
WordPress Sites Hacked with Fake Cloudflare DDoS Alerts: Attackers are tricking users into downloading malware.
DDoS protection pages typically verify whether the site visitor is actually a human or part of a Distributed Denial of Service (DDoS) attack or other unwanted bot.
Bad bots make up a large portion of web traffic. These include DDoS traffic, scrapers scavenging email addresses to send spam, bots trying to find vulnerable websites to be compromised, and more.
Bots also consume bandwidth on websites, causing increased hosting costs and corrupting meaningful website visitor statistics.
Recently, a malicious JavaScript injection was discovered by Sucuri affecting WordPress websites, resulting in a fake CloudFlare DDoS protection popup.
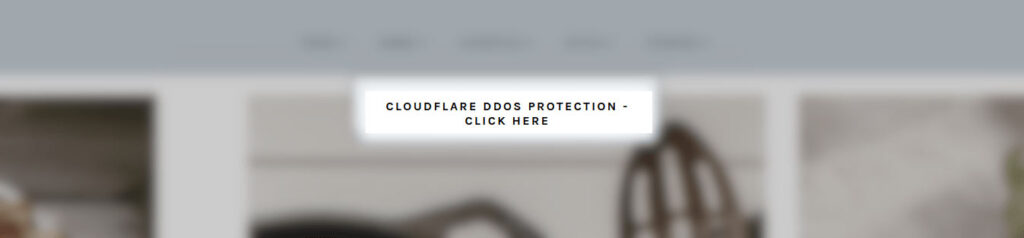
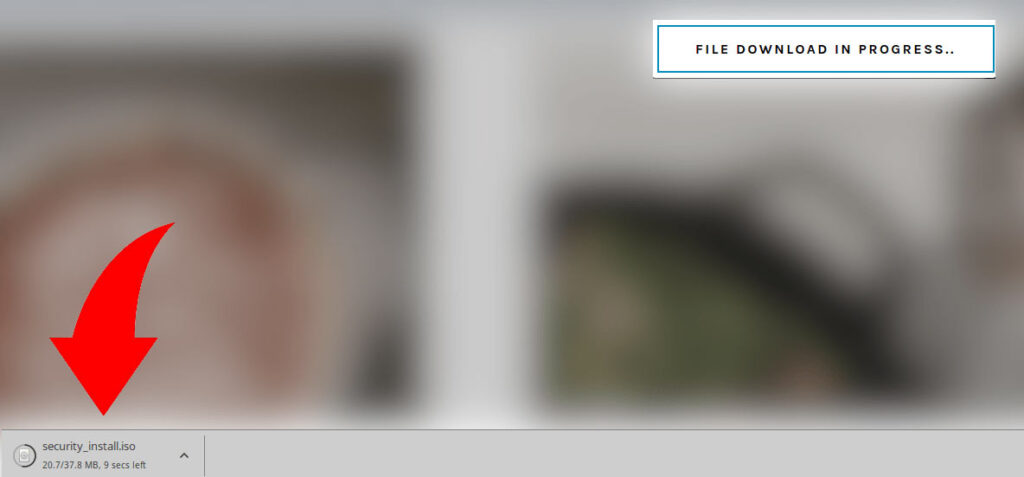
Such browser controls are common on the web. For this reason, users can click on this request without thinking twice. This prompt actually downloads a malicious .iso file to the victim’s computer.
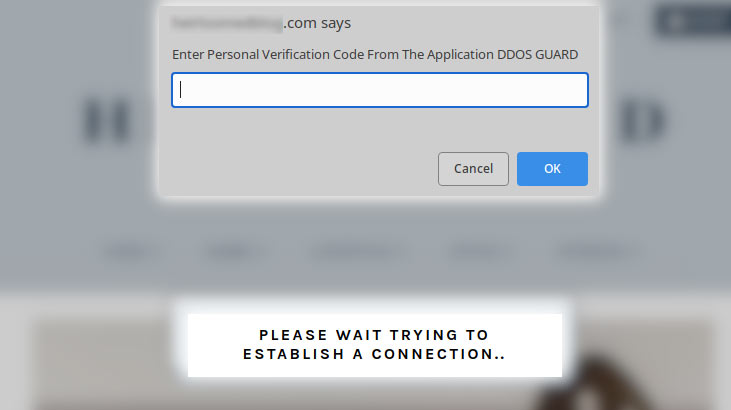
Next comes a new message asking for a verification code to access the website. This message is to persuade the user to open the file.
“This is NetSupport RAT. It has been linked to FakeUpdates/SocGholish and typically used to check victims before ransomware rollout. The ISO file contains a shortcut disguised as an executable that runs powershell from another text file.” Jerome Segura said.
“After that, just about anything can happen depending on the victim.”
The infected computer can be used to steal social media or banking credentials, detonate ransomware, and even imprison the victim in a malicious slave network, extort the computer owner and breach their privacy.
Not only SEO rankings or website reputations are important, but also the privacy and security of users visiting your website.
“Remote Access Trojans (RAT) are considered one of the worst types of infections that can infect a computer, as they give attackers full control over the device,” sucuri said in the report.
Here are some steps Sucuri recommends to reduce the risks:
https://blog.sucuri.net/2022/08/fake-ddos-pages-on-wordpress-lead-to-drive-by-downloads.html