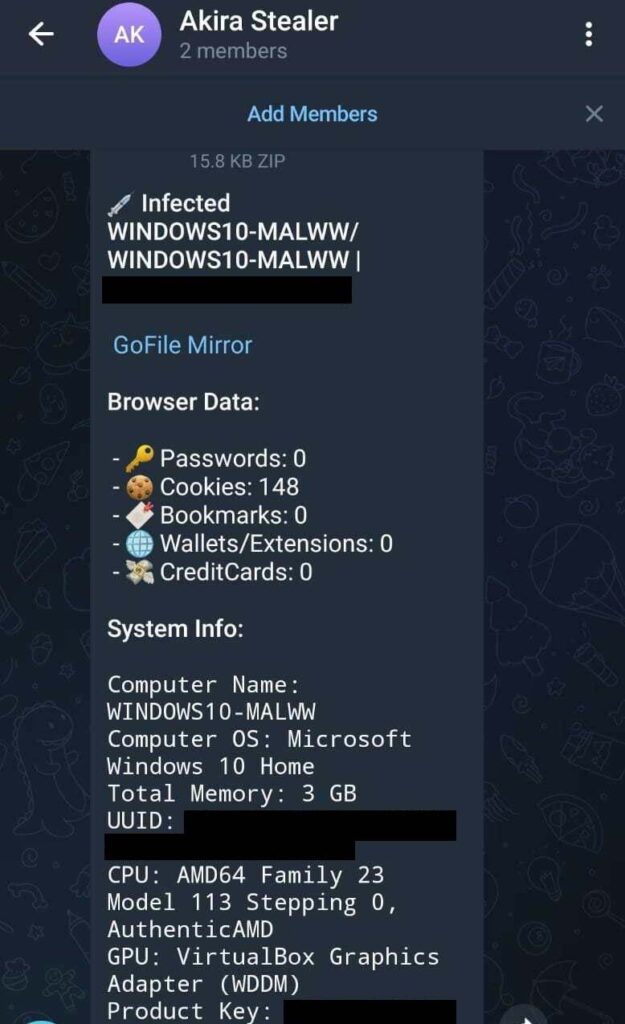
A new Stealer named Akira has been put up for sale on Telegram. It has the following features:
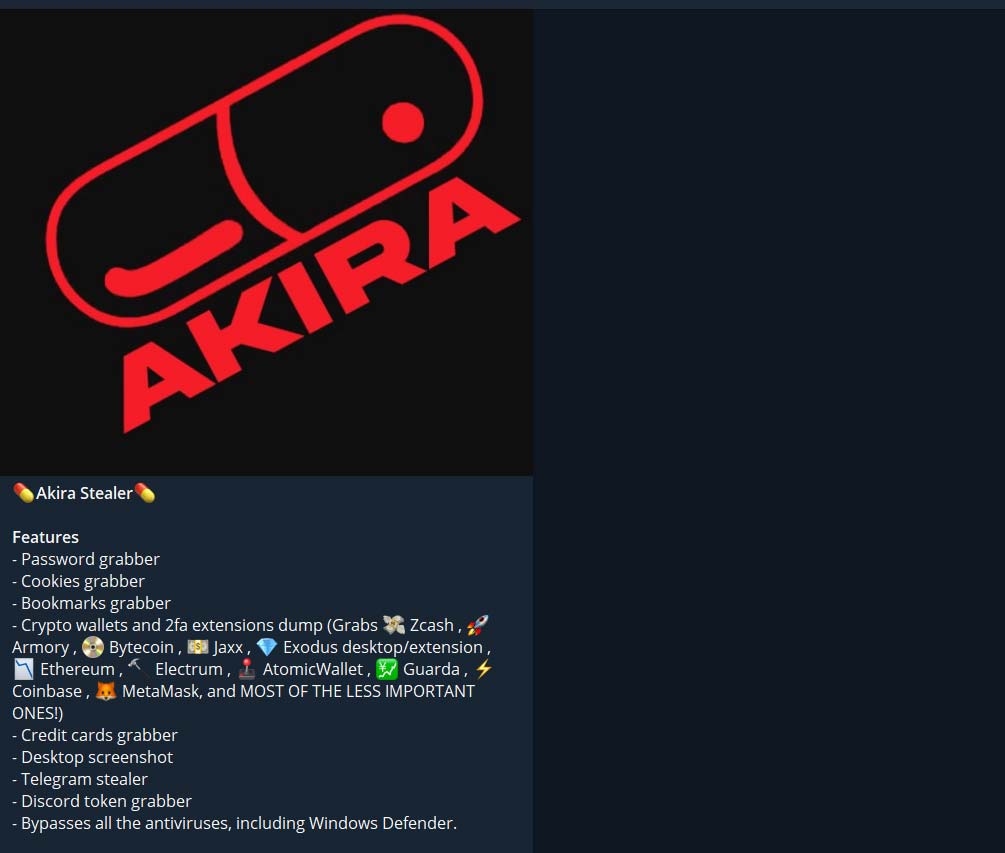
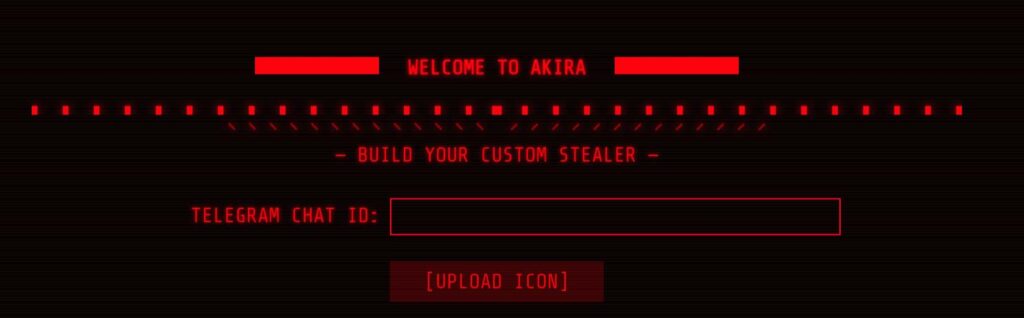
Akira Stealer has been written using Python and compiled using Pyinstaller, which is why its size is quite large. Additionally, it has very low detection on Virustotal.
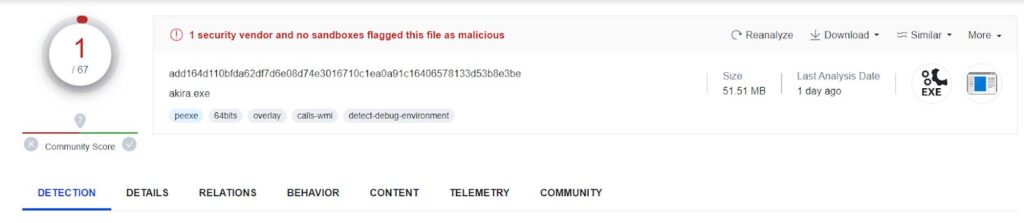
It uses Telegram as its command and control server. You can also upload the stolen data to GoFile and download it from there.