ATTACK SURFACE INTELLIGENCE
Your Weakest Supplier Could Be Your Biggest Threat
Supply chain cyberattacks have surged by 742% over the last three years.
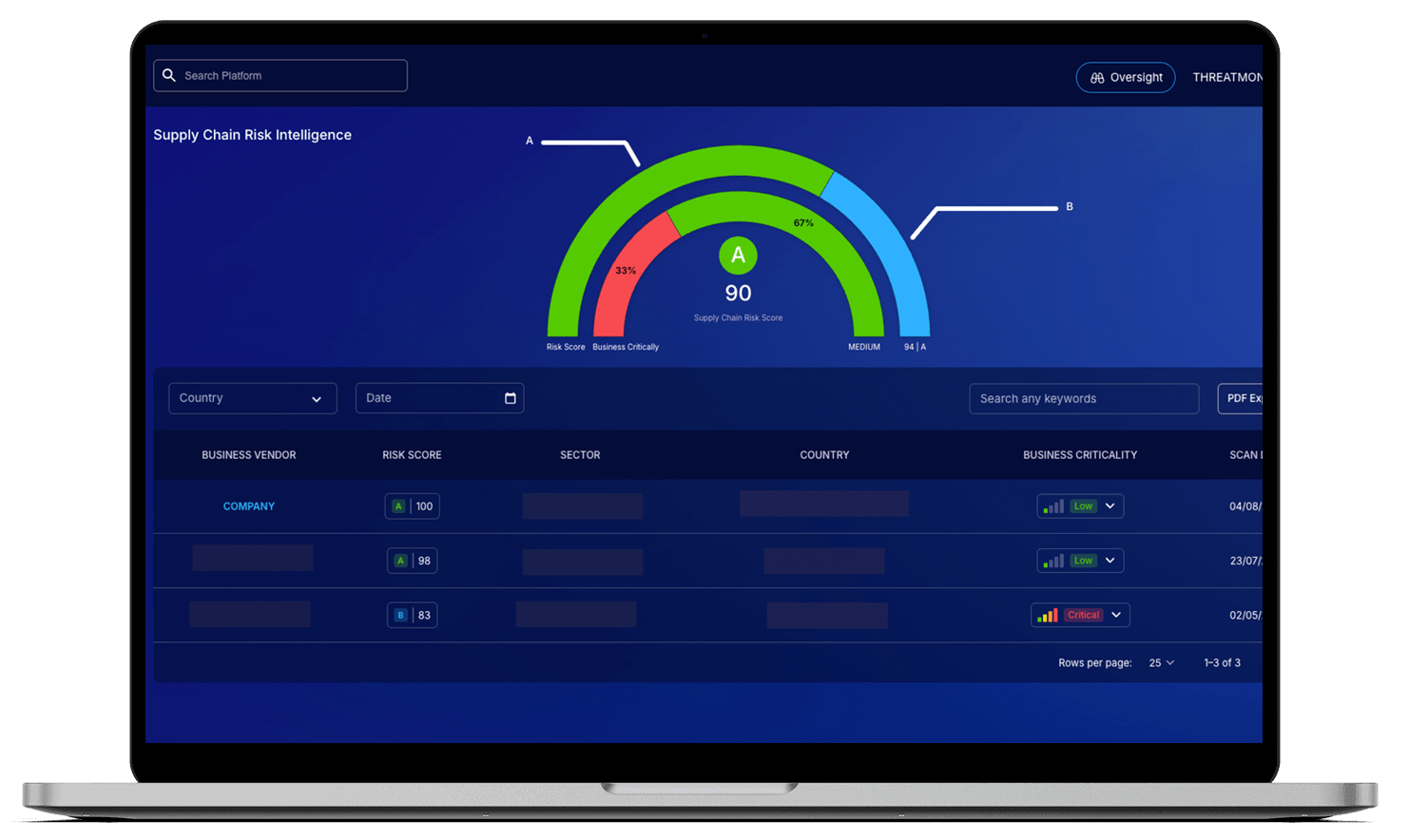
Supply chain risks have become one of the most critical cyber threats facing organizations today. Many attacks no longer target companies directly; instead, they exploit vulnerabilities in third- or fourth-party vendors, leading to data leaks, operational disruptions, and reputational damage. Protecting only your own infrastructure is no longer enough—your overall risk posture is now shaped by the security of every partner you work with.
