
Stealer log .. This article is about ‘How to Detect and Respond to Stealer Log Incidents: 10 Tips’
Introduction
Stealer logs are a growing cybersecurity threat, leaking sensitive data like login credentials, session cookies, and financial information. Instead of breaking in, cybercriminals increasingly rely on stolen data to gain unauthorized access. The good news? With the right strategies, you can detect, respond to, and prevent stealer log incidents before they escalate. In this guide, we’ll walk you through ten essential tips—and show you how ThreatMon’s cutting-edge solutions provide unmatched protection.

Alleged Data Breach of NicoVIP, March 2025
Cybercriminals often sell stolen credentials on underground forums and dark web marketplaces. ThreatMon’s dark web monitoring continuously scans these platforms, alerting businesses in real time if their credentials appear in stealer logs. This allows organizations to act fast and secure affected accounts before they are exploited.
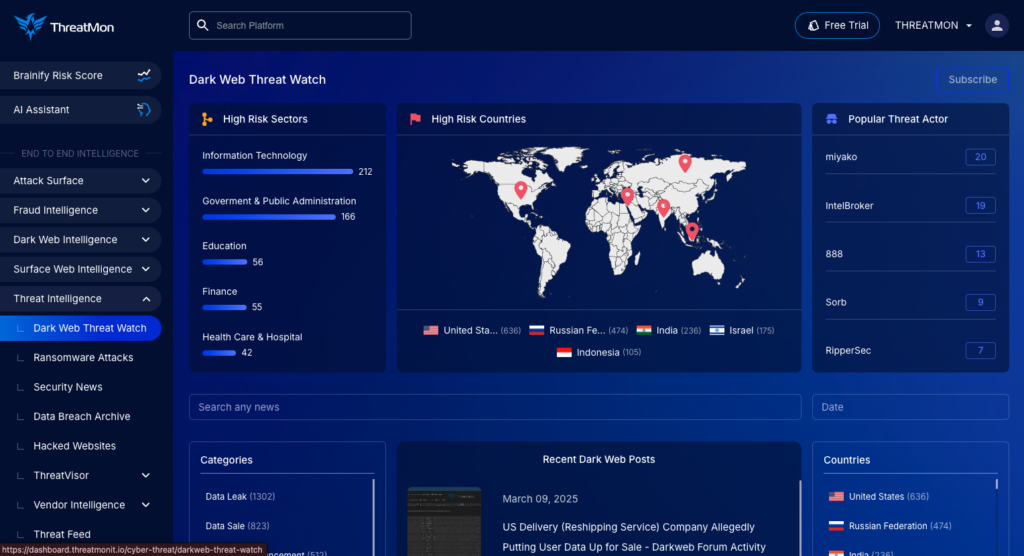
Stealer logs don’t just appear out of nowhere—they originate from phishing campaigns and malware attacks. ThreatMon’s intelligence platform helps organizations track emerging threats, detect phishing campaigns, and uncover malware distribution networks before they target your business.
Unusual data transfers, suspicious logins, or connections to known malicious IPs are all red flags. ThreatMon’s real-time traffic analysis helps businesses detect these anomalies, preventing attackers from using stolen credentials to move undetected within a network.
Infostealer malware often lurks on employee devices, silently collecting data. ThreatMon’s endpoint intelligence helps detect unauthorized data collection and alerts security teams to potential compromises before credentials are stolen.
Phishing remains the primary method for deploying infostealers. ThreatMon continuously monitors phishing attempts targeting organizations, helping security teams take preemptive measures to protect employees from falling victim to credential theft.

Even the best security measures can’t guarantee complete immunity from cyber threats. When a stealer log incident occurs, a swift and strategic response can mean the difference between a contained event and a full-scale data breach. Organizations must act quickly to limit damage, prevent further compromise, and mitigate long-term risks. Below are key steps to effectively respond to stealer log incidents and secure your organization against further exploitation.
Understanding the source of the attack is crucial:
ThreatMon’s forensic capabilities help businesses uncover these answers and implement better security measures.
Transparency is essential when dealing with compromised credentials:
Incident response requires expertise. ThreatMon works alongside internal security teams to:
Many industries require organizations to report security incidents. ThreatMon helps businesses:
One of the most effective ways to reduce the impact of stealer logs is to enforce Multi-Factor Authentication (MFA). Even if credentials are stolen, requiring an additional authentication step significantly decreases the chances of unauthorized logins. Many attackers rely on weak or reused passwords to gain access to multiple systems. ThreatMon helps organizations detect and mitigate the risks of weak credentials, ensuring employees adopt stronger password hygiene practices.
Cybersecurity awareness plays a critical role in preventing credential theft. Regular security training educates employees on how to recognize phishing attempts, avoid suspicious links, and maintain safe browsing habits. In addition to human awareness, keeping systems updated is crucial—unpatched software is a primary entry point for malware. Regular patch management closes security gaps that attackers might exploit, reducing the risk of a breach.
Data encryption adds another layer of security by rendering stolen credentials and sensitive files useless to cybercriminals. By encrypting information both in transit and at rest, organizations can minimize the damage of unauthorized data access. Finally, real-time AI-powered threat detection is essential in today’s fast-moving cyber landscape. ThreatMon’s AI-driven threat analysis continuously monitors activity, detects suspicious behavior, and helps businesses stop attacks before they escalate.
Stealer logs aren’t going away, but businesses that take proactive steps can significantly reduce their risk. ThreatMon offers advanced threat intelligence, dark web monitoring, and real-time security solutions to keep organizations safe.
Don’t wait for an attack—take control of your cybersecurity strategy today. Get in touch with ThreatMon to learn how we can help protect your digital assets and stay ahead of emerging threats.