
In recent years, the cybersecurity landscape has witnessed the emergence of a new and formidable threat group known as AzzaSec. Founded on February 28, 2024, AzzaSec quickly gained notoriety for its hacktivist and financially motivated activities. This group, originating from Italy, has rapidly expanded its influence across Europe and beyond, collaborating with other notorious cyber threat actors and participating in high-profile attacks. Below is a summary of our recent cyber intelligence report on AzzaSec. Click here to access the report.
AzzaSec refers to itself as a hacktivist group. Tracing the roots of the formation, it goes back to pro-Palestinian activism, although their actions prove that there might be ideological and financial reasons. Initially purely hacktivist, and particularly in the context of the Palestinian cause, this cyber-group was deeply engaged in the Dark Web malware marketplace with ransomware and even PDF exploits. Such an approach has enabled AzzaSec to attract a huge following and become one of the key cyber threat actors.
AzzaSec does not localize its attacks in any way within a geographical region. The organization has attacked various countries, especially those deemed enemies of its ideology. Among these notable targets by AzzaSec are nations like the State of Israel and its allies and others such as Pakistan, whose political stand does not relate to that of the group. This clearly explains and displays the opportunistic nature of AzzaSec, targeting any entity with a vulnerability.
These include close collaboration with other cyber threat groups, which goes a long way in distinguishing AzzaSec. Among the hacktivist and not hacktivist-themed organizations it has cooperated with are Noname057(16) and APT44-related Cyber Army of Russia, which are pro-Russian. These alliances have given AzzaSec the advantage of stretching out its reach and increasing the efficiency of its attacks. Noticeably, after aligning with these groups, the group stopped its attacks on Russian entities, a clear strategic shift towards other nations, with Ukraine and the United States at large.
AzzaSec has been involved in numerous publicized cyber attacks, including DDoS attacks, server takeovers, ransomware operations, data leaks, etc. Some of the largest attacks include Israeli government websites, the Saudi Arabian Central Bank, and Ukrainian government sites. The group commands different advanced tools and techniques, many self-developed or acquired through alliances that place custom-made ransomware, botnets, and advanced obfuscation techniques at its disposal to avoid detection by antivirus software.
NoName057(16) is a pro-Russian hacker group that first declared itself in March 2022. It attacks government agencies, media, private companies, individuals, and organizations of countries opposed to Russia (Ukraine, America, Europe).
The Cyber Army of Russia is another large hacker group connected with the Russian Government. This group is particularly associated with APT44, previously known as Sandworm, which is linked to Russia’s GRU military intelligence unit.
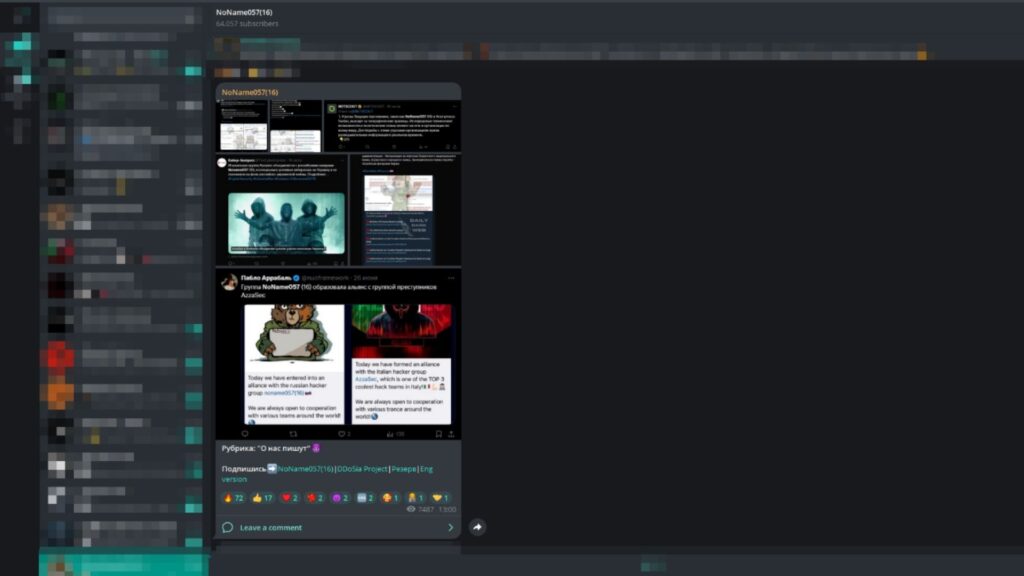
On June 26, 2024, the Italian hacktivist group AzzaSec and the pro-Russian threat actor group NoName057(16) announced their partnership.

On June 30, 2024, the Italian hacktivist group AzzaSec and the group related to APT 44, The Cyber Army of Russia, announced their partnership.
With the alliance established between the Italian hacktivist group and the pro-Russian threat actor group, the AzzaSec threat actor group has stopped all its attacks on Russia. This partnership has particularly posed a new threat to the USA and to Ukraine. The Hacktivist group is preparing for attacks on Ukraine and the United States.
The group is remarkable for the wide usage of privacy and security tools to hide their activity. It uses Proton VPN, Tor Browser, and Whonix OS, among others. AzzaSec also utilizes some custom-developed tools like LinxCrypt for secure communication, as well as some custom PHP scripts to execute ransomware attacks. Their tactics are sophisticated, employing advanced techniques such as SQL injection, command, scripting interpreter exploitation, and malicious code obfuscation.
Most of the members within AzzaSec are young males between 14 and 33 from Italy, Brazil, France, Turkey, China, and Russia. Financially, the members earn income from ransomware attacks and the sale of malware. Though AzzaSec is a new group, its impact has grown at an incredible rate due to the integration and cooperation between the underground and other threat actors.
AzzaSec is a large, evolving threat against the cyber world. While integrating hacktivist ideology with financial motivation makes this group a formidable opponent, its strategic alliances and sophisticated attack techniques make it one of the leading groups. As this group expands and grows, it poses an increasing risk to nations and organizations across the globe. Vigilance and advanced threat intelligence are critical to mitigate threats from groups like AzzaSec. Download the Unmasking AzzaSec: A Closer Look CTI Report to learn more.