The ThreatMon Supply Chain Risk Intelligence module was designed to meet this challenge. It continuously monitors the supplier ecosystem, uncovering vulnerabilities, misconfigurations, data leaks, and suspicious activity. Findings are presented through clear reports and risk scores, making it easy to see which vendor carries which risks.
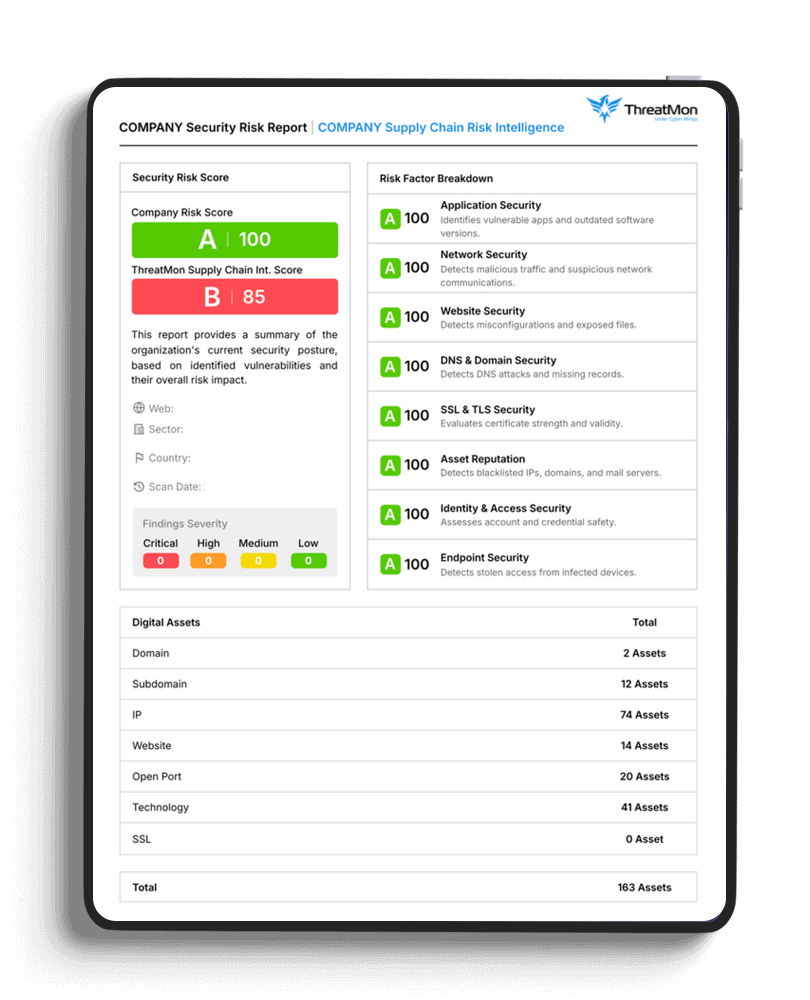
This proactive approach helps security teams detect potential threats early and take action before they escalate. With ThreatMon, organizations can secure their vendor relationships while safeguarding business continuity and reputation.
