Miyako is a sophisticated, new threat actor, recently making waves for cyber attacks on critical infrastructure, financial institutions, and governments across the globe. In this article, we’ll look at the special features, operations, motivations, and consequences of Miyako’s actions, as well as ways that organizations can prevent such risk from this sophisticated threat actor.
Origin and Attribution
Its name, “Miyako,” was translated from a Japanese term for “capital” or “city,” as it is aimed at critical infrastructure in the urban and capital regions. It is not clear where exactly Miyako came from, but there are indications of links to East Asian cybercriminal forums and government-run organizations. Some observers even argue that Miyako operates as a kind of semi-autonomous unit within a wider geopolitical structure using high-tech cyber capabilities to accomplish economic and political goals.
Key Characteristics
There are a number of characteristics of Miyako that distinguish it from other threat actors:
Advanced Toolsets:
Miyako leverages custom malware, like “Kintsugi,” which is built to take advantage of zero-day vulnerabilities in enterprise platforms used every day. The collective uses polymorphic code that is hard to detect with regular antivirus systems.
Operational Sophistication:
The threat actor uses a multistage attack approach from reconnaissance to coordinated lateral migration and data extirpation. It has high-accuracy attacks that do as little collateral as possible and do as much damage as possible.
Hybrid Motivation:
Miyako’s work seems dualistic, as well as financially motivated and nation-state-level spying. Targets range from key supply chains to universities and the federal government.
Attack Lifecycle
Miyako’s operations begin with reconnaissance, where the group leverages open-source intelligence (OSINT) tools to identify high-value targets and vulnerabilities in their digital ecosystem. This phase often includes advanced spear-phishing campaigns to gather initial access credentials. Once initial compromise is achieved, Miyako exploits zero-day vulnerabilities in VPNs, firewalls, and cloud-based applications. The group deploys malware with advanced evasion techniques to bypass endpoint detection systems, securing a foothold in the target network.
To maintain persistence, Miyako installs backdoors and rootkits, enabling prolonged access. The group cleverly uses legitimate administrative tools, such as PsExec and PowerShell, to blend in with normal network traffic and evade detection. As they move laterally across the network, Miyako employs credential dumping and privilege escalation to gain control over critical systems. Using compromised accounts, they propagate through the network to identify and exfiltrate valuable data.
In the final stage, Miyako encrypts or steals sensitive data, often demanding ransom payments in cryptocurrency. The group frequently engages in double-extortion tactics, threatening to leak stolen data if their demands are not met, amplifying the impact on their victims.
Implications
Miyako’s operations highlight several alarming trends. The group’s use of Ransomware-as-a-Service (RaaS) platforms demonstrates a growing convergence between criminal and state-sponsored cyber activities, blurring the lines between traditional cybercrime and geopolitical actions. By targeting supply chains, Miyako amplifies its reach and impact, creating vulnerabilities that threaten the stability of global markets. Additionally, the potential state-sponsored nature of its activities adds another layer of complexity, as these attacks could serve as precursors to larger geopolitical conflicts, escalating tensions between nations.
Tactics, Techniques, and Procedures (TTPs)
Initial Access
Technique:
- Exploitation of Public-Facing Applications (T1190)
- Exploits vulnerabilities in software like GitLab (e.g., CVE-2024-45409 – SAML authentication bypass).
- Targets exposed services like firewalls and enterprise applications.
- Phishing (T1566)
- Used to harvest credentials for access.
Execution
Technique:
- Command and Scripting Interpreter (T1059)
- Utilizes Python scripts to generate dummy traffic for reconnaissance and obfuscation.
Persistence
Technique:
- Account Manipulation (T1098)
- Manipulates legitimate user accounts to maintain access.
Privilege Escalation
Technique:
- Exploitation for Privilege Escalation (T1068)
- Exploits misconfigurations in identity management systems like SAML.
Defense Evasion
Technique:
- Obfuscated Files or Information (T1027)
- Compresses and encrypts stolen data before exfiltration.
