
Over the past several years, ransomware attacks have skyrocketed and are now among the most costly and perilous threats to nearly all industries in the world. These attacks, which lock up a victim’s data and demand payment for unlocking it, can shutter operations, expose sensitive information, and cause millions in losses. The latest strain, known as Rhysida, recently targeted the Washington Times.
In this blog, we will provide a technical analysis of the Rhysida ransomware, examine the consequences of its recent attack, and explain how cybersecurity professionals can improve their defenses against its attacks.
Rhysida ransomware surfaced in the wild in mid-2023 and generated considerable discussion almost immediately due to its advanced capabilities, evasion techniques, and selectiveness regarding targets. Unlike most ransomware families in recent years, which favored brute-forcing large numbers of victims, Rhysida is all about quality over quantity—taking aim at very lucrative victims who are in a position to pay large ransoms.
An understanding of its technical details is of utmost importance to craft viable defenses against it. At its core, Rhysida Ransomware is highly effective because of a combination of primitives used: modern encryption techniques, obfuscation schemes, and persistence mechanisms.
Rhysida ransomware primarily spreads through two main methods:
Moreover, the Rhysida threat group exploits network infrastructure vulnerabilities that have not yet been patched in order to get a foothold into an organizational environment, such as web servers, email servers, as well as Remote Desktop Protocol (RDP) attacks against unpatched systems often using compromised credentials or brute-force attacks.
Rhysida’s encryption process is distinct from other ransomware in several technical aspects:
Rhysida uses a two-layer encryption scheme with ChaCha20 and RSA. The files are encrypted with ChaCha20, while the ChaCha20 keys and initialization vectors (IVs) are encrypted with a 4096-bit RSA public key. However, the two-layer encryption scheme using ChaCha20 and RSA is not really anything special compared to the two-layer encryption schemes used by other ransomware. It’s just rather impractical for files to be encrypted with ChaCha20 and ChaCha20 keys/IVs encrypted with an RSA public key. Most of the other popular ransomware families use AES.
Rhysida utilizes the LibTomCrypt library, an open-source cryptographic library, to implement its encryption routine. This includes using the library’s pseudorandom number generator (PRNG) functionalities to generate unique keys and IVs for each file. This approach is somewhat unusual as many ransomware families opt for custom-built or more mainstream libraries.
Rhysida employs intermittent encryption, a technique that partially encrypts files to speed up the encryption process. This method makes the data irrecoverable without a key, even though the entire file is not fully encrypted. Several ransomware groups use this technique to increase efficiency, but it can introduce vulnerabilities if not implemented correctly.
Researchers noticed that Rhysida had a particularly weak point in the encryption routine it used for transforming files – the bit that generated keys. Identifying and logging system time and other quirky data as seeds for random number generators meant that encryption keys themselves were not hard to predict, so the number of possible keys tended to be very low and became known. This kind of weakness isn’t present in more sophisticated ransomware, where key generation focuses on making the keys as strong and inherently unpredictable as possible.
These differences highlight Rhysida’s unique approach to encryption, combining both innovative and flawed techniques that distinguish it from other ransomware families.
Rhysida ransomware has been present in a number of high-profile incidents since it first emerged: it has already struck healthcare, local government, aviation, and other important institutions. Notably, Rhysida was used during a spate of attacks during 2021-22 by threat actors targeting critical infrastructure that led U.S. authorities to release multiple advisories. In 2019, the British Library was penetrated by Rhysida – the sheer fame of that point of entry does put Rhysida in some prestigious company. Others have included Brazil’s Unimed Vales do Taquari e Rio Pardo (Unimed), a healthcare provider.
As a result, Rhysida’s operations had an impact on victims spanning Western Europe, North and South America, and Australia, reflecting its wide operational footprint. Yet, despite these aggressive targeting practices, the technical inner workings of Rhysida’s malicious encryption operations have proven to be rife with error. Namely, researchers at Kookmin University and the Korea Internet and Security Agency in South Korea discovered vulnerabilities in the way that Rhysida encrypts affected data, ultimately leading to the development of a decryption tool that allows victims to recover their data without paying the ransom. The emergence of such research exposes not only chinks in the armor of Rhysida’s design but also the promise that technical intervention may have in the future to counter its attacks and, thus, reduce the impact of such ransom-based attacks on businesses and healthcare facilities alike.
As is the case with many ransomware attacks in that group, Rhysida’s Washington Times attack followed a predictable sequence of steps.
Rhysida likely gained access to The Washington Times systems through one of its common methods, such as spear phishing or exploiting unpatched vulnerabilities. These methods allow attackers to infiltrate a network by tricking users into downloading malware or by taking advantage of security weaknesses.
Once inside, Rhysida would have used tools like Cobalt Strike to establish a foothold within the network. This involves privilege escalation to gain higher-level permissions and lateral movement to spread across systems. During this phase, they gather information and prepare for the main attack.
Before encrypting files, Rhysida exfiltrates sensitive data. This is a critical step in their double extortion strategy, where they threaten to release the stolen data if the ransom is not paid. The data purportedly stolen from The Washington Times includes names, addresses, potential banking data, invoices, and sensitive personal information of at least one journalist.
After exfiltrating data, Rhysida executes its ransomware to encrypt files across the network. The encrypted files are typically renamed with a .rhysida extension. A ransom note detailing the ransom demand and instructions for payment is then left on infected systems. The note emphasizes the urgency and exclusivity of the data sale.