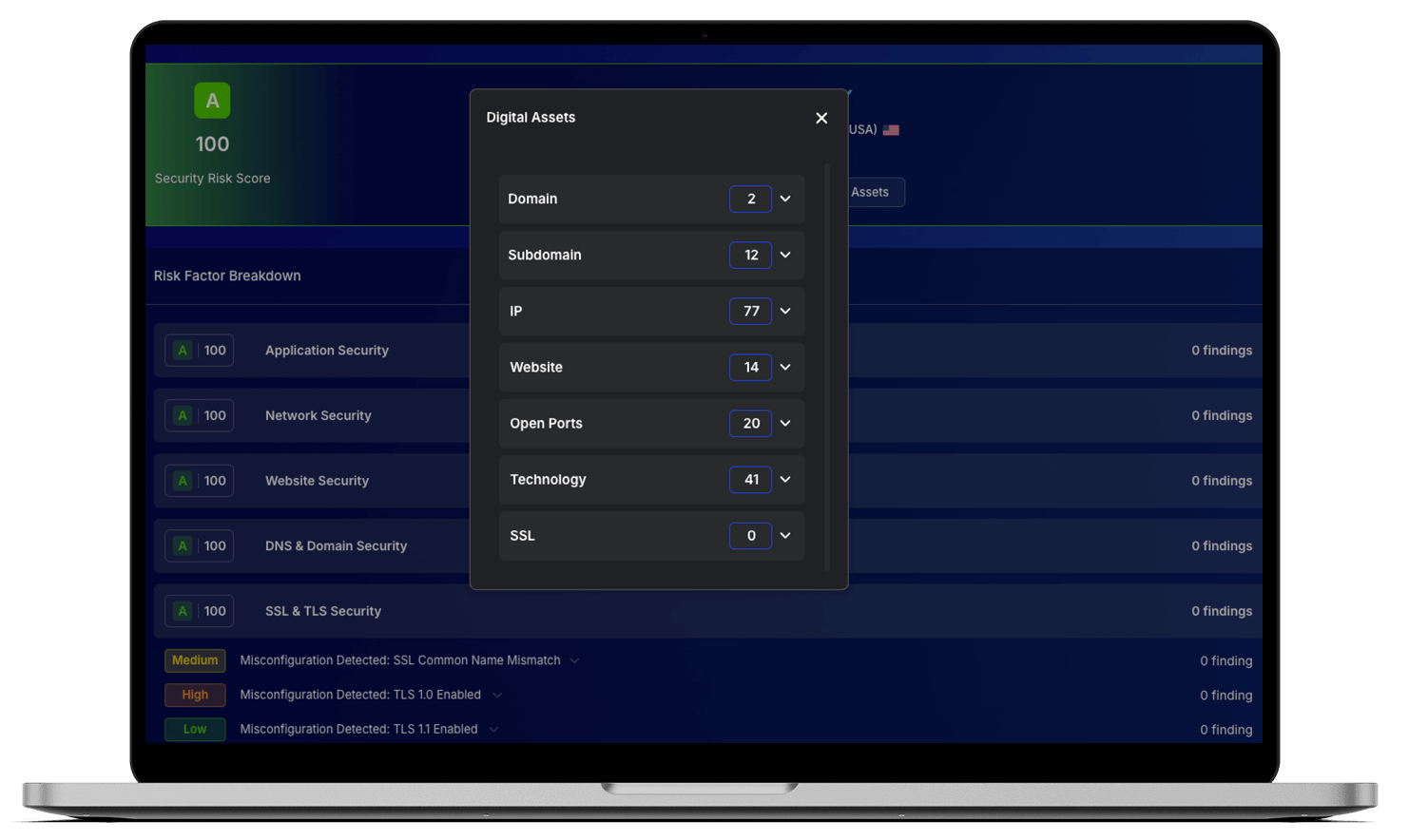
Monitor every vendor’s digital footprint, including domains, IPs, subdomains, and associated technologies. This module provides a real-time map of third-party exposures, helping organizations identify hidden assets and blind spots before attackers exploit them.
Key Benefits of Attack Surface Monitoring:
Key Benefits of Data Leak & Exposure Tracking:
Assess vendor identity and access management practices, including weak authentication controls, privilege misconfigurations, and leaked credentials. This module highlights how attackers could exploit identity weaknesses to infiltrate supplier ecosystems.
