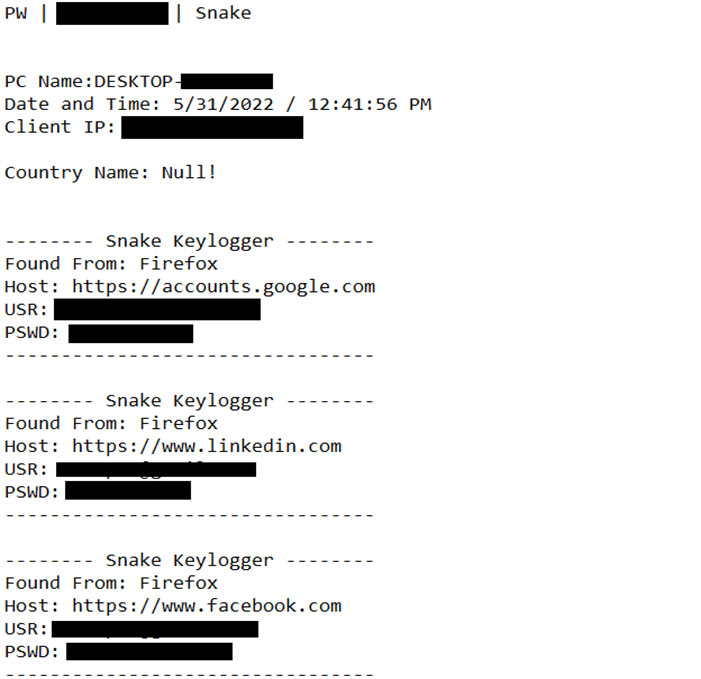
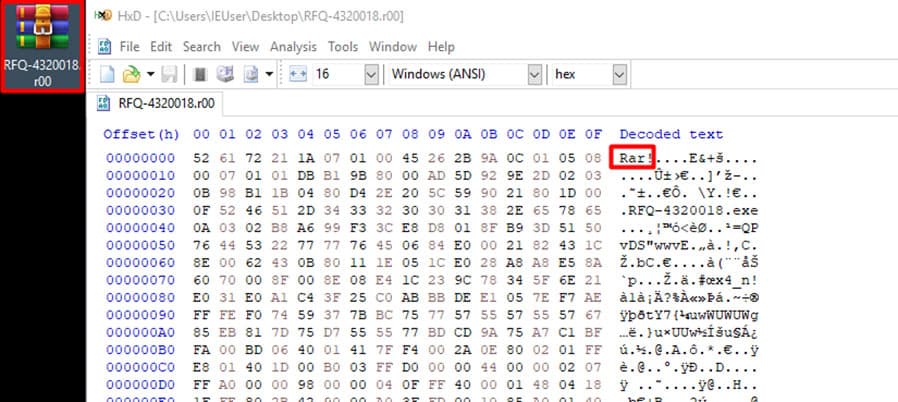
Phishing mail targeting Turkish companies has been detected. Mail attachment contains an RFQ file. Normally, a request for quotation (RFQ) is a company’s document to request pricing and packaging information from a potential supplier. This RFQ-looking file is actually a RAR file. It contains a malicious EXE file that is simply a Keylogger and Stealer. Threatmon Malware Research Team accessed the hacker’s C2 server and retrieved the stolen data.
The Stealer is using Telegram BOT API to communicate. We accessed the hacker’s C2 server and retrieved the stolen data. Here is an example: