
Our MSSP Program has already helped providers scale their services with flexibility and speed. This month, we are introducing a major upgrade to the MSSP experience — both on the platform and in how we partner with MSSPs worldwide.
Improved Slot-Based Licensing
Plans now offer more flexibility for onboarding new clients, adjusting coverage, and upgrading protection tiers based on customer needs
Predictable Pricing with Better Margins
Optimized per-domain pricing helps MSSPs scale confidently while maintaining profitability
Custom-Branded Reporting Hub
Create polished, client-ready reports with your own branding — including PDF exports for compliance, executive briefings, or weekly reviews
Growth-Oriented Tiering Model
Built-in upgrade paths that support MSSPs as they grow from early-stage to enterprise-level portfolios
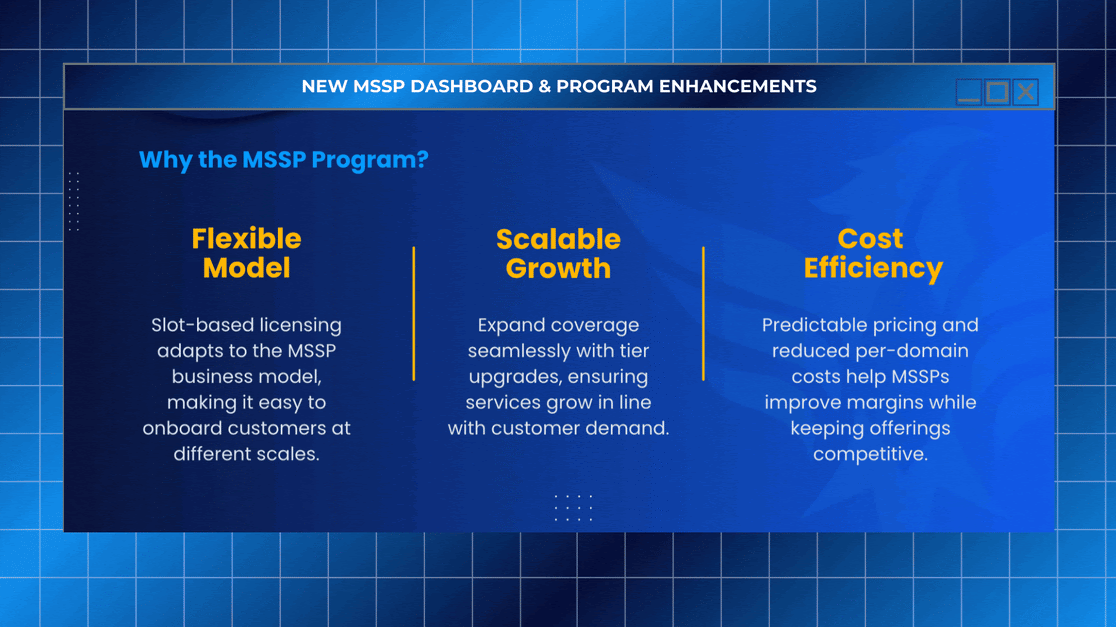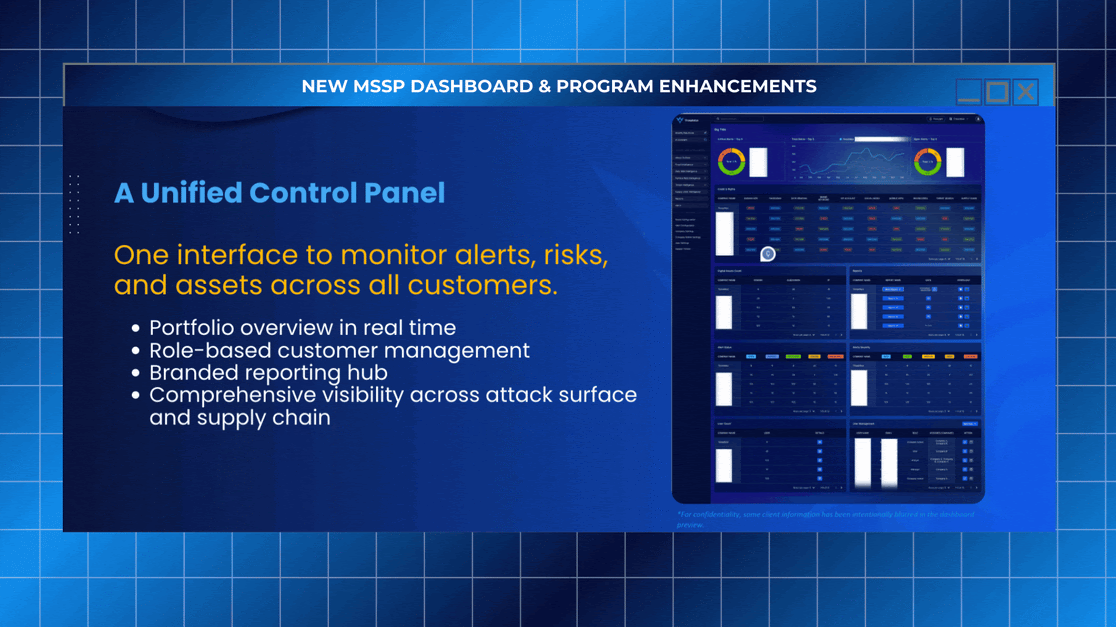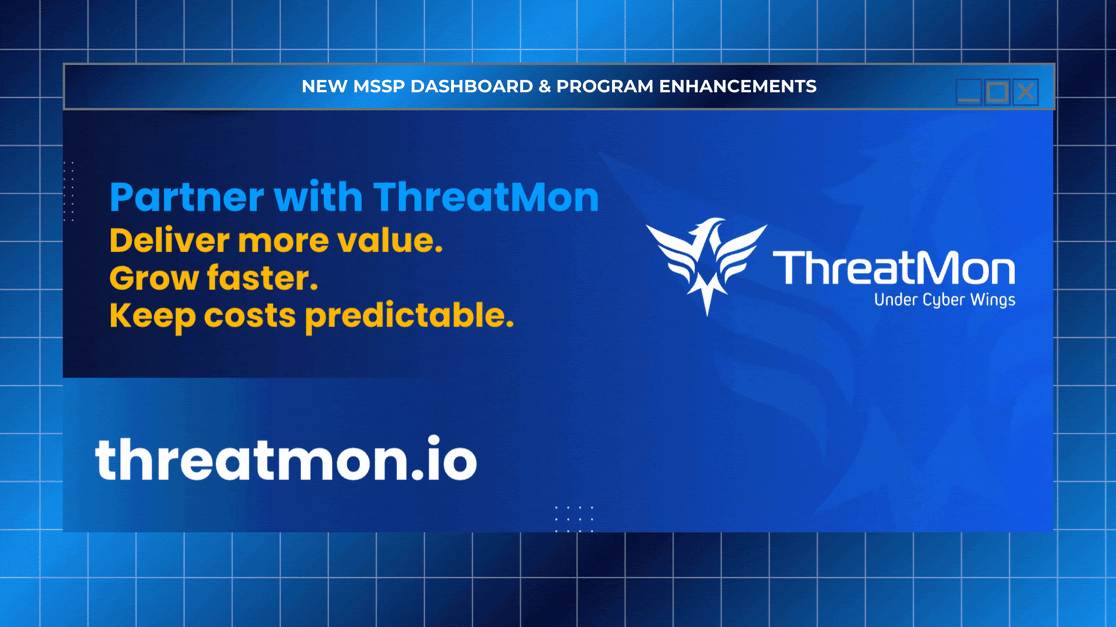
Monitor alerts, risks, and assets across all clients from one unified interface
Manage users and permissions through a role-based structure
Access a centralized reporting console that supports white-labeled client communication
Gain real-time visibility across attack surface, supply chain, and threat intelligence modules
These upgrades are designed to reduce operational complexity while giving MSSPs the insight and flexibility needed to deliver exceptional service at any scale.