Key Benefits of Identity & Access Risks:
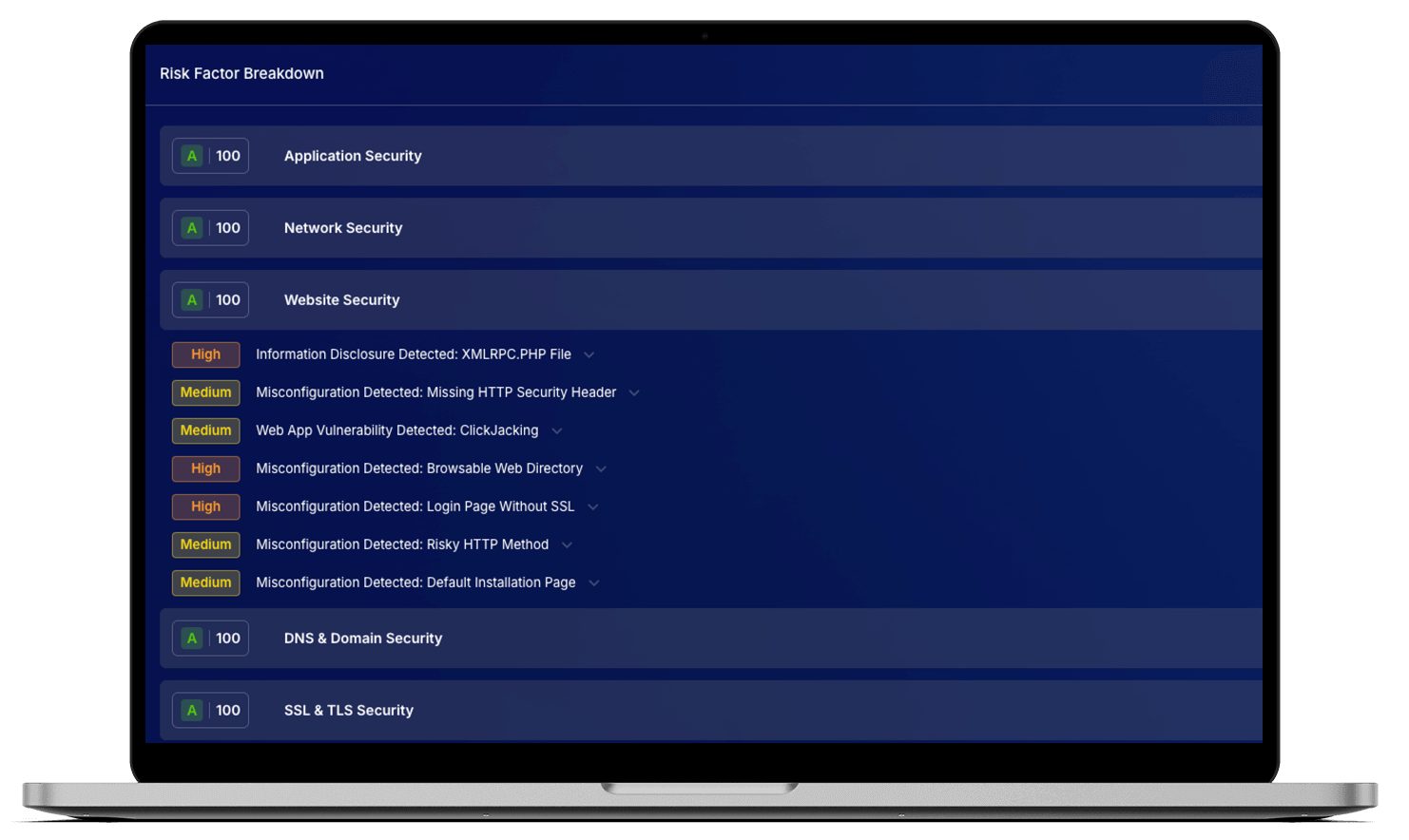
Evaluate the overall security posture of each supplier through multi-layered assessments. This module measures adherence to best practices across application, network, DNS, SSL/TLS, and endpoint security, providing a clear snapshot of vendor resilience.
Key Benefits of Security Posture:
Translate complex findings into clear, actionable scores that measure vendor risk. This module generates easy-to-understand, color-coded risk ratings across nine security layers, helping teams focus on the highest-risk suppliers first.
Key Benefits of Risk Scoring:
Generate detailed, audit-ready reports that consolidate risk findings, security scores, and incident trends across your supply chain. This module makes it simple to communicate risk posture to executives, auditors, and stakeholders.
