
Polyfill.io Supply Chain Attack: How Over 100,000 Websites Were Compromised and What You Need to Know
A highly used open-source JavaScript library, Polyfill.io helps to enable older browsers to implement modern web functionalities. This highly trusted service has recently been compromised, leading to massive supply chain attacks affecting over 100,000 websites. The rogue changed from reoriented users to scam and malicious sites.
Researchers did issue warnings about a new supply chain attack that has begun and one that emanates from the Polyfill[.] to service. The attack has shockingly impacted quite a share of sites and, as such, caused ripples among developers and owners of the websites. The malicious scripts on the cdn.polyfill.io domain have spread to place most users at risk, exposing them to several malicious activities that include redirecting users to sports betting and pornographic sites. The very clever script, therefore, acts at given times, making detection and analysis very difficult.
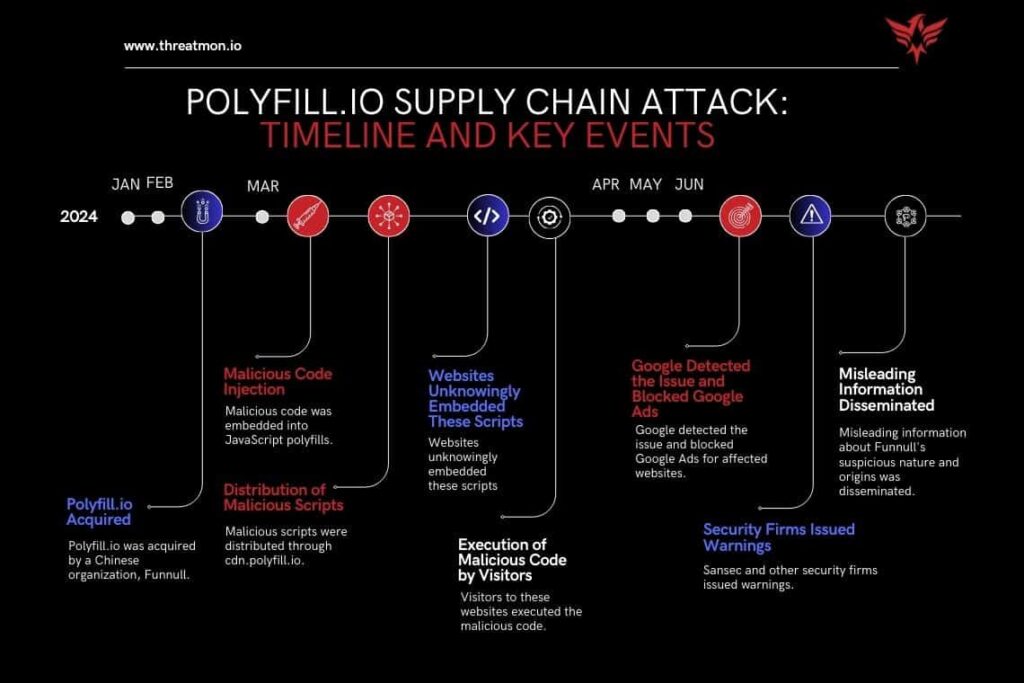
The problem started in February 2024 after Funnull, a Chinese content delivery network company, bought Polyfill.io. In March 2024, serious concerns were raised as malicious activities were detected. On June 25, 2024, Sansec reported the incident about changes made to the Polyfill domain and the GitHub account.
In their report, Sansec outlined how Funnull had begun serving malware to smartphones through the hacked domain on any website loading “cdn.polyfill.io.” The injected scripts actively weaponized attacks, and, considering the scale with which developers use Polyfill, the malicious code gets spread widely in this manner.
This represents a threat to over 110,000 websites that have embedded the Polyfill library from cdn.polyfill.io. All around the world, each has silently accepted malicious scripts to hijack their users to undesired locations, such as sports betting or pornographic sites. One can only imagine how huge and destructive this can get. The redirection of the Polyfill[.]io service to polyfill.io.bsclink.cn, managed by Funnull, enabled developers to embed those scripts in their solutions without their knowledge. It redirected end-users, primarily to take them to scam websites, through the redirection of fake Google Analytics domains and other types of malicious URLs.
Initially, Andrew Betts created Polyfill.io, but after its creation, he sold its domain to a company, Funnull, located in China. The sale of the domain immediately raised suspicion among cybersecurity experts because of the buyer’s past and the vast number of changes he was making to the JavaScript library. It was these crucial companies in the web infrastructure that discovered these activities, such as Google, Cloudflare, and Fastly, along with companies specialized in cybersecurity like Sansec and c/side.
Looks like Polyfill.io was sold to a Chinese company that offers CDN/DDOS protection services.
Not to say they aren’t trustworthy, but allowing a company to load a script on your page implicitly requres a lot of trust, and is the reason why many don’t even load google…
— Wes Bos (@wesbos) February 26, 2024
Sansec said Funnull acquired the domain of Polyfill and its GitHub account in February 2024. Using the compromised domain to inject malware into mobile devices through any site that used “cdn.polyfill.io,” it took full advantage of Polyfill.io’s credibility and high usage of Polyfill.io to spread such malicious activities widely.