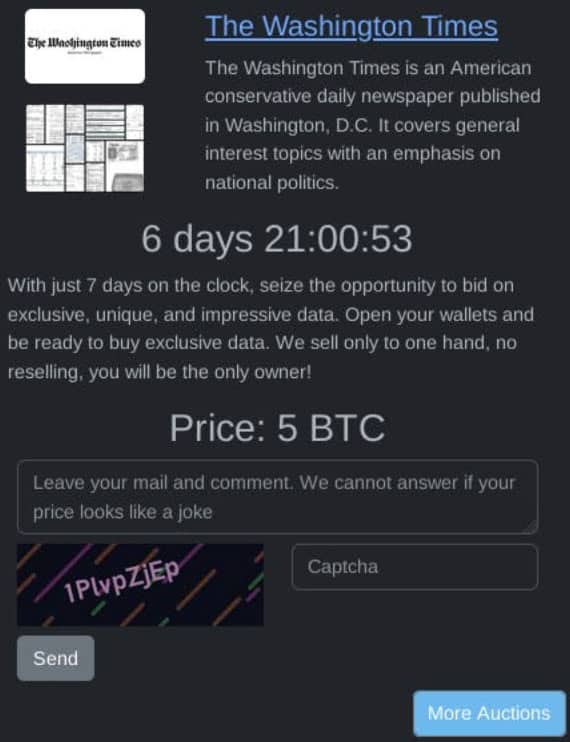
On August 15, 2024, Rhysida announced on its leak site that it was auctioning the stolen data from The Washington Times. The group set a price of five bitcoins and stated that the data would be sold to a single buyer, with no reselling allowed. They threatened to publish the data in seven days if it was not purchased.
As of the latest reports, The Washington Times has not publicly commented on the incident, and the auction remains open. Rhysida’s strategy involves maintaining pressure on the victim by setting a deadline for the auction, thereby increasing the urgency to pay the ransom.
Rhysida ransomware claimed to have stolen various types of data from The Washington Times.
The stolen data reportedly includes:

Rhysida is auctioning this data online, emphasizing that the sale is exclusive to a single buyer and that no reselling is permitted.
Rhysida is asking for 5 Bitcoins for the stolen data from The Washington Times. Based on the crypto market rates at the time of the report, this amount is equivalent to approximately $304,518.
The most immediate and obvious implication of the Rhysida ransomware attack on The Washington Times is that data was exposed. So far, Rhysida has claimed to steal the names, addresses, maybe banking details, invoices, and personal identification information of at least one journalist. Victims of the hack could suffer privacy violations, falling into greater risk of identity theft and other kinds of cyber crimes.
The ransom—5 Bitcoin, or roughly $304,000—could be too much for The Washington Times to pay. The newspaper’s owners would also have significant expenses for investigating the breach, upgrading cybersecurity infrastructure, and reputational costs from the damage to their brand.
Their reputation could take a hit, too – if The Washington Times is a target for ransomware, then what’s to say that its cyber defenses aren’t inadequate or inadequately resourced? That might influence the decisions of advertisers and readers. The newspaper’s website is still running seemingly unimpaired, but even an attack may disrupt operations if it forces systems offline to run checks, audits, or guarantees the return of files behind locked doors.
Moreover, the incident is symptomatic of the overall weakness of media houses to cyberattacks – it emphasizes the significance of having reasonable cybersecurity measures in place to ensure sound information lifecycle management and protect the integrity of data in addition to business sustainability. Therefore, the mentioned instances clearly demonstrate that the Rhysida ransomware attack on The Washington Times poses significant dangers to the newspaper’s operational integrity by threatening its financial standing and credibility while providing critical insight to other media organizations concerning protecting their proprietary information.
Organizations will need to strengthen their defenses against Rhysida and other ransomware. The NCSC and the CISA’s publications provide detailed recommendations on ransomware defense.
Advanced email filtering and ensuring that your employees have training regarding phishing significantly decrease the risk of ransomware getting through. Email gateways should be configured to block malicious attachments and links.
Make sure that systems are patched in a timely manner to fix known vulnerabilities. Rhysida, like many ransomware strains, can exploit out-of-date software. There are automated patch management tools that can help apply the latest critical updates to all systems.
restricting access between network components isolates one cell from another if there is a breach and prevents large parts of the network from being infected by a single ransomware cell. Especially in environments with sensitive data, network segmentation is important to prevent infecting the entire network if there is a single infection.
EDR solutions allow you to detect and stop ransomware from encrypting your data. EDR continuously identifies and responds to anomalies by collecting a complete history of your endpoints, analyzing it, and reacting promptly to any observed irregular activity.
Backups must be maintained in an offline state (not available over the network) that are no longer than one day old. To prevent permanent data loss, data cannot be restored unless a ransom is paid. Organizations must secure these backups against corruption and loss, ensuring that backups are air-gapped from the network and frequently tested to confirm data integrity and backup system availability.
Through threat intelligence services, you can benefit from details of new threats, such as Rhysida, before they unfold in the wild. By subscribing to threat intelligence feeds covering indicators of compromise (IOCs), new vulnerabilities, and attack toolkits used by ransomware groups, you can quickly adapt your predictive security controls and obtain powerful insights that can be useful toward planning your digital, human, and technological defenses.
Monitor the dark web for evidence of data leaks or credentials or chat about your organization. Many ransomware groups, such as the organization behind Rhysida, communicate with their victims, sell stolen data, or promote new campaigns on the dark web. Finding evidence of such a signal might trigger a fast response to mitigate any threat before it reaches fruition.
The Rhysida ransomware attack against the Washington Times illustrates the growing danger to organizations of all types of ransomware. The technical aspects of Rhysida and how it operates can help organizations defend themselves.
As cyber threats continue to evolve, keeping abreast of industry developments is imperative. The story of the Rhysida attack offers fresh insight into ways that we can strengthen our cybersecurity stance and better guard critical assets from the next ransomware assault.