Key Benefits of Reporting & Analytics:
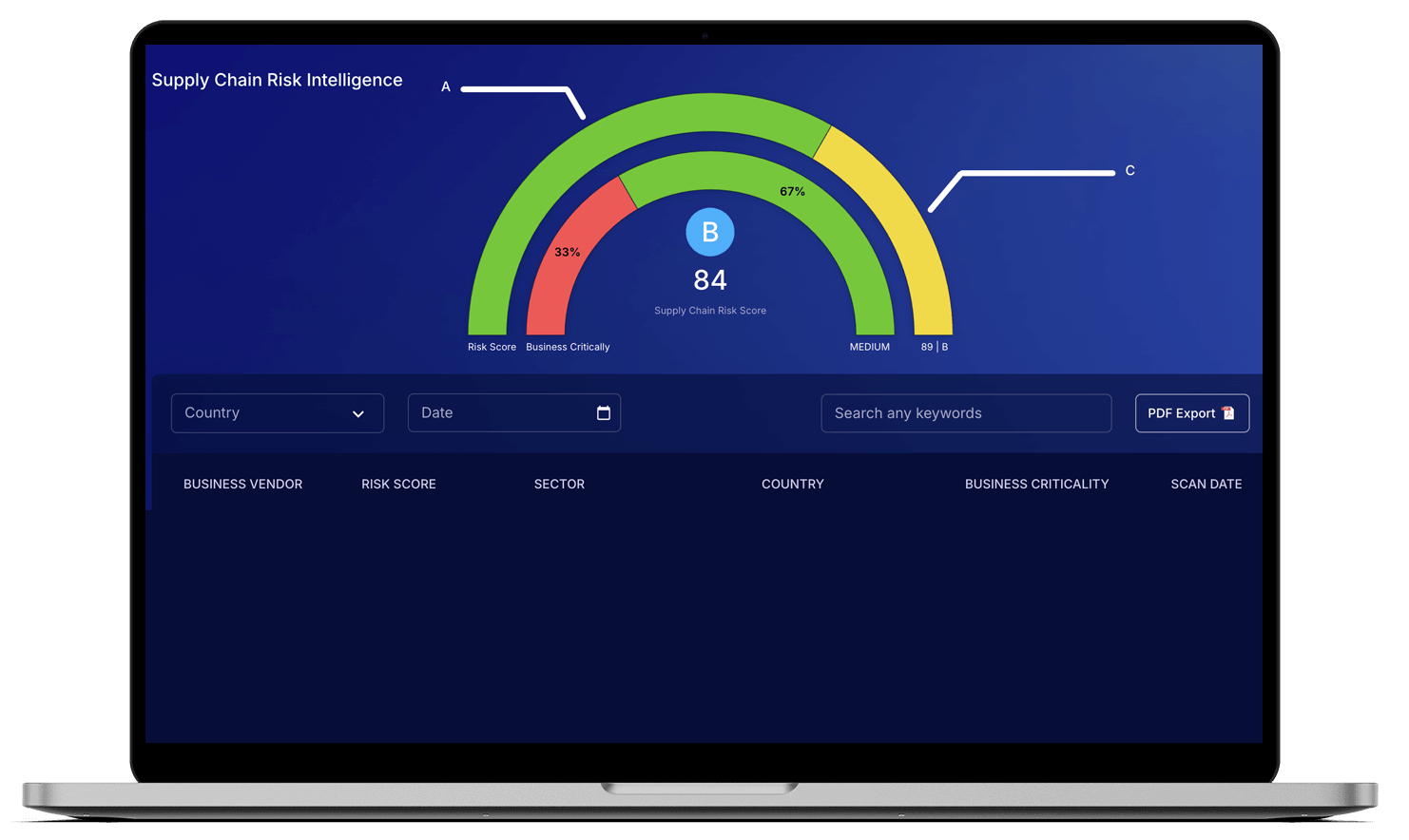
Today’s supply chains are complex, interconnected, and vulnerable. When a single vendor is compromised, the damage can ripple through your business — disrupting operations, exposing sensitive data, and damaging trust. You need complete visibility into your vendor ecosystem before attackers find the gaps.
