Organizations are acting under duress. So much has changed in the digital sphere so quickly. The ever-increasing sophistication and interconnected complexity have provided attackers with a wider pool of targets to exploit, significantly raising the number of potential damage vectors compared to years gone by. Attack Surface Management has gained traction as a critical tool for mapping and managing an organization’s attack surface. It is the practice of monitoring, interrogating, identifying, and analyzing the external-facing aspects of your managed IT estate to mitigate potential cyber threats. This blog is about what tools you can use in your ASM program to reinforce your position in an increasingly adverse cyber threat landscape.
Understanding Attack Surface and Attack Surface Management
What is an Attack Surface?
An organization’s attack surface is an inventory of all the points at which its systems reach out to the world at large: the hardware, software, and network bits and pieces that are exposed to attack, perhaps because they’re misconfigured or vulnerable to a known attack ‘vector.’ An attack surface is like the attacker’s attack. It is the access point at which an adversary can enter a system and wreak havoc from within.
What is Attack Surface Management?
Attack Surface Management (ASM) comprises multiple processes and tools that help companies identify, track, and mitigate vulnerabilities within their attack surface. The overall goal of ASM is to decrease the number of points where attackers could target an organization and respond to these vulnerabilities promptly. Thus, the security team can maintain a good security posture and avoid falling victim to growing cyber threats.
What is Attack Surface Management Software?
Attack Surface Management (ASM) is a category of cybersecurity software that tries to identify, monitor, and manage an organization’s attack surface. The attack surface includes all the possible entry points, such as IP addresses, domains, software, hardware, applications, etc., that an attacker can use to gain unauthorized access to a system or network. By monitoring the attack surface continuously, the software provides the organization with a real-time view of its attackable surface, i.e., all the spots it needs to fix.
To be effective, ASM tools must offer the following features:
Asset Discovery
Advanced ASM solutions surpass basic methods like network probes by offering comprehensive, granular discovery techniques that enable organizations to thoroughly understand and effectively monitor their diverse attack surfaces. The ability to identify and assess a broad range of asset types is crucial for enhancing overall security.
Active Assessment of Vulnerabilities
ASM assesses asset vulnerabilities through passive enumeration and active confirmation methods, with active assessments emulating attacker techniques for a more thorough evaluation. The effectiveness of an ASM solution largely depends on its capability for active vulnerability assessment, which is crucial for a comprehensive security analysis.
Internal ASM
Emerging technologies are making internal environments as dynamic and challenging as external attack surfaces, leading to the evolution of ASM solutions to cover both areas. Comprehensive ASM practices offer a unified approach to managing vulnerabilities and threats across the entire attack surface, enhancing overall security strategy.
Risk Scoring
Advanced ASM solutions enhance risk assessment by integrating contextual metadata, open source intelligence (OSINT), and active assessment data, leading to more accurate and efficient risk management. The incorporation of comprehensive context into risk scoring and the automation of response workflows based on these scores significantly streamline security operations.
Asset Categorization
Effective ASM hinges on logically grouping diverse assets, a process enhanced by detailed asset categorization, which allows for simplified risk assessment and efficient management. Unlike basic network scans, advanced ASM solutions provide in-depth insights, driving more precise asset categorization and enabling more accurate risk management based on specific customer needs.
Who Uses Attack Surface Management Software?
ASM software is utilized by a variety of stakeholders within an organization, including:
- Cybersecurity Teams: Using ASM software, these pros identify and neutralize vulnerabilities before bad actors can take advantage of them.
- Information Technology departments: IT teams use ASM to keep an accurate, secure, and up-to-date list of all digital assets, thereby enforcing compliance with security policies.
- Risk Management Pros: ASM helps you determine which elements of the attack surface have higher risks and which ones are low priorities for remediation so you can focus on remediating accordingly.
- Chief Information Security Officer (CISO): CISOs use ASM to manage their cyber security efforts at a strategic level to keep the organization’s security posture aligned with the risk appetite and regulatory constraints.
- Penetration Testers and Red Teams: These groups use ASM tools to simulate attacks and test the strength of the security controls applied.
Important Features of Attack Surface Management Software
- Continuous Discovery and Monitoring: There is no longer need for people to perform discoveries or assessments of assets in an organisation. ASM works efficiently and in real-time to monitor attack profile activities of new and existing assets as they are discovered.
- Vulnerability Assessment: The software identifies which assets are vulnerable, giving organizations key insight into where to focus their remediation efforts based on the degree of risk.
- Digital Asset Inventory: It keeps an up-to-date listing of utility-bearing digital resources and assets for home, hardware, software, cloud, third-party integrations, and more.
- Risk Scoring: Many ASM tools provide risk-scoring capabilities to help organizations prioritize vulnerabilities first based on their anticipated level of impact.
- Risk Reduction: ASM tools typically help to reduce risk by providing organizations with information on which vulnerabilities to address first.
- Ability to Integrate with Other Security Tools: The best ASM software integrates with security tools such as SIEM (security information and event management) systems, vulnerability scanners, and threat intelligence platforms, providing a holistic security position.
- Alerting and Reporting: Identify new vulnerabilities, configuration changes, OS or application updates, potential compromises, security events, and more. Automated reporting for compliance and management review.
- Remediation Advice: Actionable insights and guidance on how to remediate discovered vulnerabilities can often be provided by ASM solutions.
- Compliance support: By use of the software, compliance with various regulatory requirements can be facilitated by the organization through continuous monitoring and reporting on its activities.
So ASM software is far more likely to detect a malicious cyberattack than if the enterprise were using a small bodyguard squad of human experts. This would give the enterprise a much better chance of averting the incident and reducing its risk exposure.
Protecting Your Attack Surface
To effectively protect your attack surface, organizations should:
- Implement Continuous Monitoring: Regularly scan and monitor all assets to detect vulnerabilities promptly.
- Perform Periodic Audits: Take stringent measures when it comes to identifying existing or potential vulnerabilities and improvement opportunities.
- Train Employees: Make sure the staff or those who use the Wi-Fi network know about the security best practices and keep themselves informed on the same mission to safeguard the organization.
- Employ Sophisticated ASM Tools: Perform vulnerability hunting and fixes using automated ASM technology.
