
Jquery XSS Vulnerability Version; Much information, including personal information, can be captured and operations can be performed on computers.
Let’s start with what jquery and XSS are.
Jquery is a library of JavaScript. It was created to facilitate the use of JavaScript on websites. It is not a separate programming language and works with JavaScript.
A cross-site scripting attack (XSS) occurs when a hacker injects malicious code, usually in the form of client-side scripting, into the content of a web page that is seen as benign and trustworthy.
By examining the source codes of Jquery, which is a Javascript library, harmful codes can be run in these codes. Thanks to these malicious codes, much information, including personal information, can be captured and operations can be performed on computers.
jQuery software used a regex in its jQuery.htmlPrefilter method to ensure that closing tags were XHTML-compliant when passed to methods. The developers behind jQuery described the moderate severity vulnerability as something that only came into play in “edge cases where parsing would have unintended consequences”. The XSS vulnerability resolved last month meant that “passing HTML from untrusted sources – even after sanitizing it – to one of jQuery’s DOM manipulation methods (such as .html(), .append(), and others) may execute untrusted code,” according to the write-up on GitHub.
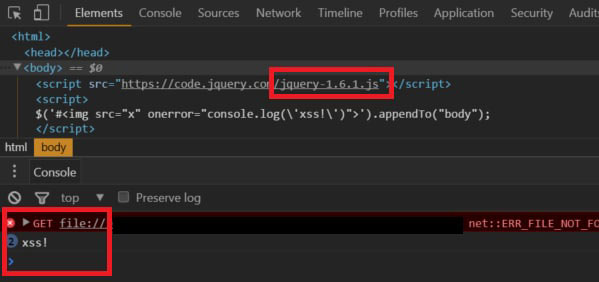
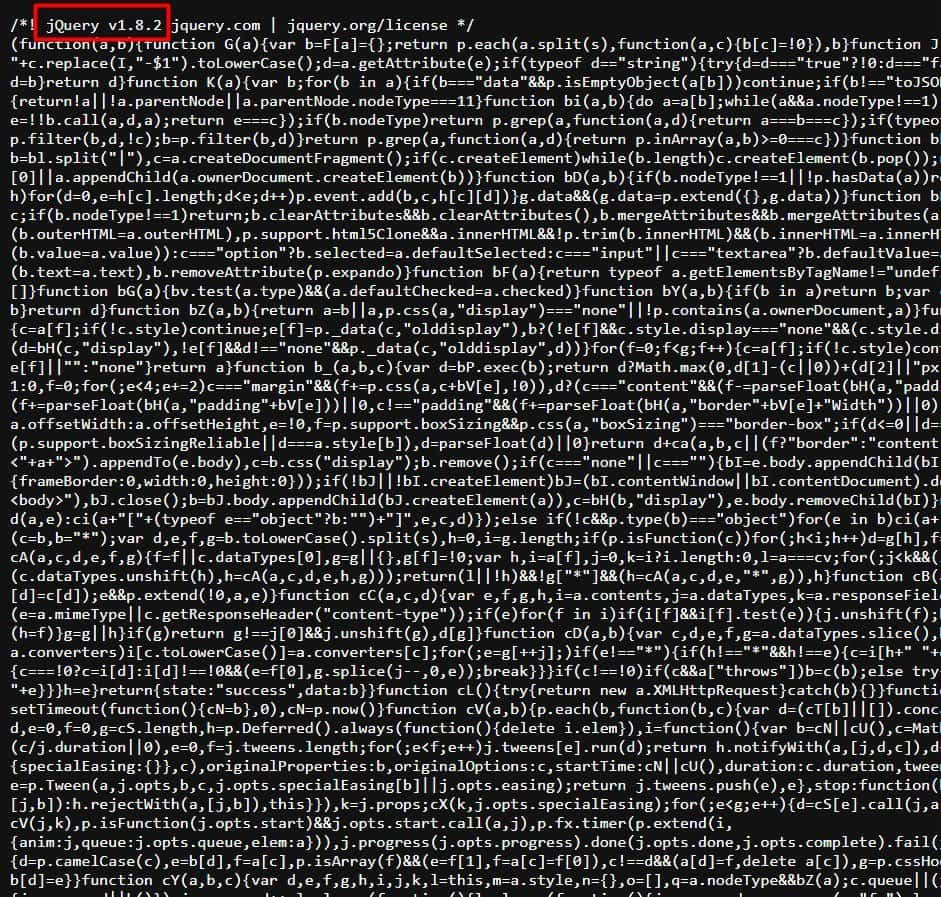
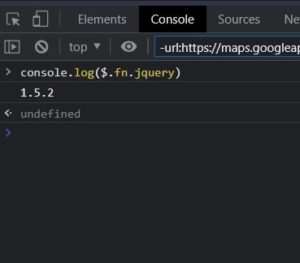
What should be done to protect from JQuery XSS vulnerability in the system?
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11023
https://nvd.nist.gov/vuln/detail/cve-2020-11022
https://nvd.nist.gov/vuln/detail/CVE-2020-7656
https://nvd.nist.gov/vuln/detail/CVE-2018-18405
https://nvd.nist.gov/vuln/detail/cve-2015-9251