
Cisco has confirmed that the Yanluowang ransomware group has breached the company’s network and that the actor has attempted to extort the stolen files under threat of leaking them online. Cisco said on May 24, 2022 that it became aware of a possible compromise.
It was determined that a Cisco employee had his credentials after the attacker took control of a personal Google account that was synchronized with the credentials saved in the victim’s browser.
The attacker carried out a series of sophisticated voice phishing attacks masquerading as various trusted entities trying to persuade the victim to accept initiated multi-factor authentication (MFA) push notifications. The attacker eventually managed to gain an MFA push acceptance and gain access to the VPN in the context of the intended user.
Yanluowang #ransomware group has made the bold claim of an attack on @Cisco and given a long list of file names as their current evidence. File names seem to reference NDAs, AnyConnect VPN clients, source code potentially connected to SCM-Manager Git repos, and other documents. pic.twitter.com/fAdliHvhSr
— Nicholas Carroll (@sloppy_bear) August 10, 2022
The threat actor was successfully removed from the environment, and after the attack, he tried to regain access and remain persistent. However, his attempts were unsuccessful.
During the attack, attempts to leak information from the environment were observed. The only successful data theft in the attack was confirmed to contain the contents of a Box folder associated with a compromised employee’s account and employee authentication data from the active directory. But the Box data obtained is not sensitive.
“While we did not observe ransomware deployment in this attack, the TTPs used were consistent with ‘pre-ransomware activity,’ activity commonly observed leading up to the deployment of ransomware in victim environments,” Cisco Talos said in the blog post.
“We’ve also implemented additional measures to protect our systems and are sharing technical details to help protect the broader security community,” Cisco Talos added.
In an email, they attached a screenshot showing the directory listing of Box data that was leaked earlier.
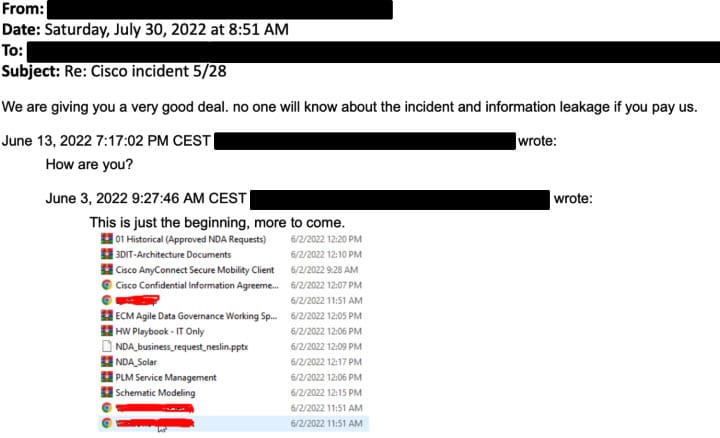
The attacker claimed to have stolen 2.75GB of data, consisting of about 3,100 files. Many of these files contain non-disclosure agreements, data dumps, and engineering drawings.
No evidence was detected that the attacker gained access to critical internal systems such as product development, code signing, and the like.
https://blog.talosintelligence.com/2022/08/recent-cyber-attack.html?m=1
https://twitter.com/sloppy_bear/status/1557454760516718593?s=21&t=7IPD8xoNTYnGnkSDNGvwBA