Weak SSL algorithms are cryptographic protocols that do not provide adequate security, making it easier for attackers to intercept sensitive data.
Sensitive data must be protected when transmitted over the network. This data may include user credentials and credit card information. Servers are authenticated using digital certificates. These are SSL/TLS certificates.
TLS encrypts communication between servers and web applications, such as web browsers that load a website. TLS uses one or more cipher suites to protect data transfer, a combination of authentication or encryption.
There are some websites to check TLS version.
In addition, version info can be found using terminal.
This command line is used in order to find TLS version.
Nmap -sV –script ssl-enum-ciphers -p <port number> <Host>
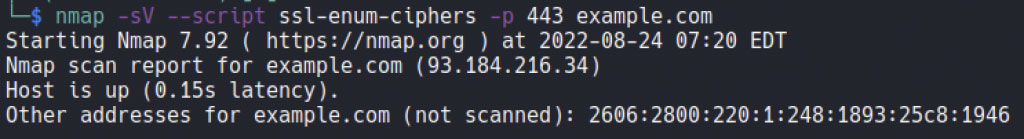
As seen below, Here is the TLS versions.
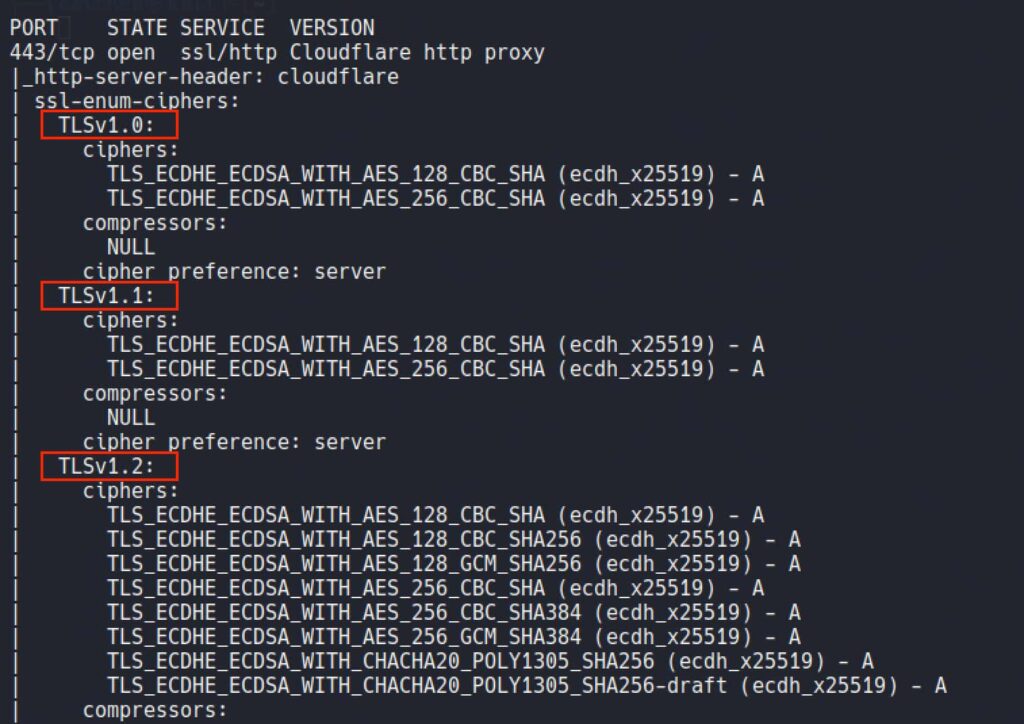
TLS 1.0, TLS 1.1, TLS 1.2 and SSLv3 are weak SSL algorithms. Using outdated or outdated versions can make it vulnerable to attacks. When using an insufficient password, an attacker can intercept or modify the data being transferred.
However, 64-bit block ciphers are also weak SSL ciphers. The use of 64-bit block ciphers can cause a SWEET32 attack.
https://owasp.org/www-project-web-security-testing-guide/01-Testing_for_Weak_SSL_TLS_Ciphers
https://nmap.org/nsedoc/scripts/ssl-enum-ciphers.html
https://www.rapid7.com/blog/post/2018/03/29/how-to-detect-weak-ssl-tls-encryption/
https://support.securityscorecard.com/hc/en-us/articles/115003260246-TLS-Protocol-Uses-Weak-Cipher