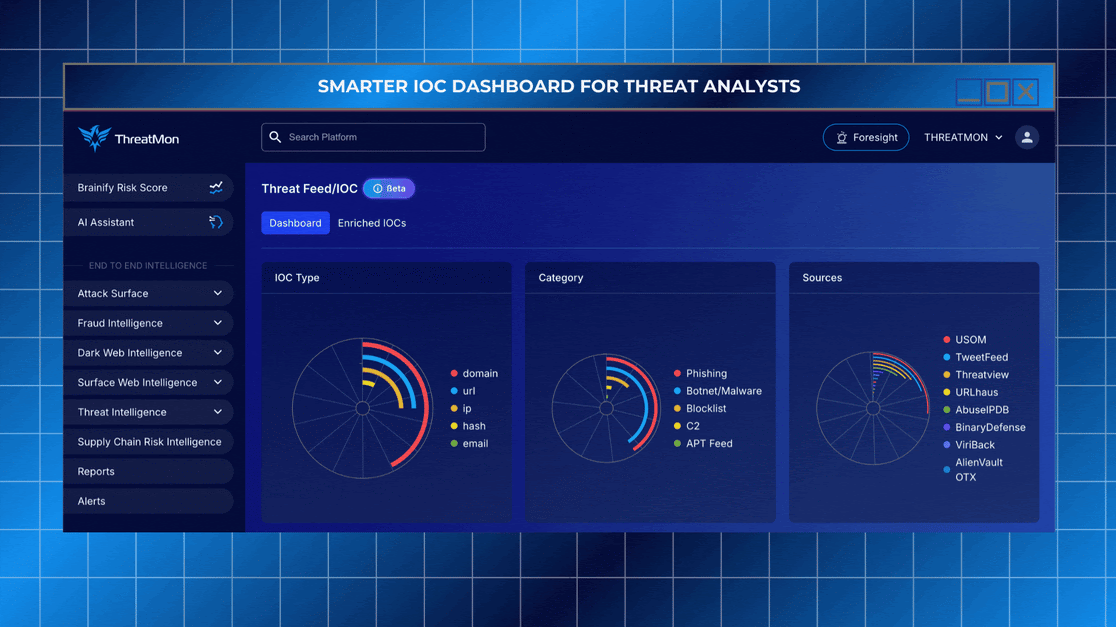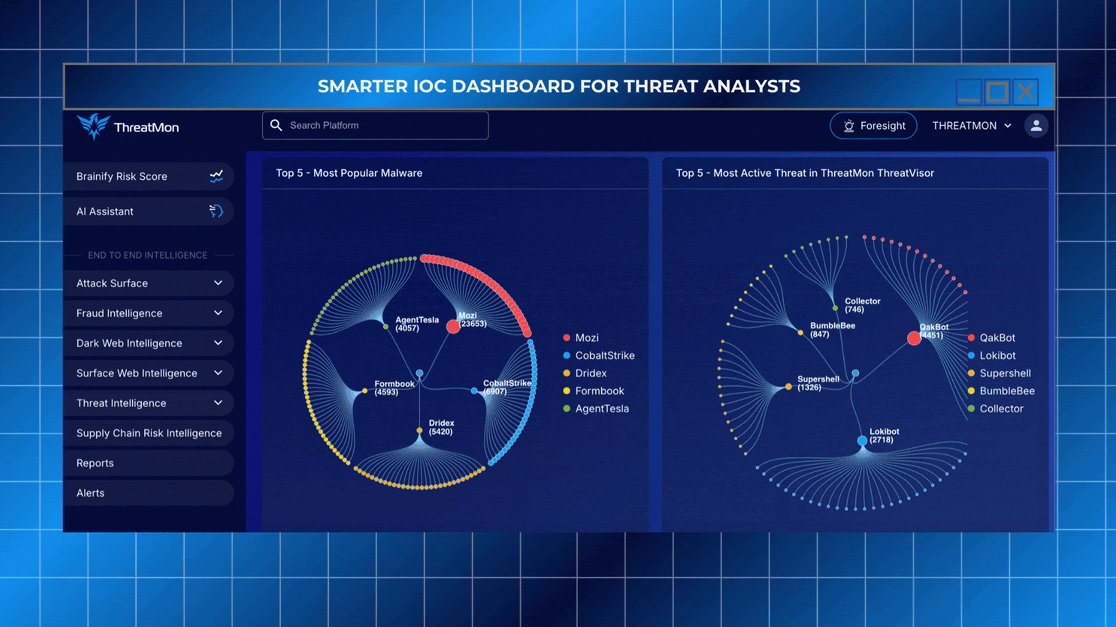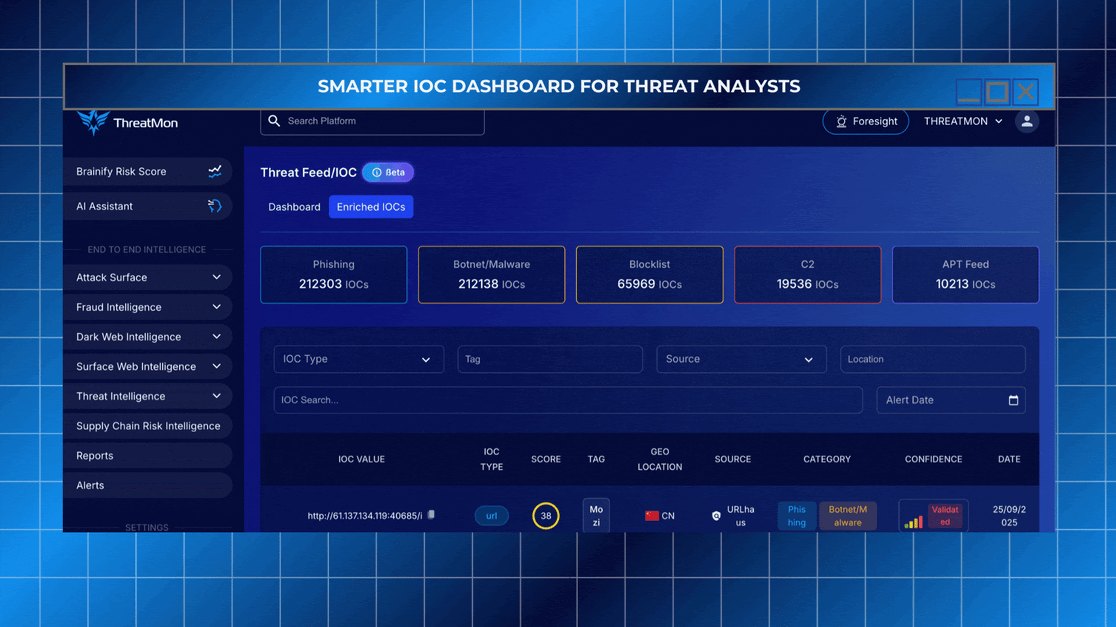
The ThreatMon IOC Dashboard has been redesigned to help security analysts and incident responders extract the most relevant signals from vast threat data. This experience is built to support both rapid response and deep investigation.
Filter IOCs by type (domain, URL, IP, email, hash) and severity
Sort intelligence by category including phishing, malware, APTs, C2 infrastructure, or blocklists
Trace IOCs back to trusted sources such as USOM, URLhaus, TweetFeed, Threatview, and more
Export enriched threat data to your own reporting workflows in PDF or CSV format
View IOCs in context with associated malware families, threat actors, and MITRE techniques
From a single URL to a full campaign, this dashboard helps you connect the dots faster.