Top 10 Tools for Effective Attack Surface Management
1. Rapid7 InsightVM
Rapid7 InsightVM is a powerful vulnerability management solution that provides comprehensive visibility and actionable insights into an organization’s security posture. Built on the Rapid7 Insight platform, InsightVM leverages advanced analytics and automation to help organizations identify, prioritize, and remediate vulnerabilities across their IT environments. This tool integrates seamlessly with various IT and security operations tools, making it a versatile and essential component of a robust cybersecurity strategy.
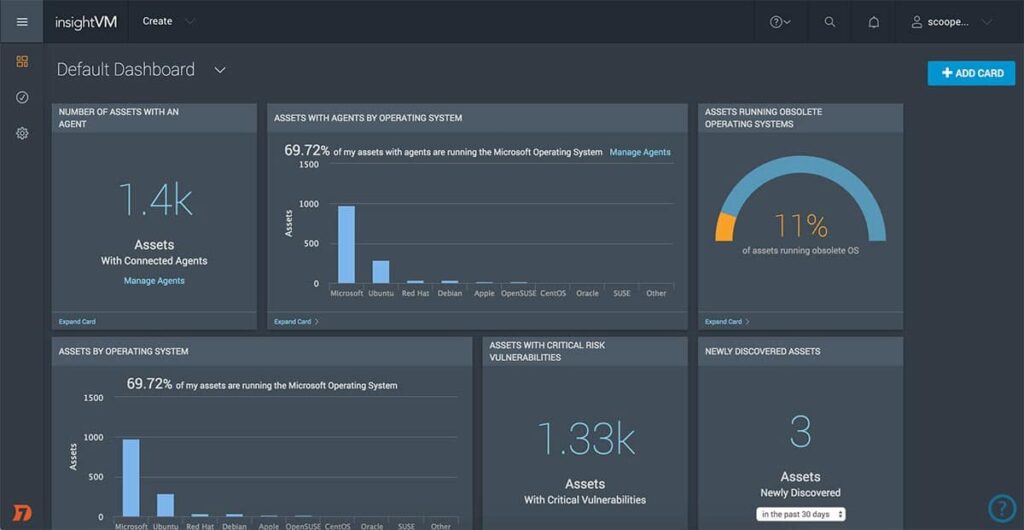
Key Features:
- Live Dashboards and Detailed Reporting: InsightVM offers customizable live dashboards that provide real-time visibility into the organization’s security posture. The detailed reporting features allow security teams to generate comprehensive reports for stakeholders, ensuring transparency and informed decision-making.
- Dynamic Asset Discovery and Inventory: Automatically discovers and inventories all assets within the organization’s network, including on-premises, cloud, and hybrid environments. This dynamic discovery process ensures that no asset is overlooked.
- Advanced Vulnerability Assessment: Utilizes a combination of agent-based and agentless scanning techniques to identify vulnerabilities across various asset types, including endpoints, servers, and network devices.
- Risk Prioritization: InsightVM employs advanced risk-scoring algorithms that take into account the exploitability and impact of vulnerabilities, helping organizations prioritize remediation efforts based on risk.
- Automated Remediation Workflows: Integrates with IT service management (ITSM) tools to automate the creation and tracking of remediation tickets. This automation streamlines the remediation process, reducing the time required to address critical vulnerabilities.
- Integration with IT and Security Tools: Seamlessly integrates with a wide range of IT and security operations tools, including SIEM, SOAR, and ticketing systems, enhancing the overall efficiency of security operations.
Pros:
- Comprehensive Visibility: Provides extensive visibility into the entire IT environment, ensuring that all assets and vulnerabilities are accounted for.
- Real-Time Insights: Live dashboards and real-time data provide up-to-date information, enabling prompt and informed decision-making.
- Effective Risk Prioritization: Advanced risk scoring helps organizations focus on the most critical vulnerabilities, optimizing the use of resources.
- Automation and Integration: Automated workflows and seamless integration with other tools improve the efficiency and effectiveness of vulnerability management processes.
- User-Friendly Interface: The intuitive interface and customizable dashboards make it easy for security teams to navigate and utilize the platform effectively.
Cons:
- Cost: The comprehensive features and capabilities come at a premium price, which may be prohibitive for smaller organizations with limited budgets.
- Resource Intensive: The initial setup and ongoing management of the platform can be resource-intensive, requiring skilled personnel.
- Learning Curve: New users may experience a steep learning curve due to the platform’s extensive features and functionalities.
Rapid7 InsightVM is a comprehensive and versatile vulnerability management solution that offers extensive visibility and actionable insights into an organization’s security posture. Its advanced features, including dynamic asset discovery, risk prioritization, and automated remediation workflows, make it an essential tool for organizations seeking to enhance their vulnerability management processes. However, the platform’s cost and resource requirements should be carefully considered, especially by smaller organizations.
2. CrowdStrike Falcon Surface
CrowdStrike Falcon Surface is an advanced Attack Surface Management (ASM) solution designed to help organizations gain comprehensive visibility into their external digital footprint. Part of the broader CrowdStrike Falcon platform, Falcon Surface leverages CrowdStrike’s extensive threat intelligence and expertise to identify, monitor, and manage exposed assets. This tool provides continuous discovery and assessment of internet-facing assets, ensuring that organizations can proactively address vulnerabilities and mitigate potential threats.
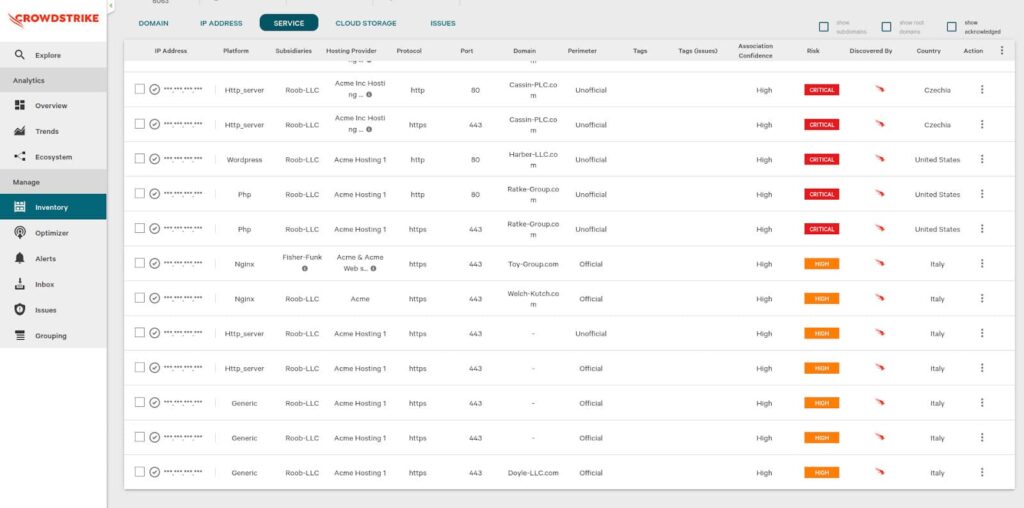
Key Features:
- Continuous Asset Discovery: Automatically discovers all internet-facing assets associated with an organization, including those that may be unknown or unmanaged, such as shadow IT.