This is a supply chain compromise in its nature. Polyfill.io was trusted and widely used by many websites to allow cross-browser compatibility, fundamentally changing the inclusion of malicious code into underlying tools that represent severe breaches of trust and security. Again, underlining the weaknesses companies are exposed to when they use third-party libraries are the possible risks associated with the libraries once compromised. It affected more than 100,000 websites that actively used the library, essentially spreading its attack surface very wide. Risk exposure is high, given that every infected site had the potential to receive thousands of visitors each day. Widely adopted Polyfill.io means that the tainted code had a broad reach and thus had a significant impact on the attack.
ASM brings your technology landscape into view, alerting you to technologies you might not know you have, and enabling you to react swiftly the moment a threat arises. It’s therefore a tool to empower your mitigation of risks – and your defense of digital assets.
To detect and handle an attack by Polyfill.io, your website has to go through some important steps.
Asset Discovery and Inventory: Catalog all external assets (websites, servers, APIs, third-party services and so on), and continuously identify new ones by using automated discovery tools. Doing this will allow you to keep an inventory of your digital asset footprint.
Attack Surface Intelligence detects the technologies you use, actively adds Pollyfile.io to the inventory if you are using it, and monitors it, if any.
Continuous Monitoring: Once you know the areas of your attack surface that can serve as attack vectors, you should try to monitor them continuously. There are multiple elements of your attack surface that can pose a vulnerability: newly discovered vulnerabilities, changes in configurations, and possible specific indicators of compromise can all signal that your environment might be under attack. The faster you can detect and monitor a threat, the more time you have to respond to it.
Review the script codes that are embedded in your website, especially those involving cdn.polyfill.io, for any modifications or additions that might be unauthorised. Look for any unauthorized changes or additions using tools like Snyk, Veracode, and Checkmarx. Detecting unauthorized script modifications early can prevent malicious code execution.
Attack surface Intelligence monitors your website and detects changes thanks to continuous asset monitoring.
Monitor the DNS records for cdn.polyfill.io: if they flip from one to another, that’s an indicator that a site may have been compromised. When you’re on a Django site you can query DNS like this: $ dig +tcp cdn.polyfill.io
Attack surface Intelligence monitors your DNS record and detects changes thanks to continuous asset monitoring.
Vulnerability Assessment: Vulnerabilities exist, as an essential part of any technology. Assets must be routinely scanned for vulnerabilities using both automated and manual assessments for a more consistent coverage. This will heighten awareness of a potential security gap through identification.
ASI can provide vulnerability intelligence, allowing you to identify and address these weaknesses proactively.
Prioritise by risk: determine what risks are high, and tackle those abuse vectors and vulnerabilities that an attacker could use. Prioritising attracts attention to the most critical risks.
The Polyfill.io attack highlighted a significant gap in visibility, which is often the biggest challenge in managing security. Many organizations struggle to know which technologies they are using, leaving them vulnerable to such attacks. Effective ASI provides this crucial visibility, allowing organizations to detect threats as soon as they emerge. By having a comprehensive view of all assets and their associated risks, ASI enables prompt and effective responses to security incidents.
Remove Compromised Scripts: The moment you are aware of potential script-manipulation, any scripts sourced from cdn.polyfill.io need to be removed and either replaced with known and vetted alternatives or self-hosted for genuine control over their integrity.
If your website uses https://t.co/3xHecLPXkB, remove it IMMEDIATELY.
I created the polyfill service project but I have never owned the domain name and I have had no influence over its sale. https://t.co/GYt3dhr5fI
— Andrew Betts (@triblondon) February 25, 2024
Update Security Policies: Use strict content security policies (CSP) to prevent scripts from loading from the wrong places This will ensure that people can’t execute scripts on your site even if they do manage to guerrilla-hack the JavaScript.
Patch Vulnerabilities: Make sure you keep the software your site is written in (and all third-party libraries used by that software) up to date with the latest security patches. A key to mitigating attacks is patching vulnerabilities as soon as they emerge.
Deploy Web Application Firewalls (WAF): Leverage WAFs to filter and monitor HTTP traffic to and from your web applications. WAFs can block malicious requests and help protect your site from attacks.
Educate Your Team: Perform regular security awareness training for your development and IT teams so that they are cognizant of the risks posed by these third-party libraries and committed to taking preventative security measures.
Using ThreatMon helps harden and secure your website by being a threat intelligence and monitoring solution. What ThretMon can provide:
ThreatMon translates dark web and surface web intelligence into actionable intelligence so you can stay ahead of the bad guys.
Act before a cyber-attack happens by getting real-time warnings and analyses of new threats and vulnerabilities to your system with our Threatmon.
Threatmon automates security operations to help your security team handle security alerts faster and more effectively.
With ThreatMon, you have strong tools to help prevent damage from supply chain attacks and other forms of cyber attacks.