
Peek into Monthly Vulnerabilities: June 2024
As more and more vulnerabilities and security flaws have surfaced throughout the rapidly changing cyber landscape, the need to keep an eye on our cybersecurity has become more keenly felt than ever before.
The patching requirements of good cyber hygiene mandate that your chain is in good working order. To be effective, every security release in every security patch has to be downloaded, installed, and utilized.
The monthly security patches are one of the best discoveries against the evil adversaries. They become victims of our inattention. Bad actors can be kept at bay. The issue isn’t the difficulty, it’s the inconvenience that prevents us from doing it.
Your June 2024 vulnerability report lists tens of thousands of software vulnerabilities across hundreds of products, all of them waiting to harm you or those around you. However, as carefully as each vulnerable component is analyzed, as closely as the numbers are cross-referenced against prior incidents, these casualties of the present are employed to better safeguard the future.
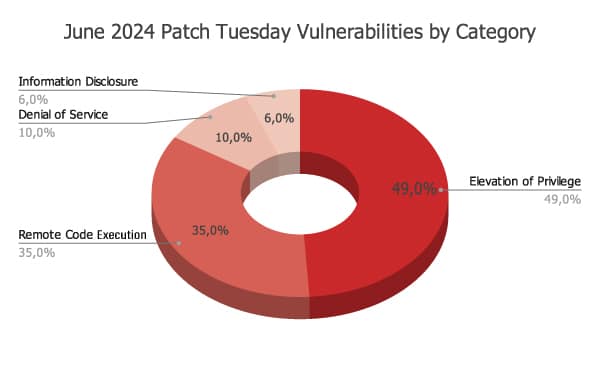
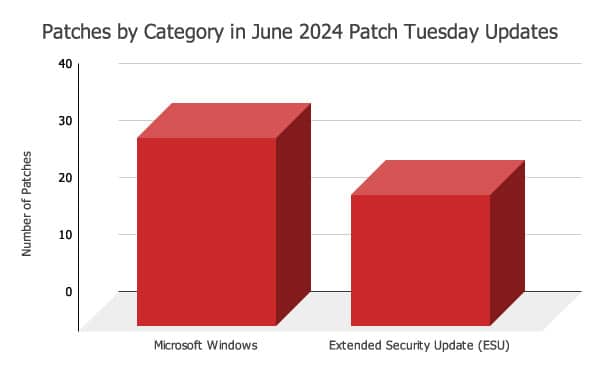
By June 2024, there were hundreds of them, ranging from low to high risk. Especially, ‘Patch Tuesday’ updates included vulnerabilities across various categories as follows:
Start your free Subscription today
Start your free Subscription today