- Risk-Based Prioritization: Uses advanced risk scoring algorithms to evaluate the severity and potential impact of vulnerabilities, helping organizations prioritize remediation efforts based on risk.
- Threat Intelligence Integration: Integrates with CrowdStrike’s comprehensive threat intelligence to provide context-aware insights into vulnerabilities and potential threats.
- Automated Monitoring and Alerts: Continuously monitors the attack surface for changes and new vulnerabilities, providing real-time alerts to security teams for prompt action.
- Detailed Reporting and Dashboards: Offers customizable dashboards and detailed reports that provide visibility into the organization’s security posture, trends, and remediation progress.
Pros:
- Comprehensive Visibility: Provides extensive visibility into the external digital footprint, ensuring that all exposed assets are identified and monitored.
- Proactive Threat Management: Continuous monitoring and real-time alerts enable proactive management of vulnerabilities and threats.
- Context-Aware Insights: Integration with CrowdStrike’s threat intelligence offers valuable context, improving the accuracy of risk assessments and prioritization.
- User-Friendly Interface: Intuitive dashboards and detailed reporting make it easy for security teams to navigate and utilize the platform effectively.
Cons:
- Cost: The comprehensive features and capabilities come at a premium price, which may be prohibitive for smaller organizations with limited budgets.
- Resource Intensive: The initial setup and ongoing management of the platform can be resource-intensive, requiring skilled personnel.
- Learning Curve: New users may experience a steep learning curve due to the platform’s extensive features and functionalities.
CrowdStrike Falcon Surface is a powerful ASM solution that offers extensive visibility and proactive threat management capabilities for organizations. By leveraging advanced asset discovery, risk-based prioritization, and integration with CrowdStrike’s threat intelligence, Falcon Surface provides a comprehensive approach to managing and securing the attack surface. However, the platform’s cost and resource requirements should be carefully considered, especially by smaller organizations.
3. Microsoft Defender External Attack Surface Management
Microsoft Defender External Attack Surface Management (EASM) is a comprehensive solution designed to help organizations identify, monitor, and manage their external digital assets. Part of the Microsoft Defender suite, this tool offers continuous discovery and assessment of internet-facing assets, helping organizations mitigate risks and enhance their security posture. Leveraging Microsoft’s extensive cloud infrastructure and security expertise, Defender EASM provides organizations with the tools needed to proactively manage their attack surface.
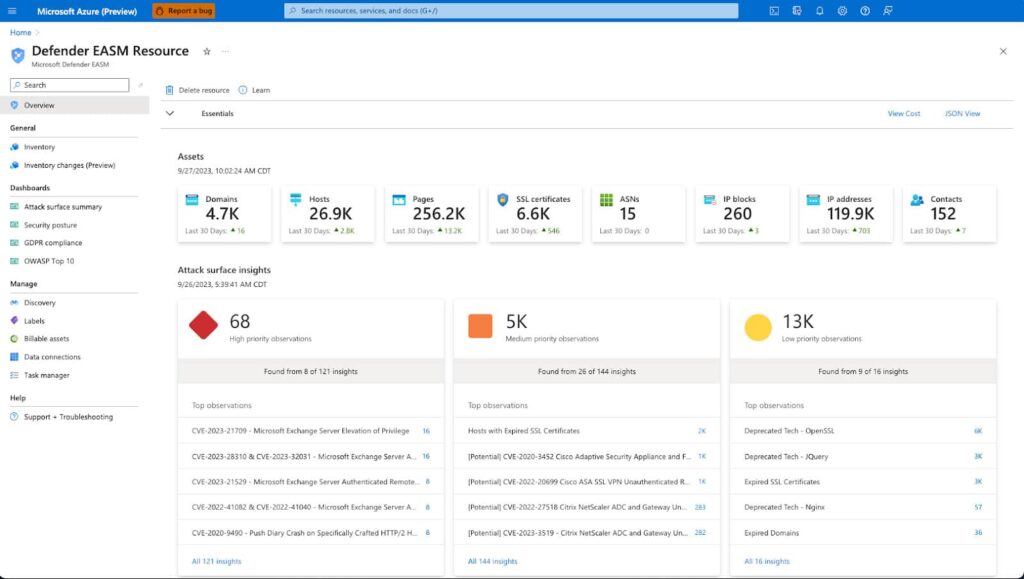
Key Features:
- Continuous Asset Discovery: Automatically scans and identifies all external-facing assets associated with an organization, including shadow IT and unmanaged assets.
- Risk-Based Prioritization: Evaluates the severity and potential impact of vulnerabilities, providing prioritized remediation recommendations based on risk.
- Integration with Microsoft Threat Intelligence: Utilizes Microsoft’s vast threat intelligence network to provide context-aware insights into vulnerabilities and potential threats.
- Automated Monitoring and Alerts: Offers continuous monitoring of the external attack surface, with real-time alerts to notify security teams of new vulnerabilities or changes.
- Comprehensive Reporting and Dashboards: Provides detailed reports and customizable dashboards to track the organization’s security posture, remediation efforts, and trends over time.
Pros:
- Extensive Visibility: Provides comprehensive visibility into all external-facing assets, ensuring that no vulnerabilities are overlooked.
- Proactive Risk Management: Continuous monitoring and real-time alerts enable proactive management of vulnerabilities and threats.
- Context-Aware Insights: Integration with Microsoft’s threat intelligence offers valuable context, enhancing the accuracy of risk assessments and prioritization.
- Seamless Integration: Integrates well with other Microsoft security tools and services, providing a unified security approach.
Cons:
- Complexity: Initial setup and configuration can be complex, requiring significant effort and expertise.
- Cost: The premium features and capabilities may be cost-prohibitive for smaller organizations with limited budgets.
- Learning Curve: Users may experience a steep learning curve due to the extensive features and functionalities offered by the platform.