ThreatMon’s Supply Chain Intelligence gives you full visibility across vendors, partners, and service providers by mapping and monitoring their digital footprint. It discovers domains, IPs, and assets, assigns clear risk scores across key security layers, and tracks vulnerabilities in real time. With detailed findings, remediation guidance, and one-click, audit-ready reports, you can manage supply chain risks confidently and proactively.
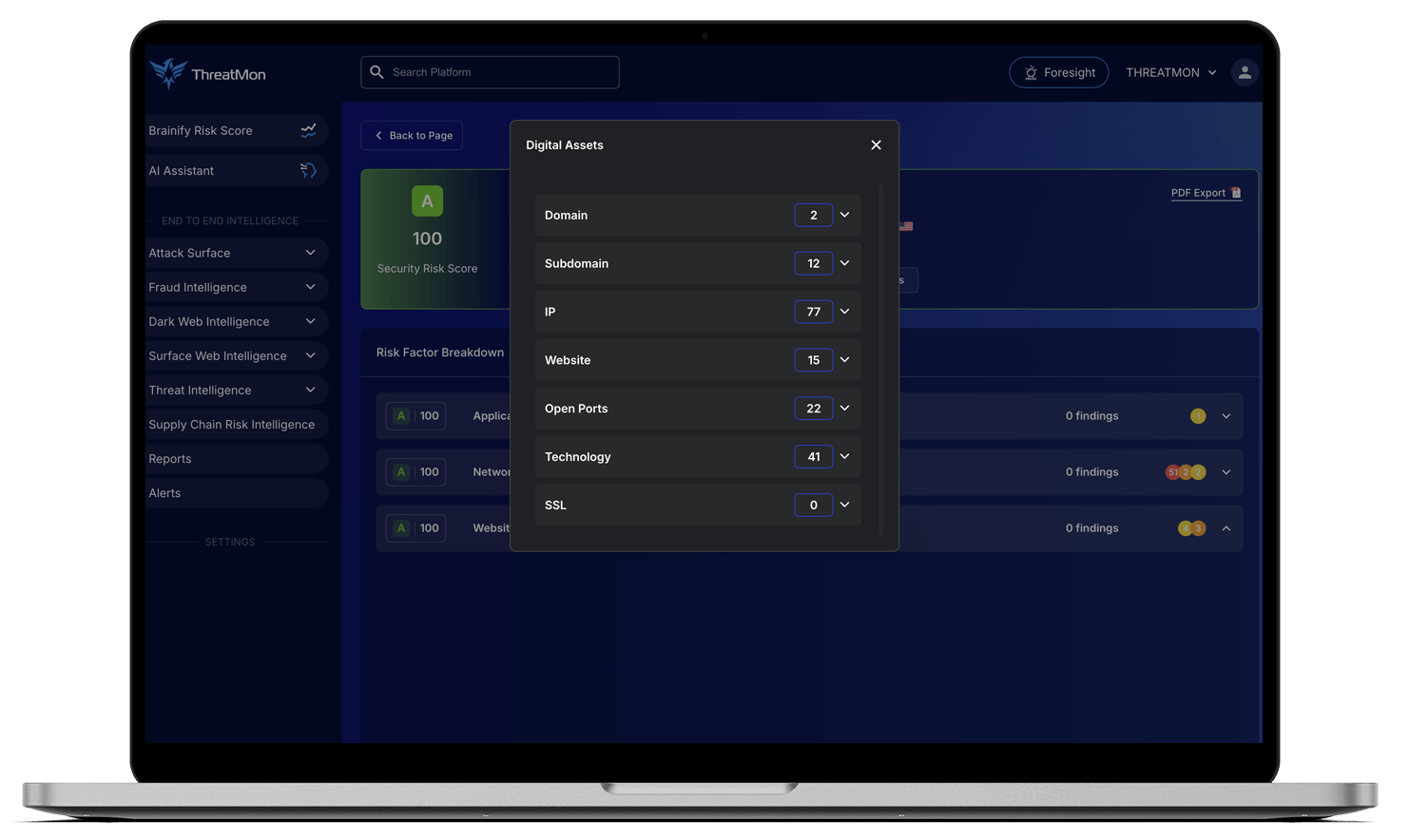
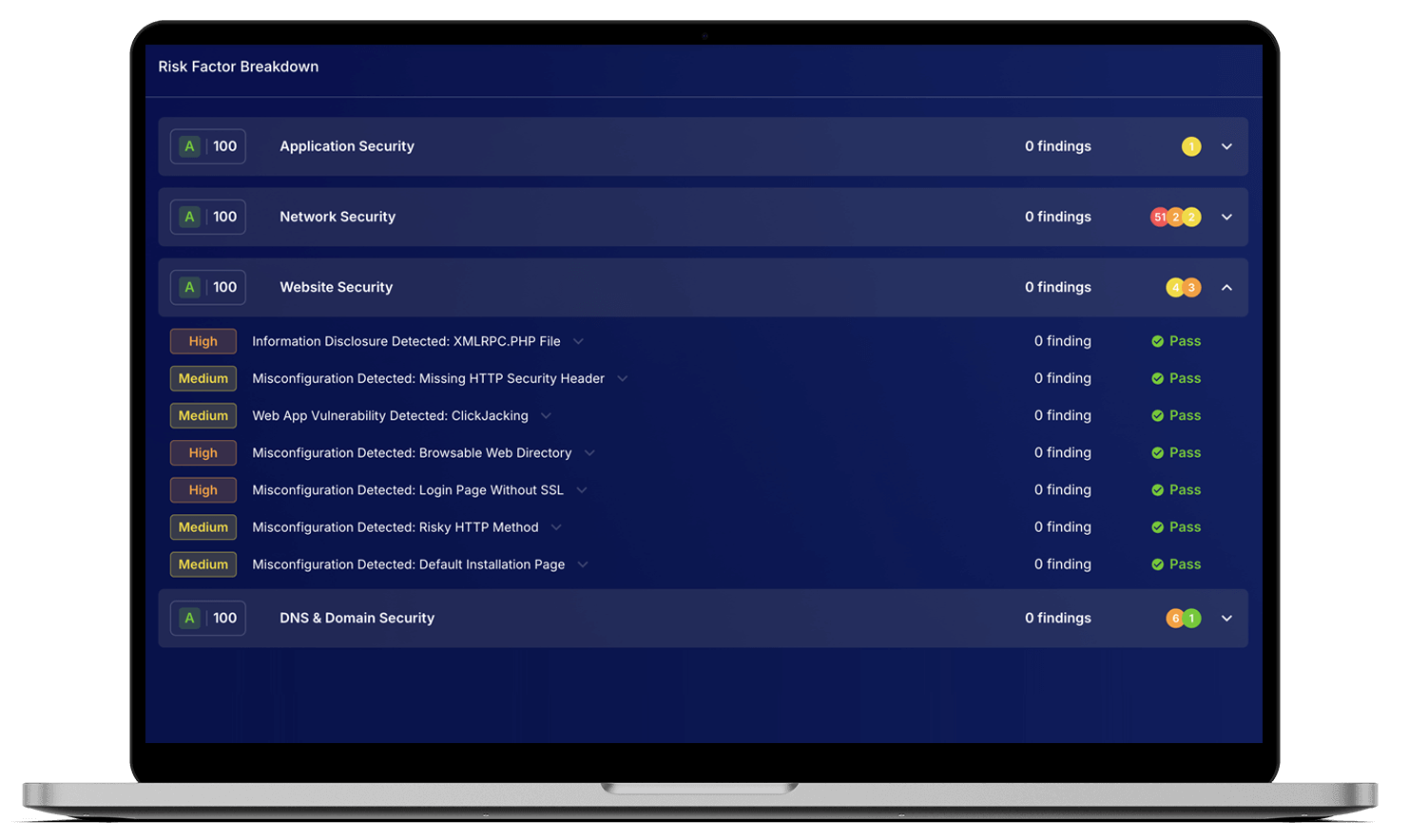
Unlike one-off assessments, ThreatMon delivers continuous monitoring so your risk view is always current. Whether you’re managing 5 suppliers or 500, you get a single source of truth for third-party risk. Our goal is simple: give you the tools to act early, act fast, and act confidently.