
The Iranian threat actor MERCURY has been exploiting unpatched Log4j 2 vulnerabilities in SysAid applications to target organizations, highlighting the critical need for timely security updates.
The Microsoft Threat Intelligence Center (MSTIC) and Microsoft 365 Defender Research Team found that Iran-based threat actor MERCURY exploited Log4j 2 vulnerabilities in SysAid applications. The threat actor targets organizations that are all based in Israel.
After gaining access, MERCURY maintains persistence, flushes credentials, and moves laterally within the targeted organization using both proprietary and well-known hacking tools and embedded operating system tools for a hands-on keyboard attack.
Microsoft assessed that MERCURY exploited remote code execution vulnerabilities in Apache Log4j 2 in vulnerable SysAid Server instances where targets are running.
According to US Cyber Command, MuddyWater, a group tracked as MERCURY, “is a subordinate element within the Iranian Ministry of Intelligence and Security.”
MERCURY was observed to exploit vulnerabilities against vulnerable SysAid Server instances as the initial access vector.
Based on observations, Microsoft says the exploits are most likely related to Log4j 2. The threat actor exploited Log4j 2 vulnerabilities against VMware applications in early 2022.
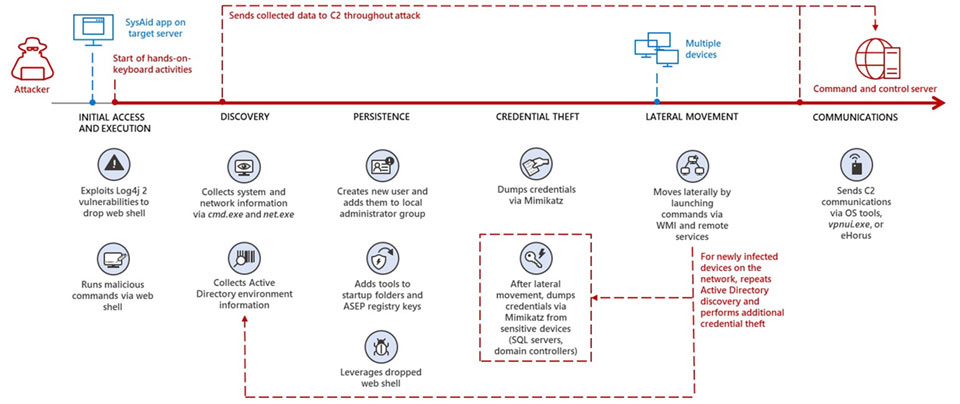
SysAid many organizations use it as an IT management tool, service desk and help desk solution. For this reason, it is a very good first access vector.
Successfully exploiting SysAid allows the threat actor to drop and use webshells to execute various commands. Adds a user, elevates their privileges to a local administrator, and then adds attack tools to their startup folders to ensure persistence across reboots.
It has been observed that MERCURY is using its foothold more and more to compromise other devices in target organizations by leveraging a variety of methods. These methods are remote services (using the RemCom tool) to use Windows Management Tools (WMI) to start commands on devices in organizations and run coded PowerShell commands in organizations.
the threat actor used embedded operating system tools such as PowerShell to communicate with the command and control (C2) server, a tunneling tool called vpnui.exe, a unique version of the open source tool Ligolo, and remote monitoring and management software eHorus.
Be sure to check if you’re within the targeting scope of the group by reviewing the report.