Microsoft Defender External Attack Surface Management is a powerful ASM solution that leverages Microsoft’s extensive cloud and security expertise to provide comprehensive visibility and proactive threat management for organizations. Its advanced features, including continuous asset discovery, risk-based prioritization, and integration with Microsoft’s threat intelligence, make it an essential tool for enhancing security posture.
4. Palo Alto Cortex Xpanse
Palo Alto Networks’ Cortex Xpanse is a robust ASM tool designed to help organizations manage and secure their digital assets. It provides a comprehensive view of an organization’s attack surface by continuously discovering and assessing all internet-facing assets.
Key Features:
- Automated Asset Discovery: Continuously scans the internet to identify all assets associated with an organization, including shadow IT and cloud resources.
- Risk Assessment: Evaluate the security posture of discovered assets, identifying vulnerabilities, misconfigurations, and compliance issues.
- Threat Intelligence Integration: Incorporates threat intelligence to prioritize risks based on the likelihood of exploitation and potential impact.
- Incident Response: Provides actionable insights and remediation guidance to address identified vulnerabilities and mitigate risks.
- Comprehensive Reporting: Offers detailed dashboards and reports to track the organization’s security posture and improvements over time.
Pros:
- Comprehensive Visibility: Automatically discovers all assets, including those that may be unknown to IT and security teams, providing a complete view of the attack surface.
- Proactive Risk Management: Identifies and prioritizes vulnerabilities, allowing organizations to focus on the most critical risks.
- Ease of Integration: Seamlessly integrates with other Palo Alto Networks’ security products and third-party tools, enhancing overall security operations.
- Scalability: Suitable for organizations of all sizes, from small businesses to large enterprises.
Cons:
- Complex Setup: Initial deployment and configuration can be complex and time-consuming, requiring skilled personnel.
- Cost: Premium pricing may be a barrier for smaller organizations with limited budgets.
- Learning Curve: Users may need extensive training to fully utilize all features and capabilities.
Palo Alto Cortex Xpanse stands out for its ability to provide comprehensive visibility and proactive risk management across an organization’s digital assets. Its integration capabilities and detailed threat intelligence make it a valuable tool for organizations looking to strengthen their security posture. However, the complexity and cost may require careful consideration, particularly for smaller businesses.
5. Recorded Future
Recorded Future is a comprehensive threat intelligence platform that provides organizations with real-time insights into emerging threats and vulnerabilities. Leveraging advanced analytics and machine learning, Recorded Future aggregates and analyzes data from a wide range of sources to deliver actionable intelligence. This tool helps security teams proactively identify and mitigate risks, enhancing their overall security posture.
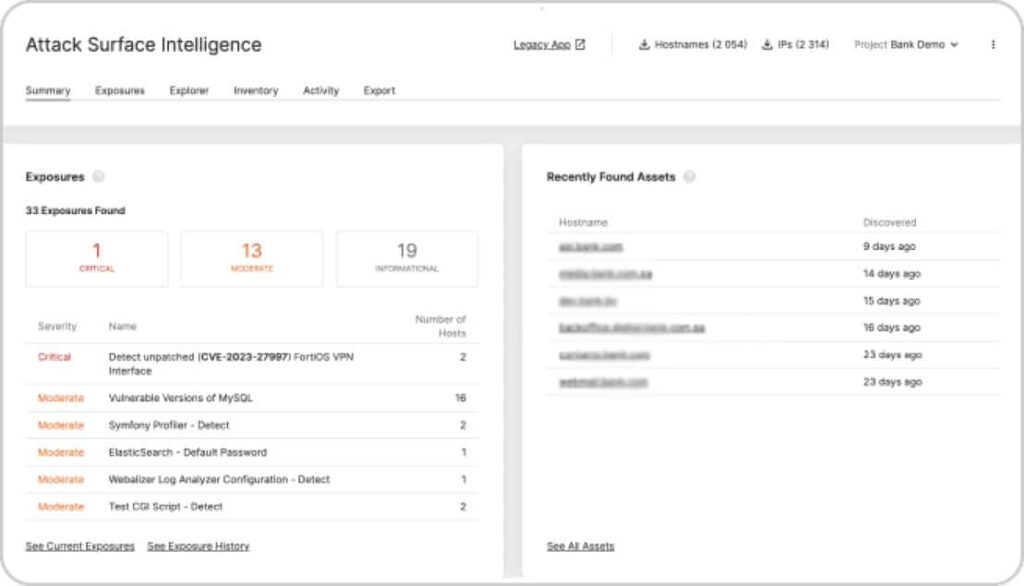
Key Features:
- Threat Intelligence Integration: Aggregates data from a vast array of sources, including open, dark, and technical web data, to provide comprehensive threat intelligence.
- Real-Time Monitoring and Alerts: Continuously monitors for new threats and vulnerabilities, providing real-time alerts to security teams.
- Risk-Based Prioritization: Uses advanced risk-scoring algorithms to prioritize threats based on their severity, potential impact, and likelihood of exploitation.
- Automated Analysis: Employs machine learning and natural language processing to analyze threat data, providing context-aware insights and actionable recommendations.
- Detailed Reporting and Dashboards: Offers customizable dashboards and detailed reports to help organizations track threat trends and monitor their security posture.
Pros:
- Extensive Threat Intelligence: Provides access to a vast range of threat data sources, ensuring comprehensive visibility into the threat landscape.
- Proactive Risk Management: Real-time monitoring and automated analysis enable proactive identification and mitigation of threats.
- Context-Aware Insights: Advanced analytics provide context to threats, enhancing the accuracy of risk assessments and prioritization.
- User-Friendly Interface: Intuitive dashboards and detailed reporting make it easy for security teams to navigate and utilize the platform effectively.
Cons:
- Cost: The extensive features and capabilities come at a premium price, which may be prohibitive for smaller organizations with limited budgets.
- Complexity: The initial setup and integration with existing systems can be complex, requiring significant effort and expertise.
- Learning Curve: New users may experience a steep learning curve due to the platform’s extensive features and functionalities.
Recorded Future is a powerful threat intelligence platform that provides organizations with real-time, actionable insights into emerging threats and vulnerabilities. Its comprehensive data aggregation, advanced analytics, and machine learning capabilities make it an essential tool for proactive risk management and enhanced security posture. However, the complexity and cost of the platform should be carefully considered, especially by smaller organizations.