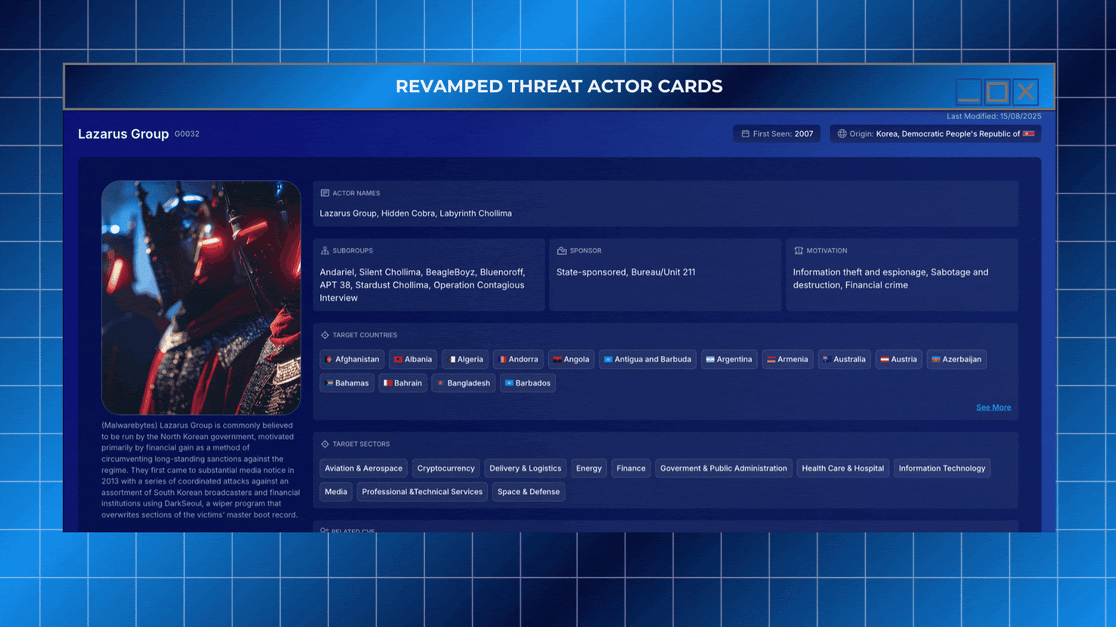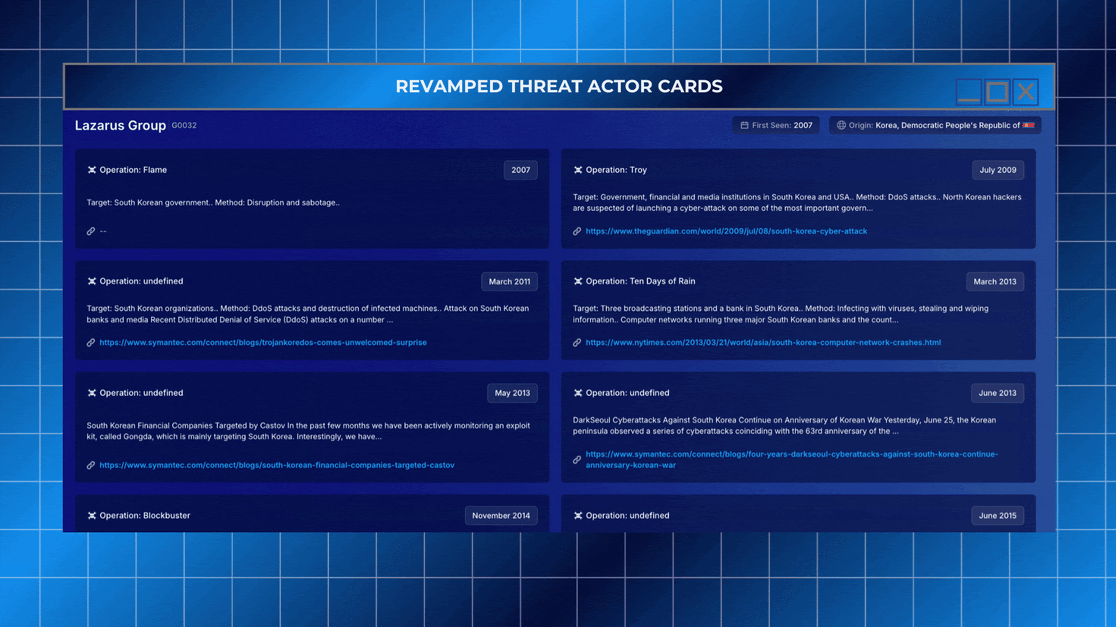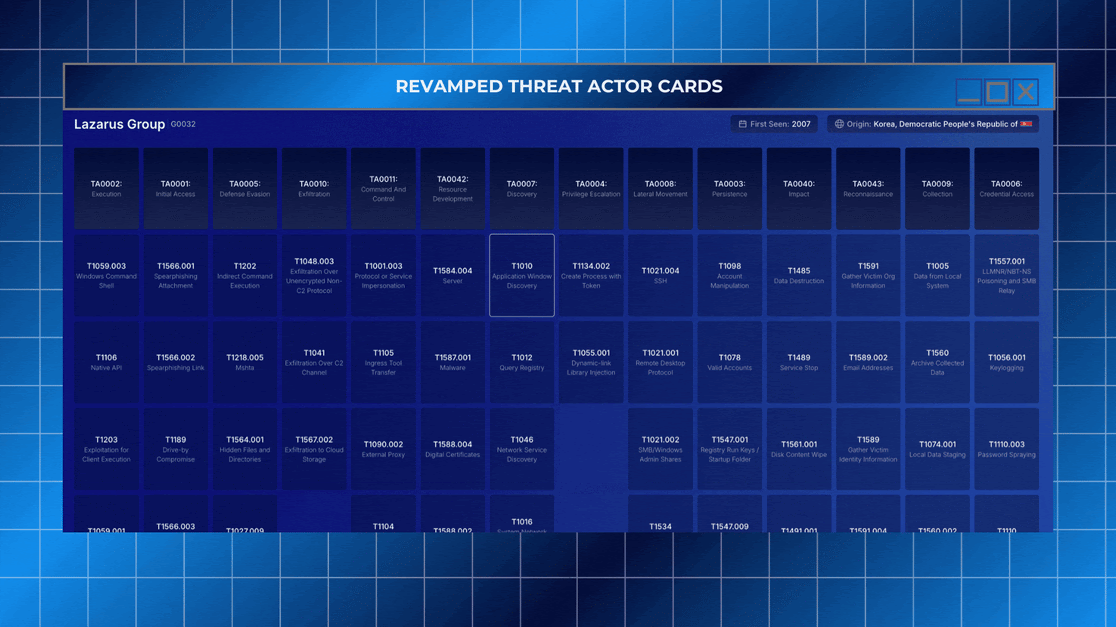
Our Threat Actor Cards have been completely redesigned to offer a 360-degree view of adversaries — making attribution, analysis, and response easier and faster for security teams. This update brings more structure, more data, and deeper interactivity across every card.
Now, analysts can move beyond basic naming conventions and access a full operational history, enriched with cross-linked threat intelligence.
This version of Threat Actor Cards helps analysts understand not just what happened, but who is behind it, how they operate, what they might do next, and where they are most likely to strike. From nation-state APTs like Lazarus Group to financially motivated collectives, your team is now equipped with the intelligence it needs — all in one place.
ThreatMon has been honored with 65+ G2 badges across Spring, Summer, Fall, and Winter — a recognition that reflects consistency, trust, and the voices of our customers worldwide.
We’re proud to be recognized as a top-rated platform by our users. These recognitions reflect our commitment to delivering exceptional value, seamless user experiences, and responsive customer support.
Every badge starts with you.
Thank you for trusting ThreatMon to deliver actionable intelligence and protect your business, no matter the season.
At ThreatMon, we believe in empowering businesses with the tools they need to stay secure in an ever-evolving threat landscape. These updates are just the beginning—we’re constantly working to enhance your experience and provide you with the best cybersecurity solutions.
Log in to your ThreatMon dashboard today to explore these new features and see how they can strengthen your cybersecurity strategy. If you have any questions or need assistance, our support team is here to help!