Credential Access
Technique:
- Brute Force (T1110)
- Target credentials are stored in weakly secured systems like PhpMyAdmin panels.
Discovery
Technique:
- Network Service Scanning (T1046)
- Scans network services to identify exploitable endpoints.
Collection
Technique:
- Data from Information Repositories (T1213)
- Collects sensitive financial, customer, and operational data.
Exfiltration
Technique:
- Exfiltration Over Web Service (T1567)
- Uses platforms like WeChat to transmit stolen data.
MITRE Mapping
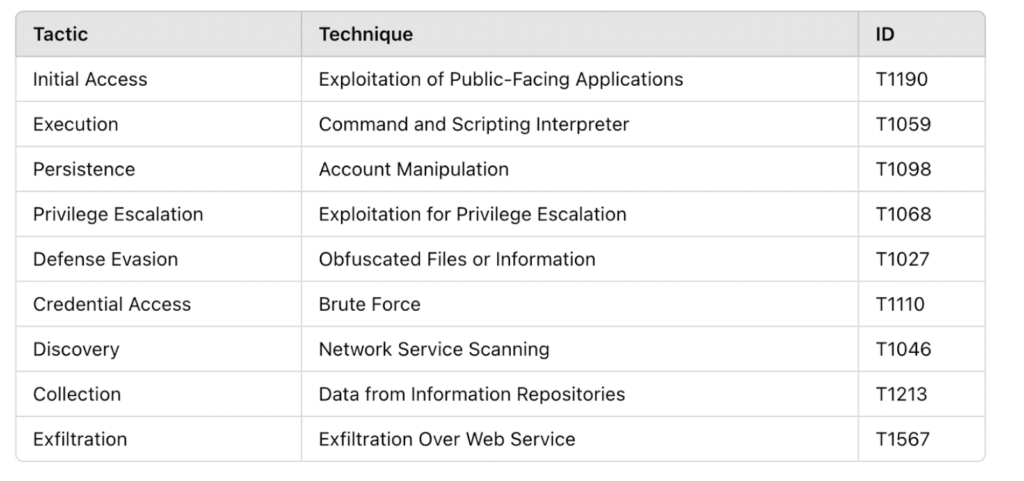
Sample Yara Rule
 This is just a template. Actual YARA rules, IOCs and IOAs are available for customers only.
This is just a template. Actual YARA rules, IOCs and IOAs are available for customers only. 
Case-Studies
Miyako, an emerging threat actor, has been linked to several notable cyber incidents in 2024, primarily involving the sale of unauthorized access to various organizations:
- FBI Subdivision Access Sale (December 2024): Miyako claimed to possess and sell unauthorized root access to a firewall belonging to a subdivision of the Federal Bureau of Investigation (FBI) in the United States. This breach, targeting a critical law enforcement agency, underscores the group’s audacity and the potential risks posed to national security.
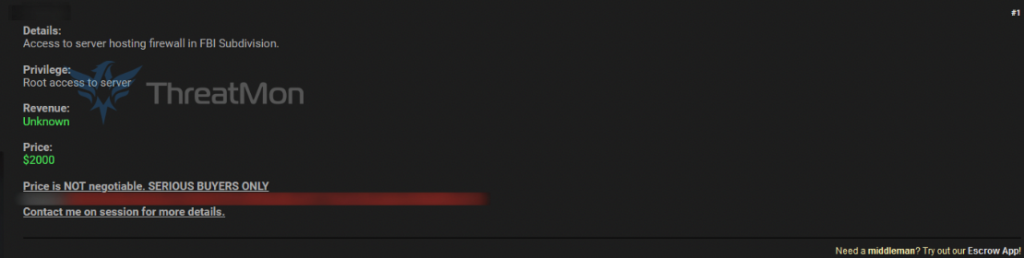
- State University Access Sale (November 2024): Miyako allegedly offered access to an unidentified state university in the USA, reported to have $5.6 billion in revenue. The sale of such access could lead to significant data breaches, affecting students, faculty, and research integrity.