6. ImmuniWeb
ImmuniWeb is a comprehensive application security platform that offers continuous web application scanning and threat detection for web applications and APIs. The platform integrates with CI/CD pipelines to provide real-time insights and actionable recommendations, ensuring that security is embedded throughout the software development lifecycle. ImmuniWeb leverages a combination of AI technology and expert analysis to deliver high-quality vulnerability assessments, compliance checks, and threat intelligence.
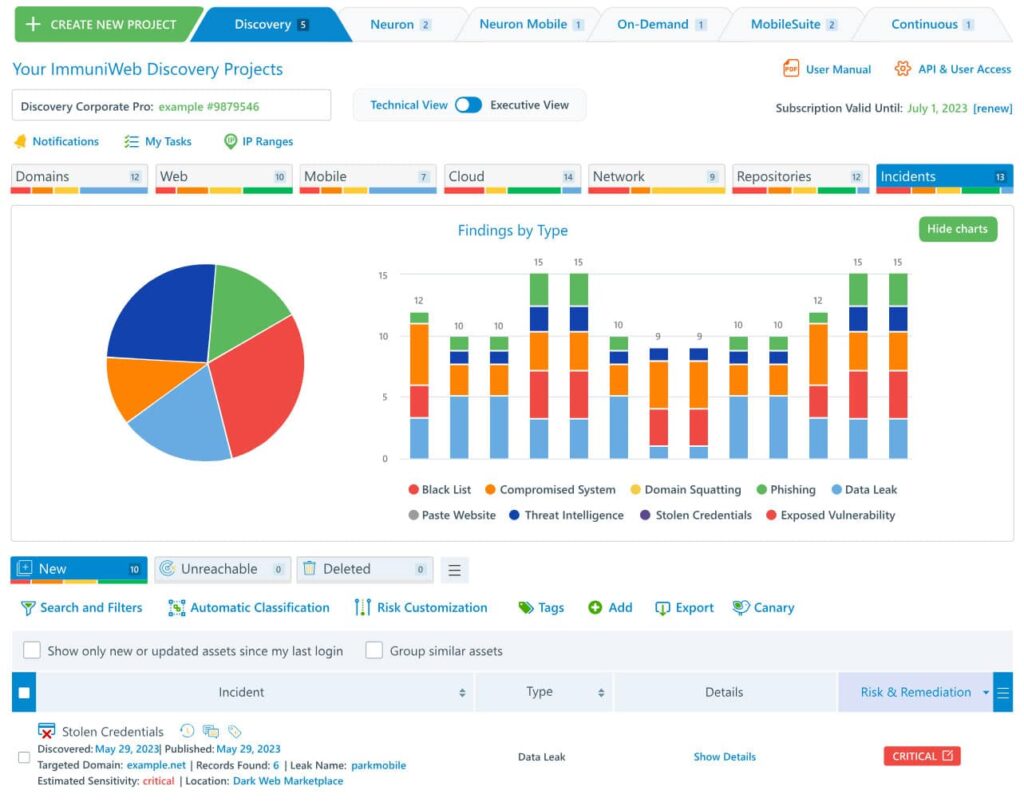
Key Features:
- Continuous Web Application Scanning: Automatically scans web applications and APIs for vulnerabilities, providing continuous assessment and monitoring.
- AI-Powered Vulnerability Assessment: Utilizes advanced AI technology to identify and prioritize vulnerabilities, offering detailed insights and recommendations.
- Integration with CI/CD Pipelines: Seamlessly integrates with development workflows to provide real-time security feedback during the development and deployment processes.
- Compliance Checks: Conducts comprehensive compliance assessments to ensure adherence to standards such as GDPR, PCI DSS, HIPAA, and more.
- Detailed Reporting and Analytics: Offers in-depth reports and analytics, enabling organizations to track security trends, remediation progress, and overall security posture.
Pros:
- Advanced AI Technology: Leverages cutting-edge AI to enhance the accuracy and efficiency of vulnerability assessments.
- Seamless CI/CD Integration: Provides real-time security feedback within development workflows, promoting a DevSecOps approach.
- Comprehensive Compliance Coverage: Ensures compliance with various regulatory standards, helping organizations avoid legal and financial penalties.
- Expert Analysis: Combines automated scanning with expert analysis to deliver high-quality, actionable insights.
Cons:
- Cost: The advanced features and capabilities come at a premium price, which may be prohibitive for smaller organizations with limited budgets.
- Resource Requirements: Continuous monitoring and integration with CI/CD pipelines may require significant resources and coordination with development teams.
- Complexity: The initial setup and configuration can be complex, requiring skilled personnel to manage effectively.
ImmuniWeb is a powerful application security platform that provides comprehensive vulnerability assessments and compliance checks for web applications and APIs. Its advanced AI technology and seamless integration with CI/CD pipelines make it an essential tool for organizations looking to embed security throughout the software development lifecycle. However, the complexity and cost of the platform should be carefully considered, especially by smaller organizations.
7. CyCognito
CyCognito provides an innovative Attack Surface Management (ASM) platform designed to uncover and manage risks across an organization’s external digital footprint. Leveraging advanced reconnaissance techniques and comprehensive analysis, CyCognito identifies assets and vulnerabilities that are often missed by traditional security tools. Its platform is built to provide continuous monitoring and risk assessment, helping organizations proactively manage their security posture.
