
Kaspersky’s report highlights the rise of malicious browser extensions that steal cryptocurrency and perform web injects.
Kaspersky analyzed threat statistics by processing data voluntarily shared by its users for the period from January 2020 to June 2022. According to this data, during the first half of this year, 1,311,557 users tried to download malicious or unwanted extensions at least once.
From January 2020 to June 2022, nearly 70 percent of users affected by malicious and unwanted add-ons were targeted by adware lurking in browser extensions.
Malicious and unwanted add-ons are often distributed using official stores. In 2020, Google removed 106 browser extensions from the Chrome Web Store. All of them were used to collect sensitive user data such as cookies and passwords and even take screenshots.
Sometimes the user can assess the risks by looking at what permissions an extension is requesting when installed from the store.
While extensions do not have malicious functionality, they can be dangerous. The danger is that after many extensions have access to “read all data from all websites”, they collect large amounts of data from the web pages users visit. Developers may pass it on to third parties or sell it to advertisers.
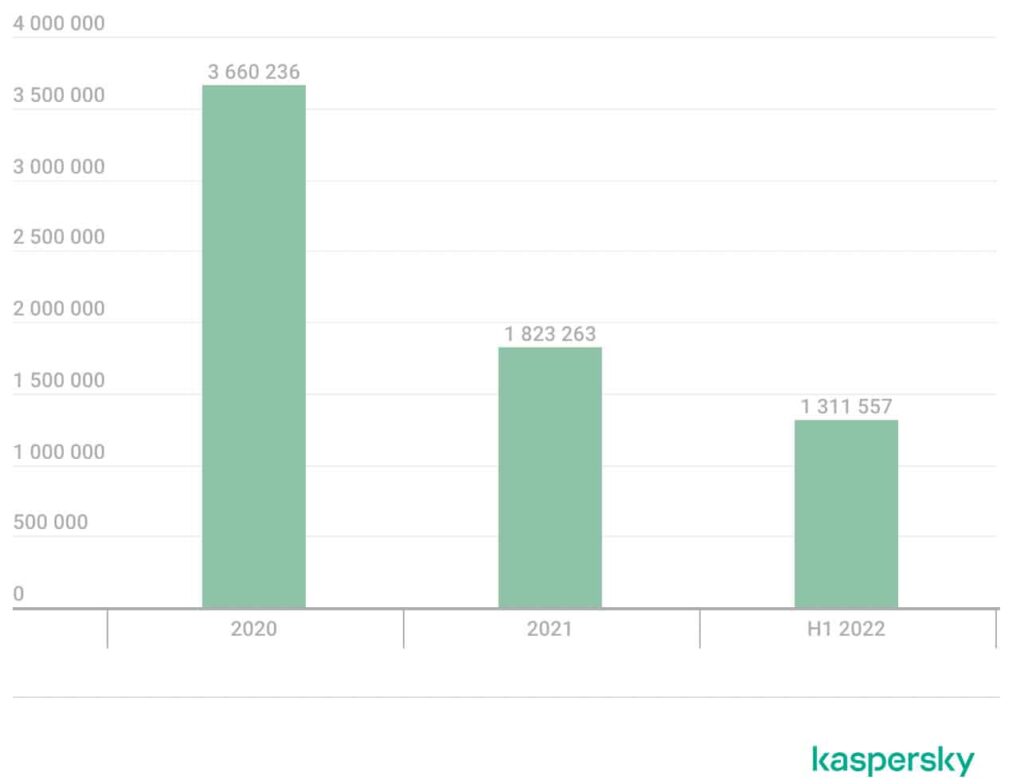
Number of users affected by malicious or unwanted browser extensions
“Our telemetry shows that the most common threat spread under the guise of browser extensions is adware — unwanted software designed to promote affiliates rather than improve user experience,” Kaspersky said in the report.
They use browser history to tap into users’ interests with such advertisements, to redirect them to affiliate pages where adware developers make money, or to embed affiliate links on web pages.
In the first half of 2022, 876,924 users used the WebSearch plugin. This threat includes DOC to PDF converters, document merging, etc. It acts as if they are tools for working with documents such as WebSearch extensions change the browser’s start page. It consists of a search engine and several links to third-party resources such as AliExpress or Farfetch. Migration to these resources is carried out through affiliate links. This is how attackers make money from their extensions.
In the first half of 2022, 156,698 unique users encountered AddScript were observed. The function of this extension is to download music and videos from social networks or proxy managers.
However, such extensions perform malicious activities as well as useful functions. It uses post-install JavaScript to run videos in the background and save views on YouTube channels.
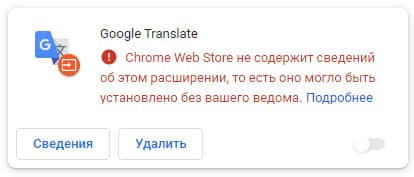
One of the most dangerous families is FBStealer. Besides traditional search engine substitution, it can steal user credentials from Facebook. Between January and June 2022, 3,077 users were identified who encountered FB Stealer.
FB Stealer is installed by malware, not by the user. Once added to the browser, it mimics the standard-looking Google Translate extension.
DealPly-related extensions are adware that first appeared in late 2018 and remains popular with cybercriminals.
Between January and June 2022, 97,515 users encountered DealPly related plugins. Similarly, DealPly related extensions also change the browser’s start page to place affiliate links on it. The default search engine is changed to block user requests.
All searches made by users in this engine are analyzed by the extension. According to the keywords in the searches, the user is directed to a suitable site.
https://securelist.com/threat-in-your-browser-extensions/107181/