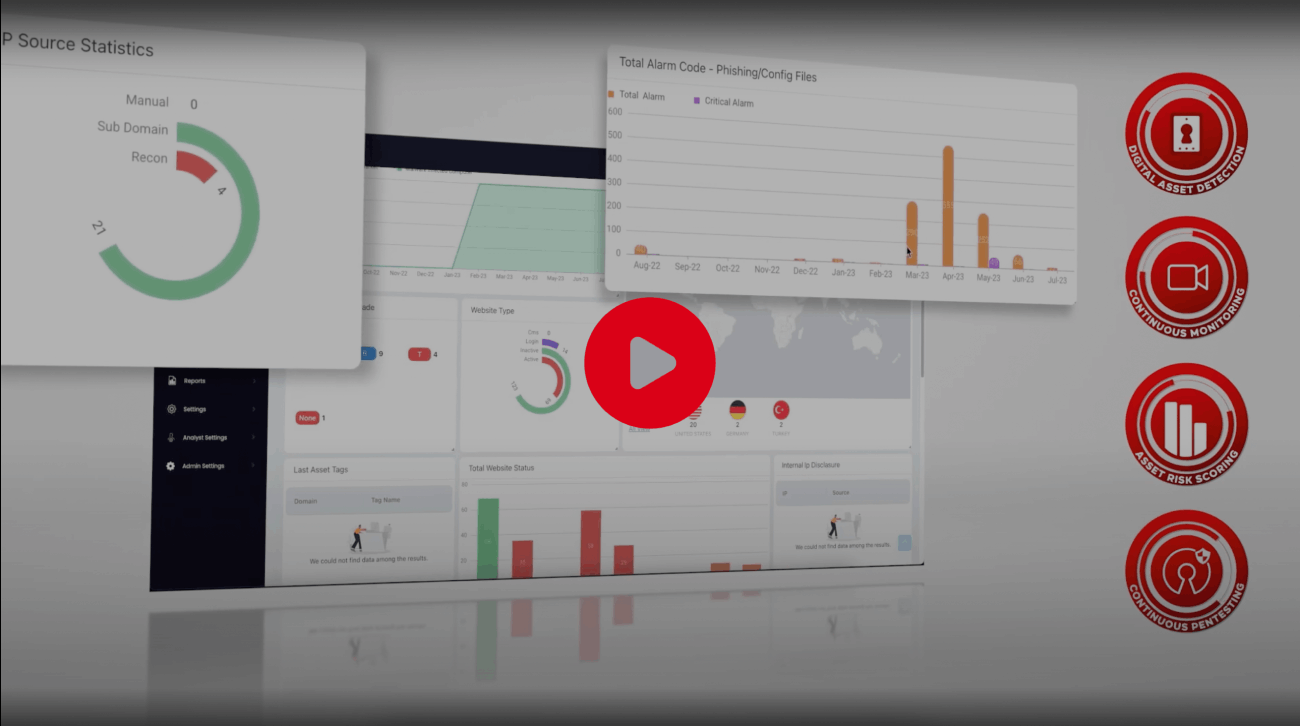
How does ThreatMon help with Vulnerability Management?
ThreatMon’s vulnerability remediation and prioritization transform an unorganized inventory of thousands of vulnerabilities into a prioritized list of those that are most exploited.
ThreatMon provides and details mitigation and remediation methods to its customers to eliminate each vulnerability it detects.
ThreatMon continuously monitors its customers' digital coverage, keeping their security status up to date and notifying them immediately when new threats emerge.





ThreatMon Vulnerability Management Key Features

ThreatMon helps organizations prepare more effectively against security threats by leveraging a large security database with Centralized vulnerability intelligence.

ThreatMon calculates an organization's security risk score by taking into account all security issues detected in the external attack surface. In this way, it gives its customers an idea of the security risk rating.

ThreatMon comprehensively aggregates, displays, and tracks all activities, findings, and security statuses related to its customers' digital assets in real-time dashboards.

ThreatMon consistently observes the digital footprint of its clients, ensuring their security status remains current, and promptly alerts them upon the detection of emerging threats.

ThreatMon provides regular security status reports to its customers, assessing the impact of identified security problems, proposing solutions, and ensuring they are ready for potential risks.

ThreatMon conducts scans on externally accessible assets, including web applications, servers, cloud-hosted services, and IP addresses. The aim is to detect, monitor, and manage these assets effectively for organizations.

ThreatMon offers strategic reporting capabilities that provide valuable insights into regional and industry-specific threat trends. These reports help organizations understand the broader threat landscape and make informed decisions to enhance their security strategies.

ThreatMon sends you push notifications that you can customize according to your needs to inform you about security problems detected on your organization's digital assets.
Holistic Product Approach for Better Security
ThreatMon is designed as an integrated product that covers the entire security process, not just one component. In this way, it offers all the tools organizations need on a single platform to discover, assess, manage, and protect vulnerabilities in one place.

ThreatMon provides the advantage of managing security processes from one central place. Organizations can work on a single platform without needing different tools and systems to discover, assess, manage, and protect vulnerabilities. This feature of the platform saves time and resources and increases efficiency.
Learn MoreThreatMon proactively monitors threats that can affect the security of organizations' digital assets. This feature of ThreatMon includes risks such as malware, phishing attacks, data leaks, reputational damage, and more. ThreatMon provides customers with real-time threat information, enabling them to react quickly and minimize potential damage.
Learn MoreThreatMon detects the external digital assets of the organization by performing active and passive scans on the entire internet. It then provides continuous monitoring of the identified external attack surface.
Learn MoreCustomer Reviews
“I appreciate ThreatMon's ability to provide organizations with a comprehensive view of external threats. Integrating Managed Security Service Provider (MSSP) panel usage allows managed security service providers to offer their customers a holistic understanding of external threats."
- Technical Teams Manager“Our institution, which holds a significant presence globally, relies on numerous outsourced services. Managing, tracking, and controlling these services has proven to be quite challenging.' However, with ThreatMon, we now seamlessly handle these tasks. ThreatMon conducts regular activities, investigates system vulnerabilities, detects and reports brand threats, and, most importantly, presents all findings user-friendly.”
- Information Systems Operation and Technical Support Manager“ThreatMon consistently conducts thorough analysis and promptly reports the attack surfaces of our organization in response to external threats. The cloud-based platform they offer enables us to efficiently access and track data, facilitating effective threat monitoring and response.”
- Chief Information Technology OfficerFAQ
Start Your Free Trial Now!
The free trial of ThreatMon allows users to explore the product's security benefits. During this trial period, you can test Threat Intelligence data, detect threats to your organization and recommend security measures.
Start Free Trial