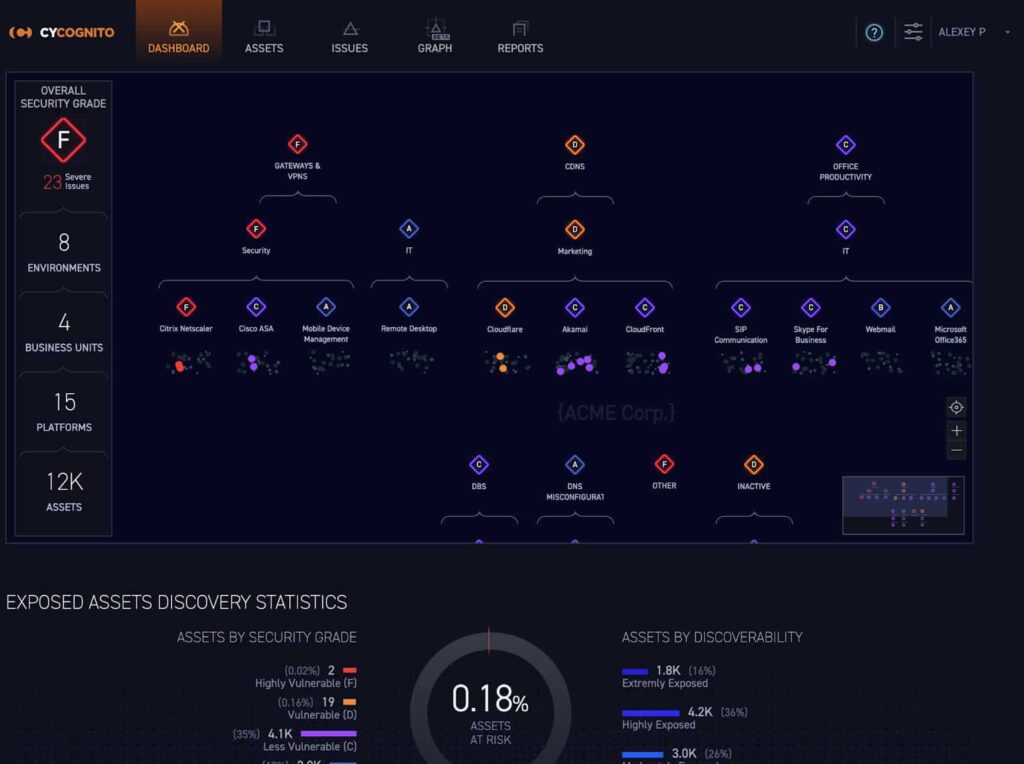
Key Features:
- Automated Asset Discovery: Continuously scans and discovers all external-facing assets, including those that are unknown, unmanaged, or overlooked, providing a complete view of the attack surface.
- Comprehensive Risk Assessment: Evaluates discovered assets for vulnerabilities and misconfigurations, using both passive and active assessment methods to ensure thorough analysis.
- Prioritized Remediation: Utilizes advanced risk scoring to prioritize vulnerabilities based on their potential impact and exploitability, guiding organizations in efficient remediation efforts.
- Threat Intelligence Integration: Incorporates threat intelligence to provide context-aware insights, enhancing the accuracy and relevance of risk assessments.
- Detailed Reporting and Dashboards: Offers interactive dashboards and detailed reports that provide visibility into the organization’s security posture, vulnerability trends, and remediation progress.
Pros:
- Extensive Visibility: Provides a thorough and comprehensive view of the external attack surface, identifying assets that might otherwise go unnoticed.
- Proactive Risk Management: Continuous monitoring and advanced risk assessment help organizations stay ahead of potential threats.
- Actionable Insights: Detailed risk scoring and prioritized remediation recommendations facilitate efficient vulnerability management.
- User-Friendly Interface: Intuitive dashboards and comprehensive reports make it easy for security teams to understand and act on findings.
Cons:
- Cost: The premium features and extensive capabilities may come at a high price, which could be a barrier for smaller organizations with limited budgets.
- Complex Setup: Initial deployment and configuration can be complex, requiring significant expertise and effort.
- Resource Intensive: Continuous monitoring and comprehensive analysis may demand substantial resources and coordination with security and IT teams.
CyCognito offers a powerful ASM solution that excels in providing extensive visibility and proactive risk management for an organization’s external digital footprint. Its advanced asset discovery and comprehensive risk assessment capabilities make it a valuable tool for enhancing security posture. However, the complexity and cost associated with the platform should be carefully considered, especially by smaller organizations.
8. Bugcrowd’s Attack Surface Management (ASM)
It is designed to provide comprehensive visibility and continuous monitoring of an organization’s digital assets. This platform leverages Bugcrowd’s extensive network of security researchers to identify, assess, and manage vulnerabilities across a wide range of assets.
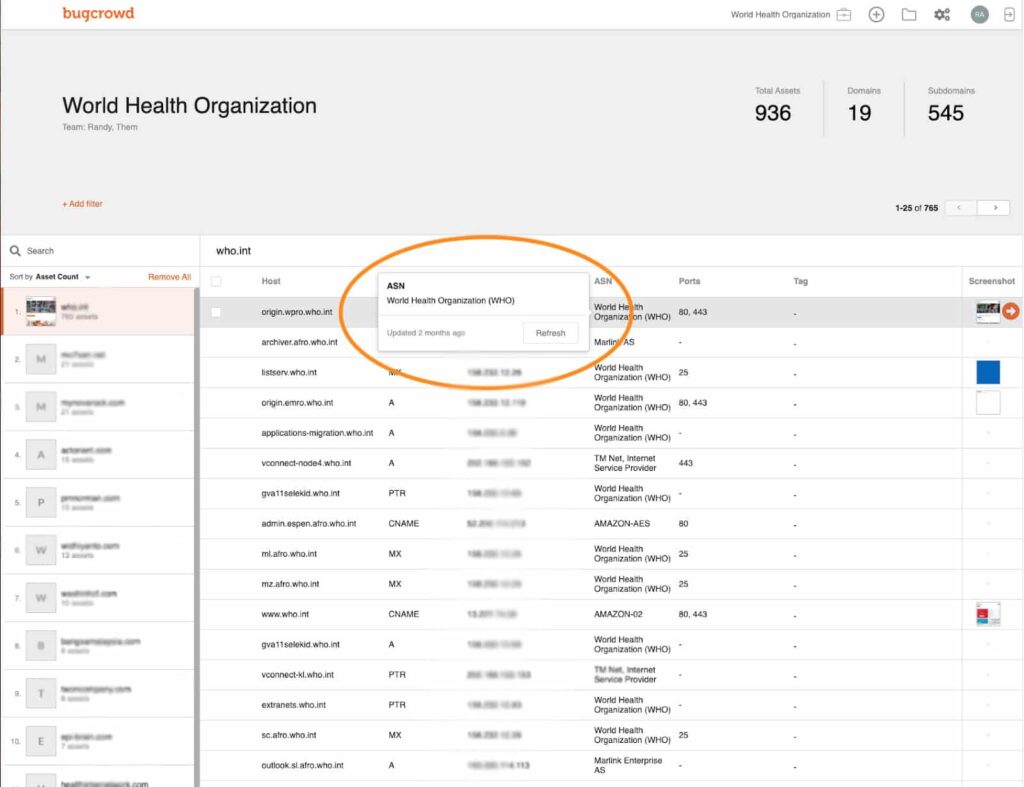
Key Features:
- Crowdsourced Security Insights: Utilizes a global network of security researchers to discover vulnerabilities and provide continuous monitoring.
