
The CyberVolk Ransomware represents a significant and evolving cyber threat, crafted by the financially motivated CyberVolk group, an Indian hacker organization linked with Russian cyber threat actors. This ransomware, which has rapidly gained notoriety in the cybersecurity community, was released as Ransomware-as-a-Service (RaaS) and demonstrated sophisticated encryption techniques, including the use of quantum-resistant algorithms. This analysis delves into the technical intricacies of CyberVolk ransomware, its unique features, and the vulnerabilities that may be exploited by cybersecurity professionals. More information is in our CyberVolk Ransomware Technical & Malware Analysis Report.
The CyberVolk group was established in March 2024 under the name GLORIAMIST India before rebranding to its current identity. It quickly aligned with Russian hacker groups, becoming part of the Holy League, a coalition targeting NATO, Ukraine, and other perceived adversaries of Russia. CyberVolk‘s activities include DDoS attacks, website defacements, data breaches, and ransomware attacks, showcasing their broad cybercriminal capabilities.
The threat actor, known by the alias Hacker-K, is of Indian origin and is the leader of the CyberVolk group.
CyberVolk ransomware first appeared on July 1, 2024, and was soon after offered as a RaaS on the dark web. Initially written in C++, ransomware uses multiple encryption algorithms, including ChaCha20-Poly1305, AES, RSA, and quantum-resistant encryption. This combination of algorithms enhances the ransomware’s resilience against decryption attempts, especially by quantum computing technologies.
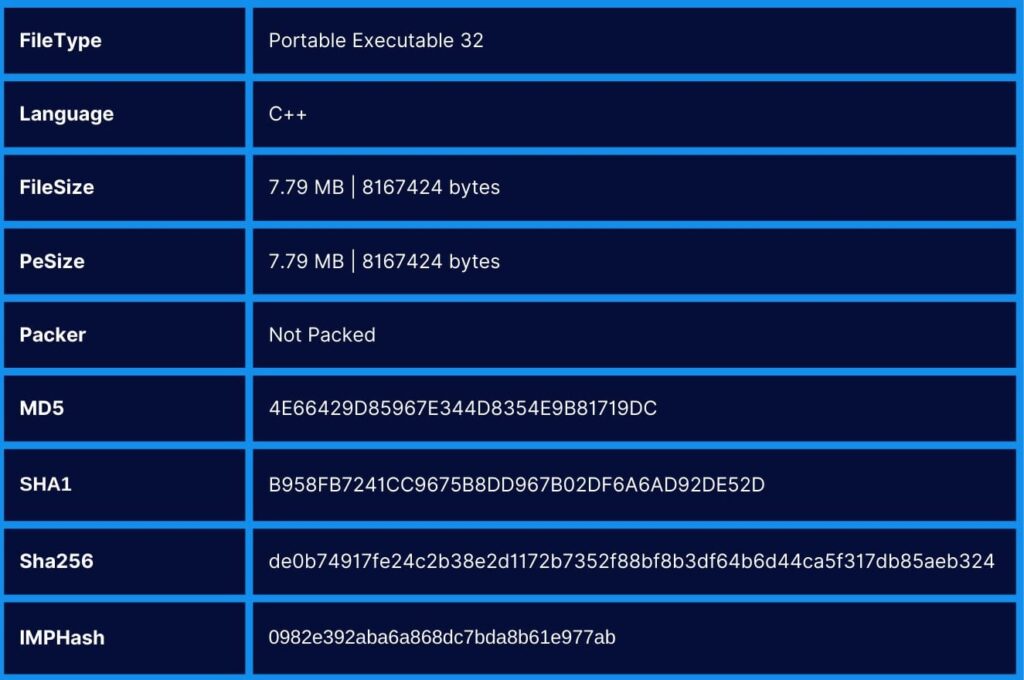
When examining the file features of the CyberVolk Ransomware, it is observed that it is developed in C++, has a size of 7.79MB, and does not use any packer.
It is observed that CyberVolk ransomware starts its process by writing a BMP file to the $HOME\\AppData\\\Temp directory. The BMP file is then set as the background image.
Then it prints the “time.dat” file to the system and starts the GUI. A time of 5 hours is specified in “time.dat” and a timer is set on the GUI according to the data written there.
After creating the time.dat file, encryption starts from the first directory of the $HOME directory. First, it creates a file with .CyberVolk extension and encrypts it by reading its contents. Then, it writes the encrypted data into the file with the.CyberVolk extension. Finally, it deletes the unencrypted file from the system.
After encrypting all files in the directory, it writes a file named CyberVolk_ReadMe.txt in the directory.
CyberVolk_ReadMe.txt
“Greetings.
All your files have been encrypted by CyberVolk ransomware.
Please never try to recover your files without decryption key which I give you after pay.
They could be disappeared?
You should follow my words.
Pay $1000 BTC to below address.
My telegram : @hacker7
Our Team : https://t.me/cubervolk
We always welcome you and your payment.”