- Tourism Company Server Access Sale (November 2024): The group purportedly sold server access to an unidentified tourism company. Compromising such an entity could disrupt services and lead to the theft of sensitive customer information.
- Domain Name Registrar Access Sale (December 2024): Miyako claimed to have access to an unidentified domain name registrar. Unauthorized access to such a service could facilitate widespread domain hijacking or phishing attacks, posing risks to numerous websites and their users.
- Indonesian University Access Sale (December 2024): The group allegedly offered access to an unidentified university in Indonesia. Such a breach could compromise academic records, research data, and personal information of students and staff.
These incidents highlight Miyako’s focus on infiltrating diverse sectors, including education, tourism, and government agencies and monetizing unauthorized access. Organizations are advised to enhance their cybersecurity measures to mitigate the risks posed by such threat actors.
Target Sectors:
- Government and Public Institutions
- Healthcare
- Finance
- Energy
- Internet Service Providers (ISPs)
- Technology and Software
- E-commerce and Retail
- Manufacturing and Engineering
- Education
- Media and News
Target Countries:
- United States (USA)
- China
- France
- Hong Kong
Top Attacks
- FBI Subdivision
- Canadian ISP
- $9bil Revenue USA Medical Center
- United States Air Force Base
- $9bil Revenue French Energy Distribution
- Indonesian Government Financial Services
Defense Strategies
Mitigating threats from sophisticated actors like Miyako necessitates a comprehensive and multi-layered cybersecurity approach.
Below are key strategies to enhance your organization’s defenses:
- Regular Software Updates and Patch Management: Ensure all systems and applications are consistently updated to address known vulnerabilities. Automating this process can reduce the window of opportunity for attackers to exploit unpatched systems.
- Implement Strong Access Controls: Adopt the principle of least privilege, granting users only the access necessary for their roles. Utilize multi-factor authentication (MFA) to add an extra layer of security, making unauthorized access more difficult.
- Network Segmentation: Divide your network into segments to contain potential breaches. This approach limits lateral movement by attackers, preventing them from accessing critical systems even if one segment is compromised.
- Continuous Monitoring and Threat Detection: Employ advanced monitoring tools to detect anomalous activities in real-time. This proactive stance enables swift identification and response to potential threats, minimizing damage.
- Employee Training and Awareness: Conduct regular training sessions to educate employees about cybersecurity best practices, including recognizing phishing attempts and social engineering tactics. An informed workforce serves as a vital line of defense against cyber threats.
- Develop and Test Incident Response Plans: Establish a comprehensive incident response plan outlining procedures for detecting, responding to, and recovering from cyber incidents. Regularly test and update this plan to ensure its effectiveness during actual events.
- Secure Backup and Recovery Solutions: Implement robust backup solutions for critical data, ensuring backups are encrypted and stored offline or in secure cloud environments. Regularly test recovery procedures to guarantee data integrity and availability during crises.
- Leverage Threat Intelligence Services: Subscribe to reputable threat intelligence services to stay informed about emerging threats and attacker tactics. This knowledge enables timely adjustments to security measures, keeping defenses aligned with the evolving threat landscape.
By integrating these strategies into your cybersecurity framework, your organization can significantly enhance its resilience against advanced threat actors like Miyako.
In conclusion,
The emergence of threat actors like Miyako underscores the critical importance of robust cybersecurity measures. Their sophisticated tactics and persistent efforts to exploit vulnerabilities highlight the need for organizations to remain vigilant and proactive. Implementing comprehensive security strategies, fostering a culture of awareness, and staying informed about evolving threats are essential steps in safeguarding digital assets. By adopting these measures, organizations can enhance their resilience against adversaries and contribute to a more secure cyber landscape.

 This is just a template. Actual YARA rules, IOCs and IOAs are available for customers only.
This is just a template. Actual YARA rules, IOCs and IOAs are available for customers only. ![]()