- Comprehensive Asset Discovery: Automatically identifies and inventories all internet-facing assets, including shadow IT and cloud services.
- Vulnerability Detection: Actively assesses discovered assets for vulnerabilities using both automated tools and manual testing by expert researchers.
- Risk Prioritization: Assigns risk scores to vulnerabilities based on their severity, potential impact, and exploitability, helping organizations prioritize remediation efforts.
- Detailed Reporting and Analytics: Provides comprehensive reports and dashboards to track the organization’s security posture, vulnerability trends, and remediation progress.
Pros:
- Access to Expert Researchers: Benefits from Bugcrowd’s vast network of security experts, enhancing the depth and accuracy of vulnerability assessments.
- Continuous Monitoring: Offers ongoing surveillance of the attack surface, ensuring real-time detection and mitigation of new threats.
- High-Quality Insights: Combines automated scanning with human intelligence, resulting in high-quality, actionable insights and recommendations.
- User-Friendly Interface: Intuitive dashboards and detailed reports make it easy for security teams to understand and act on findings.
Cons:
- Complex Setup: Initial configuration and integration with existing systems can be complex and time-consuming.
- Cost: The premium nature of the service may be cost-prohibitive for smaller organizations with limited budgets.
- Resource Requirements: Continuous engagement with the platform and researchers may require significant resources and coordination.
Bugcrowd’s Attack Surface Management solution stands out for its innovative use of crowdsourced security research combined with automated tools. This approach ensures comprehensive coverage and high-quality vulnerability detection, making it a valuable tool for organizations looking to enhance their security posture. However, the complexity of setup and potential costs should be carefully considered, especially by smaller organizations.
9. Bishop Fox Cosmos
Bishop Fox’s Cosmos is an advanced Attack Surface Management (ASM) platform designed to provide continuous monitoring, comprehensive visibility, and actionable insights into an organization’s digital assets. Cosmos combines automated scanning with expert analysis to uncover and address vulnerabilities in real time.
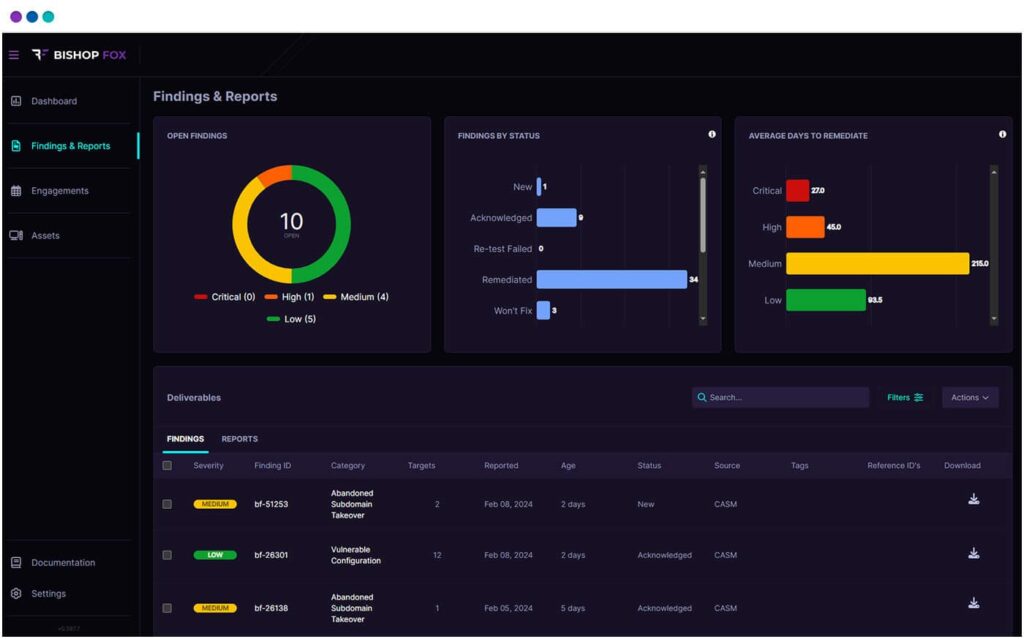
Key Features:
- Automated Asset Discovery: Continuously identifies and catalogs all internet-facing assets, including shadow IT and third-party services.
- Expert Analysis: Pairs automated findings with manual assessments by security experts to ensure thorough risk identification and validation.
- Real-Time Risk Assessment: Evaluates and prioritizes risks based on the severity and potential impact of vulnerabilities.
- Continuous Monitoring: Provides ongoing surveillance of the attack surface, alerting organizations to new vulnerabilities and changes in asset status.
- Detailed Reporting and Dashboards: Offers comprehensive reports and interactive dashboards to help organizations track their security posture and make informed decisions.
Pros:
- Combination of Automation and Expertise: Integrates automated scanning with expert analysis, ensuring high accuracy and thoroughness in vulnerability detection.
- Proactive Risk Management: Continuously monitors and assesses risks, enabling organizations to address vulnerabilities before they can be exploited.
- User-Friendly Interface: Intuitive dashboards and detailed reports make it easy for security teams to understand and act on findings.
- Scalability: Effective for organizations of all sizes, from small businesses to large enterprises, providing tailored solutions to meet specific needs.
Cons:
- Initial Setup Complexity: The deployment and initial configuration can be complex, requiring significant effort and expertise.
- Premium Pricing: The cost of the platform may be high for smaller organizations or those with limited cybersecurity budgets.
- Resource Intensive: Continuous monitoring and expert analysis can require substantial resources and coordination with in-house security teams.
Bishop Fox Cosmos offers a powerful ASM solution by combining automated asset discovery with expert analysis. This dual approach ensures comprehensive coverage and accurate identification of vulnerabilities, making it an excellent choice for organizations seeking to enhance their security posture. However, the complexity of setup and premium pricing may necessitate careful consideration, especially for smaller organizations.
10.ThreatMon
ThreatMon is a comprehensive Attack Surface Management (ASM) platform that provides continuous monitoring, proactive threat detection, and in-depth vulnerability assessment. Designed to integrate seamlessly with existing security infrastructure, ThreatMon offers organizations a real-time view of their attack surface, helping them identify, prioritize, and mitigate potential security threats. Its advanced capabilities make it a valuable tool for enhancing an organization’s overall security posture.
