SMTP open mail relay vulnerability occurs when a mail server is improperly configured, allowing unauthorized users to send emails through it.
SMTP, e-mail protocols are sets of rules that let different e-mail clients and accounts easily exchange information. It is also the only dedicated protocol for sending e-mails. Most e-mail clients including Outlook, Apple Mail, Gmail, and Yahoo Mail rely on SMTP to “push” or send messages from a sender to a recipient.
SMTP default ports:
This vulnerability could allow a sender to use e-mail server to send their e-mail. Threat actors can thus use server to distribute spam e-mails. Because of this, network bandwidth may overflow and e-mail server may be blacklisted.
Finally, once the host address resolves to the correct IP address and transfer it to another/secondary machine, etc.
2. It should be ensured that the security protocols for the server are active and that only users who provide username and password information can forward e-mails.
SMTP server may be expecting an authentication method that is not supported. If TLS is required, then enable it.
Check that the SMTP server is accepting authentication with SMTP username and password.
3. Should use an up-to-date TLS algorithm on SMTP server.
Should use the algorithms listed below that come with TLS version 1.3:
There are some browsers that do not support 1.3, which could result in a bad user experience. Additionally, if take out potentially vulnerable features like renegotiation and use PFS for applications’ TLS 1.2 configuration, get all the same security and privacy benefits as TLS 1.3. As far as a potential performance boost should be performed thorough testing to see if this is true for application as it may not be worth the effort with 0-RTT disabled.
4. Should be disabling the “Open Relay” feature of the server.
If “Open Relay” is turned on on an Exchange 2007 or Exchange 2010 server, there is a very simple command run from the Exchange Management Shell to turn it off.
The command is:
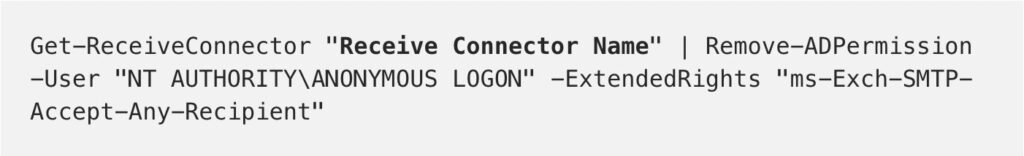
Exchange 2013 onwards command to check open relay on exchange servers:
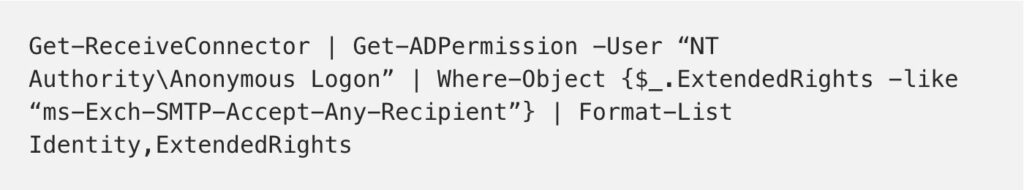
If in the case have found that the user “NT AuthorityAnonymous Logon” is having the permission “ms-Exch-SMTP-Accept-Any-Recipient” on the receive connector which is used to receive e-mails from the Internet then we need to remove that permission for that account on that particular receive connector.
To configure a Lotus Domino server from being an Open relay please do the following:
From the “Router/SMTP” tab, “Restrictions and Controls” tab, then from the “SMTP Inbound Controls” option, from the “Inbound Relay Controls” section, it is sufficient to set the following as an “Asterisk (*)”.
smtpd_sender_restrictions: Restrict sender for sending e-mail only if given criteria matched. In addition, the following options can be added:
smtpd_recipient_restrictions: This options allow to filter incoming e-mails based on criteria which will help to minimize spam e-mails: Some of the important options are: reject_non_fqdn_recipient, reject_unlisted_reciepient, permit_sasl_authenticated and reject_invalid_hostname. More options can be added as follows.
smtpd_relay_restrictions: Prevent others to use SMTP server to send e-mails. Most important setting is permit_sasl_authenticated. More options can be added as follows:
Also, authentication can be forced by removing the following option in the “/etc/postfix/master.cf” file.
https://postmarkapp.com/guides/everything-you-need-to-know-about-smtp
https://support.cloudshare.com/hc/en-us/articles/200701595-How-to-disable-an-open-SMTP-relay
https://smallbusiness.chron.com/setup-smtp-email-forwarding-46405.html
https://knowledge.broadcom.com/external/article/179041/how-to-stop-mail-server-being-an-open-re.html
https://community.hpe.com/t5/System-Administration/SMTP-Open-Mail-Relay-vulnerability/td-p/4003003