In this article, Nginx Server and its vulnerabilities, and ways to mitigate these threats will be talked about.
How to find the website’s server?
There are multiple tools available to find out which web server is used.
The first of these is curl -I command. curl -I command is run on terminal in order to learn web server.
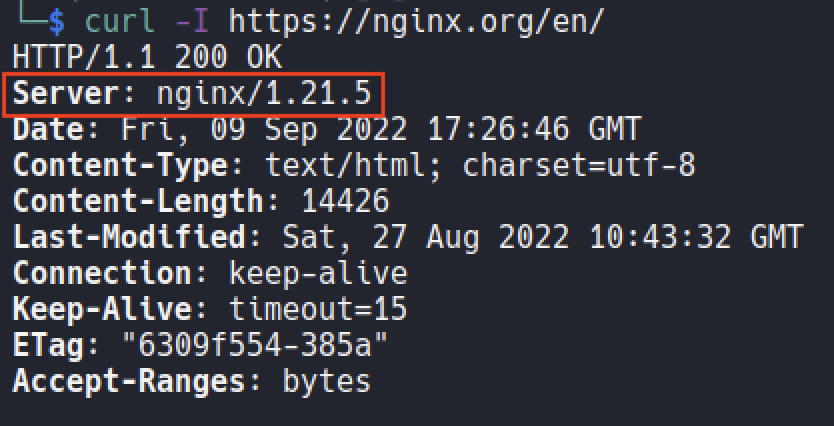
Second, It can be found by viewing the header in the browser.
These steps should be followed:
- Right-click on the page
- Click inspect
- Or use these commands to open the header: Mac: option+command i, Windows: ctrl+ shift i
- Click the Network tab in the header.
- Then refresh the page to view all uploaded files.
- Click on any of the lines containing the name and file.
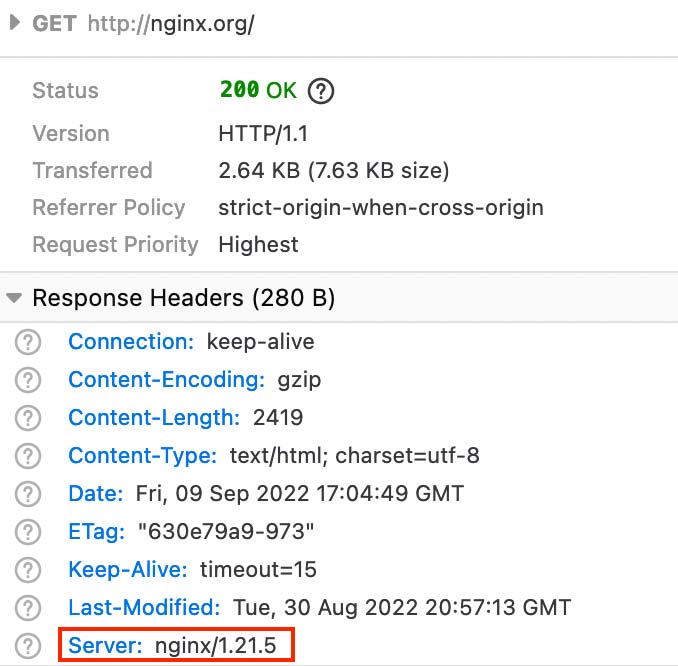
Here is the web server and version used on the website.
So what does this information do?
A threat actor that learns web server and version info used on the website can use this information for malicious purposes.
Web servers can contain exploitable bugs like any software. These can also be major flaws that could cause an attacker to remotely execute code in the system. RCE flaw 9.4, tracked with code CVE-2021-23017, is rated critical.
An attacker who exploits this vulnerability can escalate their privileges, causing more critical problems.
In addition, they can create buffer overflows to take control of the Web server and attack the system to replace Web pages or take them down.
For example, the vulnerability tracked by code CVE-2017-20005 (CVSS: 9.8) is a critical buffer overflow issue.
Mitigation and Remediation
It is mentioned above are just a few of the ways web servers can be exploited. There are important actions to be taken to mitigate these threats.
- It is important to upgrade web servers to their current versions in order to mitigate these threats.
- Second, the web server name can be changed or removed from the header in the browser. If an attacker can’t find the web server name and its version, there will be no such vulnerabilities.
These actions are important to protect the assets in the cyber world against a possible attack.
References:
https://www.tecmint.com/change-apache-server-name-to-anything-in-server-headers/
https://blog.avast.com/create-a-secure-web-server-avast