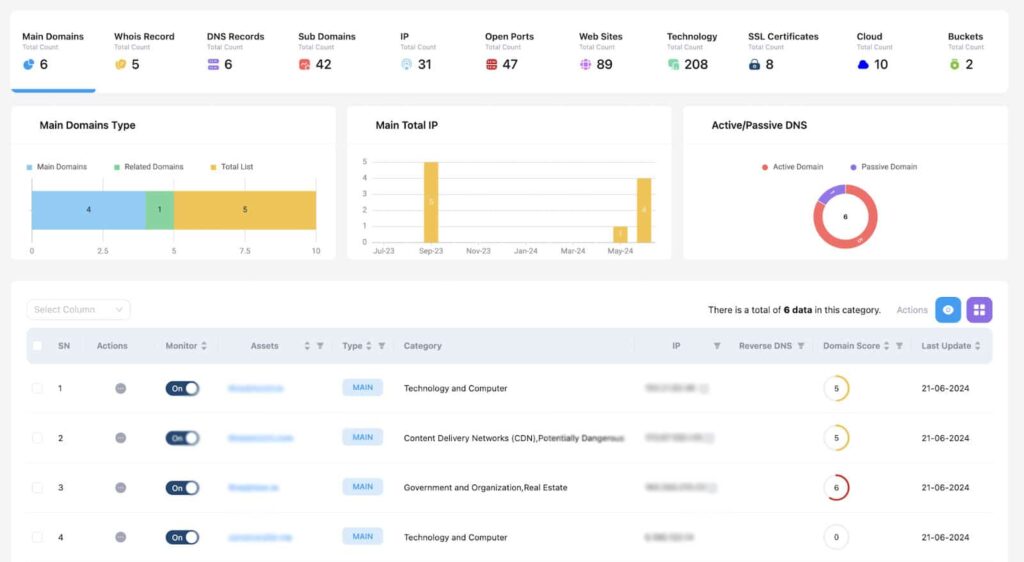
Key Features:
- Continuous Monitoring: Offers 24/7 monitoring of digital assets to detect vulnerabilities and potential threats in real time.
- Automated Threat Detection: Utilizes advanced algorithms and threat intelligence to automatically identify and alert potential security issues.
- Vulnerability Assessment: Conducts thorough vulnerability assessments across all assets, including on-premises, cloud, and hybrid environments.
- Risk Prioritization: Uses sophisticated risk-scoring algorithms to prioritize vulnerabilities based on severity and potential impact, enabling efficient remediation.
- Integration with Security Tools: Seamlessly integrates with SIEM, SOAR, and other security tools, providing a unified approach to security management.
- Detailed Reporting and Analytics: Provides comprehensive reports and interactive dashboards that offer insights into security posture, vulnerability trends, and remediation progress.
Pros:
- Real-Time Visibility: Provides continuous, real-time visibility into the attack surface, ensuring timely identification and mitigation of vulnerabilities.
- Proactive Threat Management: Automated threat detection and risk prioritization help organizations stay ahead of potential threats.
- Seamless Integration: Integrates well with existing security tools, enhancing the overall efficiency of security operations.
- User-Friendly Interface: Intuitive dashboards and detailed reporting make it easy for security teams to understand and act on findings.
Cons:
- Resource Intensive: Continuous monitoring and detailed analysis may demand substantial resources and coordination with security and IT teams.
ThreatMon is a robust ASM platform that provides comprehensive visibility and proactive threat management for organizations. Its advanced features, including continuous monitoring, automated threat detection, and risk prioritization, make it an essential tool for maintaining a strong security posture. However, the complexity and cost associated with the platform should be carefully considered, especially by smaller organizations.
How ThreatMon Can Help?
ThreatMon’s advanced and innovative ASM platform delivers real-time visibility and threat intelligence that seamlessly integrates into current security infrastructure, empowering you to:
- Continuously monitor and assess vulnerabilities.
- Detect and respond to threats in real time.
- Automate incident response and remediation processes.
- Integrate with other security tools for a holistic approach to ASM.
As attack surface continues to increase and become more complex, effective Attack Surface Management will be an important component for enterprise-grade cyber resilience. Using these tools mentioned in this blog, organizations can have complete visibility into their attack surface and prioritize attack vectors and vulnerabilities, enabling them to swiftly patch and mitigate. ThreatMon utilizes its core technology that offers advanced intrusion detection and vulnerability management capabilities to enable organizations to proactively monitor and respond to vulnerabilities and threats.
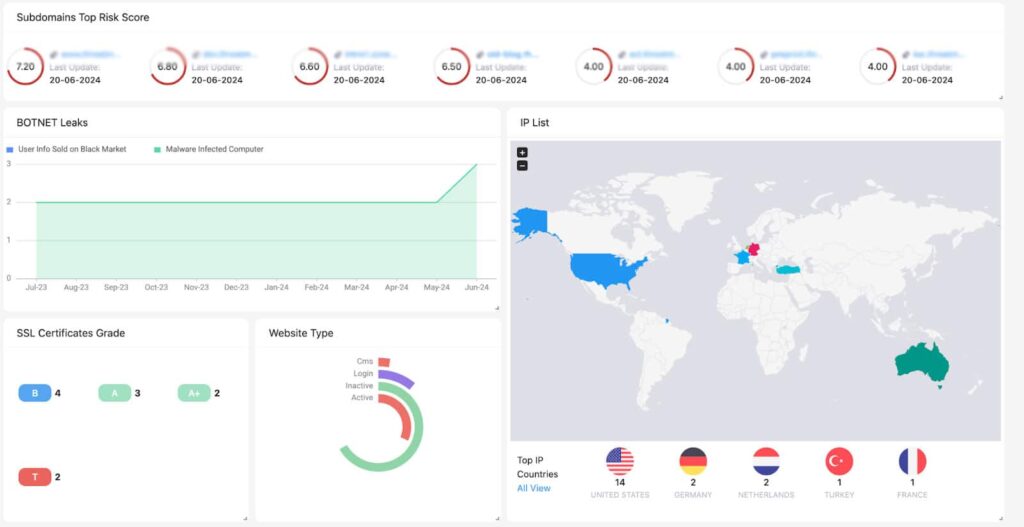
To achieve a mature ASM that helps enterprises manage ever-increasing attack surfaces, organizations will need to adopt a proactive and integrated attack surface approach to prepare for next-generation cyber risks.











