
In the ever-evolving world of cybersecurity, new threats emerge constantly, challenging our defenses and requiring continuous vigilance. One such threat that has recently come to light is the “Kematian Stealer,” an advanced information-stealing malware. ThreatMon’s Kematian Stealer Technical Analysis Report aims to provide an in-depth analysis of this potent malware, its features, and the mitigation strategies necessary to protect against it.
Kematian Stealer is a sophisticated PowerShell-based malware designed to infiltrate Windows systems and exfiltrate sensitive data. Developed by a group of contributors and shared openly on GitHub, it stands out for its advanced capabilities and stealthy operations. Unlike other open-source stealers that rely on Discord or Telegram, Kematian Stealer uses a custom Command and Control (C2) server, enhancing its effectiveness and evasion techniques.
Kematian Stealer differs from other known open-source stealer malware. Typically, known open-source stealer malware are Discord or Telegram- based, whereas Kematian Stealer operates with a custom C2 (Command and Control) server. Additionally, because of its fileless feature, it can evade traditional security measures such as firewalls and antivirus software.
Kematian Stealer creates a mutex on the system and designates the process as critical before initiating data exfiltration, ensuring smooth and uninterrupted data transmission. It also has robust persistence mechanisms that remain active on the machine after reboot. Additionally, its user-friendly web-based GUI builder simplifies the process of creating payloads, enhancing its accessibility and usability.
Kematian Stealer initiates its attack with a method, the most commonly used being a phishing attack. When the targeted Windows user opens the file, it forces the UAC to grant admin privileges within the script. After gaining admin privileges, it creates a critical process and collects critical data from the system through some system changes. The collected data is then exfiltrated to the attacker’s C2 server via an HTTP POST request.
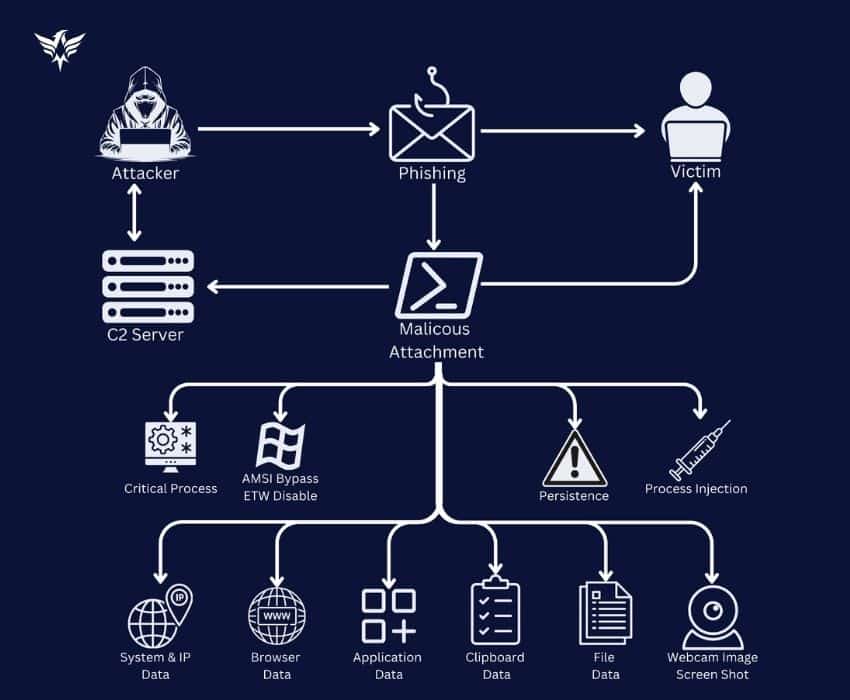
The malware’s source code is a blend of Python, PowerShell, Go, JavaScript, and Batchfile, although it primarily operates using PowerShell and Batchfile scripts. It employs various evasion techniques, including checking for VM environments, low RAM, and specific malware analysis tools to prevent detection and analysis.
The documentation and the Readme.md file on GitHub of Kematian—Stealer provides information on how to remove the malware if the system is infected.
In a simple way, running the following PowerShell code shared by the Kematian-Stealer project in PS1 format as administrator on the system will remove the malware from the system. To learn more, read the Kematian Stealer Technical Analysis Report.
Do not install applications from unknown sources and senders.
When downloading an application from a site, make sure it is the original and official site.
Avoid using cracked applications.
Be vigilant against phishing emails and ensure the sender and source are reliable.
For files or software you are unsure about but must open, use a VM or Sandbox.
Set up your security software to block the IOCs listed in the IOC section.
Integrate Yara and Sigma rules into your security products.
Request training against social engineering attacks.
Regularly install your Windows updates.
Enable Two-Factor Authentication (2FA) for every account you use.
Change your passwords regularly.
Use application whitelisting to allow only trusted and authorized programs to run on the system.
Implement appropriate password policies and practices and regularly audit and secure credentials.
To protect critical files, use strong encryption methods to safeguard these files from unauthorized access.
Restrict user and application access to the Windows Registry and regularly monitor and audit registry changes.
Kematian Stealer represents a significant threat due to its advanced features and ability to operate stealthily. Understanding its capabilities and implementing robust security measures is crucial in defending against such sophisticated malware. Stay informed, stay vigilant, and prioritize cybersecurity to protect your valuable data from malicious actors.