
APT41, one of the state-sponsored ex-hacker groups, breached government networks in six US states in March 2022, including by exploiting a vulnerability in a livestock management system, according to Mandiant researchers.
Cybersecurity firm Group-IB’s investigations resulted in nearly 80 proactive notifications of APT41 attacks against their infrastructure to private and government organizations worldwide.
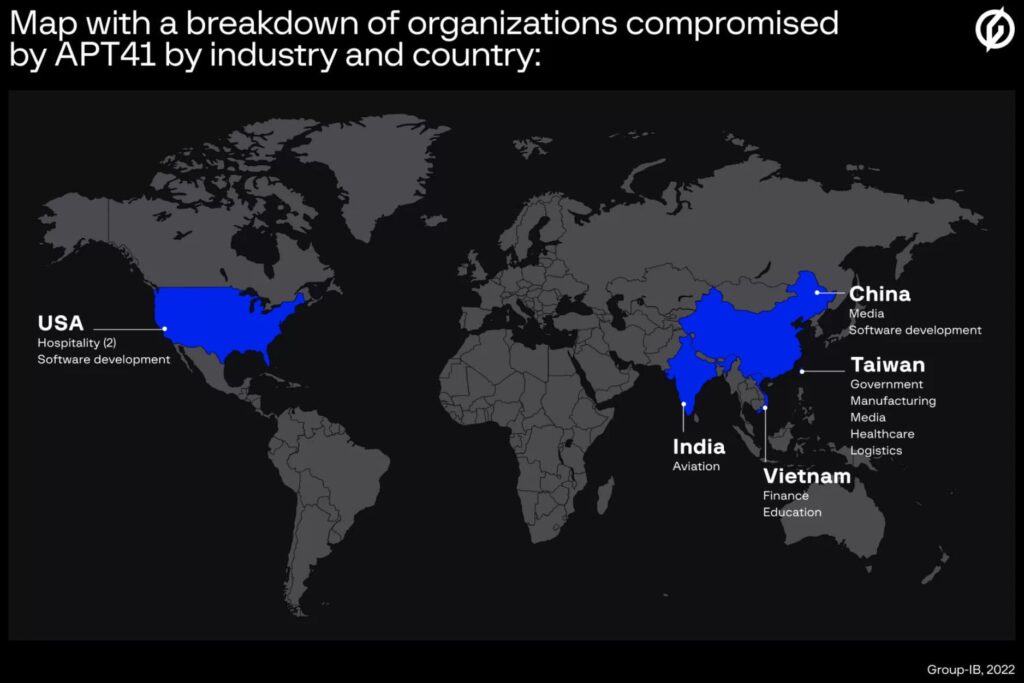
The group’s targets include government and private organizations based in the United States, Taiwan, India, Thailand, China, Hong Kong, Mongolia, Indonesia, Vietnam, Bangladesh, Ireland, Brunei and the United Kingdom.
According to the analysis, the sectors targeted by APT41 in the campaigns are the government sector, manufacturing, health, logistics, accommodation, finance, education, telecommunications, consultancy, sports, media and travel.
Attackers use tools such as Acunetix, Nmap, Sqlmap, OneForAll, subdomain3, subDomainsBrute, and Sublist3r for discovery.
During its infiltration phase, APT41 used various techniques such as spear phishing emails, exploiting various vulnerabilities (including Proxylogon), and thirst and supply chain attacks.
Threat actors used SQL injections in some cases. Such attacks were carried out with the publicly available SQLmap tool.
APT41 members gained access to a target server’s command shell and were able to execute certain commands. The group also used this tool to upload files to the target server. At this stage, the files were either Cobalt Strike Beacons or custom web shells.
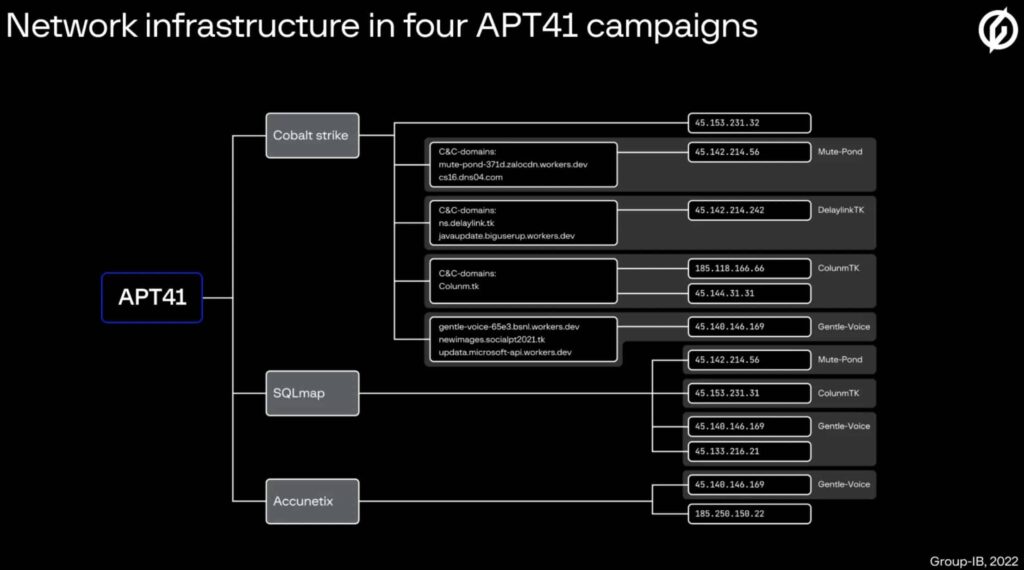
The group usually uses certain servers only to host the Cobalt Strike framework. It uses others only for active browsing through Acunetix.
By the end of 2021, the number of Cobalt Strike servers exclusively used for command and control reached 106, according to Group-IB Threat Intelligence data. However, many of them are no longer active.
The cybersecurity firm said that while this tool has been favored by cybercriminal gangs targeting banks in the past, it is now popular with various threat actors, including notorious ransomware operators.