When the process operations are monitored in the dynamic analysis, it is observed that the console “conhost.exe” for GUI support is started depending on the main process. No additional potentially harmful processes, network connections, persistence, or any other methods/techniques were detected.
the “SafeBoot” key draws attention. CyberVolk ransomware is observed to be tampering with the safe mode settings of the windows device. It is also observed that it reads dec_key.dat in the $HOME\\AppData\\\Roaming directory. The file is not created because it does not write.
the checking with the original key was examined in detail, but no such comparison was found. CyberVolk ransomware does not compare the provided decryption key to the original one.
Instead, after acquiring the key from the dec_key.dat file, it uses the WriteFile API to create an empty file with the actual name of the .CyberVolk extension file. For example, for the file file.txt.CyberVolk, it writes an empty file named file.txt on the disk. Then, using the NtWriteFile API, the decryption key is processed and the decrypted content of the encrypted file is written into file.txt. However, during this process, the buffer memory is not checked. If the provided key is incorrect, instead of writing corrupted data into the file, it writes 0-byte data. But if the provided key is correct, it writes the decrypted file content correctly since the generated data won’t be corrupted.
CyberVolk Ransomware detects whether it is running in safe mode using GetOSSafeBootMode and the SafeBoot registry key. The HideInSafeMode function is used to hide or stop certain functions when safe mode is detected.
The string “Decryption Key is Not Correct” function was analyzed due to its potential relation to the encryption key. It was found that it does not check the actual encryption key. Instead, it calculates a 36-character value. If the entered value is not exactly 36 characters, it shows the “Decryption Key is Not Correct” message and returns 0. However, if the string is 36 characters, it proceeds with decryption without validating the actual encryption key.
When it detects a 36-digit value, it is observed that it starts the decryption process. At the same time, a write operation is performed in the _fopen code structure. Here, the 36 bytes of value received as input from the user is printed on dec_key.dat, which was displayed within the dynamic analysis.
It is observed that CyberVolk Ransomware can detect debuggers with the “IsDebuggerPresent” API. If the debugger is detected, the function is terminated, but if the debugger is not detected, the program continues with the resetGlobalVariable() function.
“IsProcessorFeaturePresent” API determines whether the specific processor feature is supported by the computing environment in which it is running.
It was also observed that Ransomware accesses information related to the CPU. the CPUID instruction is utilized to distinguish between virtual and physical environments. CPUID queries the processor’s attributes and checks virtualization indicators to determine if the environment is a virtual machine.
CyberVolk Ransomware has been found to include activity similar to a worm virus. It scans all drive letters between “a” and “z.” If these drives are of the type where it can spread itself (removable, hard, network), it creates a multi-thread to execute on them. This structure has an auto-spread feature like a worm.
CyberVolk Ransomware continuously searches for the window named “TaskManagerWindow” via the “FindWindowA” API by waiting for 1 second in an infinite loop running as a different thread. When it finds it, it sends 0x0010 (WM_CLOSE) via the PostMessageW API to close the window. This prevents the user from terminating the cybervolk ransomware process via the task manager.
When the decryption process is completed, the program terminates itself using the _exit(1); function. However, since it does not involve any persistence, writing itself to a process, or utilizing any other technique/method, it does nothing else in the self-cleaning stage other than terminating itself.
Despite its sophisticated design, the ThreatMon malware team identified critical vulnerabilities within CyberVolk ransomware. One such vulnerability is the ransomware’s failure to block PowerShell, which can be used to terminate the ransomware process before it completes its encryption. CyberVolk does not employ persistence techniques, meaning it does not re-initiate after a system reboot, providing a window for defensive actions.
Moreover, the ransomware operates on a countdown timer initiated from a file name, which can be manipulated to extend the decryption window, aiding in forensic analysis. These vulnerabilities offer potential avenues for mitigation and defense against CyberVolk infections.
One of CyberVolk‘s most distinctive features is its offline operational capability. Unlike many other ransomware types that rely on a command-and-control (C2) server, CyberVolk can encrypt and decrypt data without needing a server connection, reducing the likelihood of being intercepted during the encryption process. Moreover, if an incorrect decryption key is used, the ransomware deletes the file content instead of merely returning an error, leading to irreversible data loss.
The ransomware employs a unique anti-detection mechanism. It blocks Task Manager to prevent the user from terminating its process, and it uses APIs to detect virtual environments and debugging attempts, further complicating the task for analysts trying to dissect its code.
To protect against the CyberVolk ransomware and similar threats, organizations should adopt several key practices:
CyberVolk ransomware exemplifies the evolving nature of cyber threats with its sophisticated encryption techniques and operational independence from C2 servers. However, by understanding its mechanisms and vulnerabilities, cybersecurity professionals can develop strategies to mitigate its impact. As ransomware threats continue to grow, tools like ThreatMon provide critical intelligence, helping organizations stay one step ahead of potential attacks.
Businesses looking to bolster their cybersecurity defenses should try ThreatMon’s free trial. It offers comprehensive threat detection and intelligence solutions tailored to your needs.