The Microsoft Threat Intelligence Center (MSTIC) has taken action and taken measures to disrupt the campaigns launched by the SEABORGIUM actor, which has been tracked since 2017. SEABORGIUM is a threat actor with goals aligned with the interests of the Russian state.
SEABORGIUM is a threat actor that often targets the same organizations over long periods of time. It deepens their intrusion through constant impersonation, relationship building, and phishing to infiltrate the social networks of targeted organizations. Based on the actor’s tactics, SEABORGIUM overlaps with the threat groups tracked as Callisto Group (F-Secure), TA446 (Proofpoint), and COLDRIVER (Google).
While SEABORGIUM targets other countries in the Baltic, Northern and Eastern Europe, it primarily targets NATO countries, primarily the USA and the United Kingdom.
“Such targeting included Ukraine’s government sector in the months leading up to the Russian invasion and organizations involved in supporting roles for the war in Ukraine,” Microsoft said in the report.
SEABORGIUM focuses its operations in target countries primarily on defense and intelligence consulting firms, non-governmental organizations (NGOs) and intergovernmental organizations (IGOs), think tanks, and higher education.
Threat Actor Activity
Based on some observed impersonation and targeting, the threat actor is suspected of using social media platforms, personal directories, and public open-source intelligence (OSINT) to support reconnaissance efforts. MSTIC, together with LinkedIn, observed that fraudulent profiles thought to belong to SEABORGIUM were used to conduct discoveries of employees from relevant organizations. Based on its policies, LinkedIn has closed all accounts found to be engaging in unfounded or fraudulent behavior.
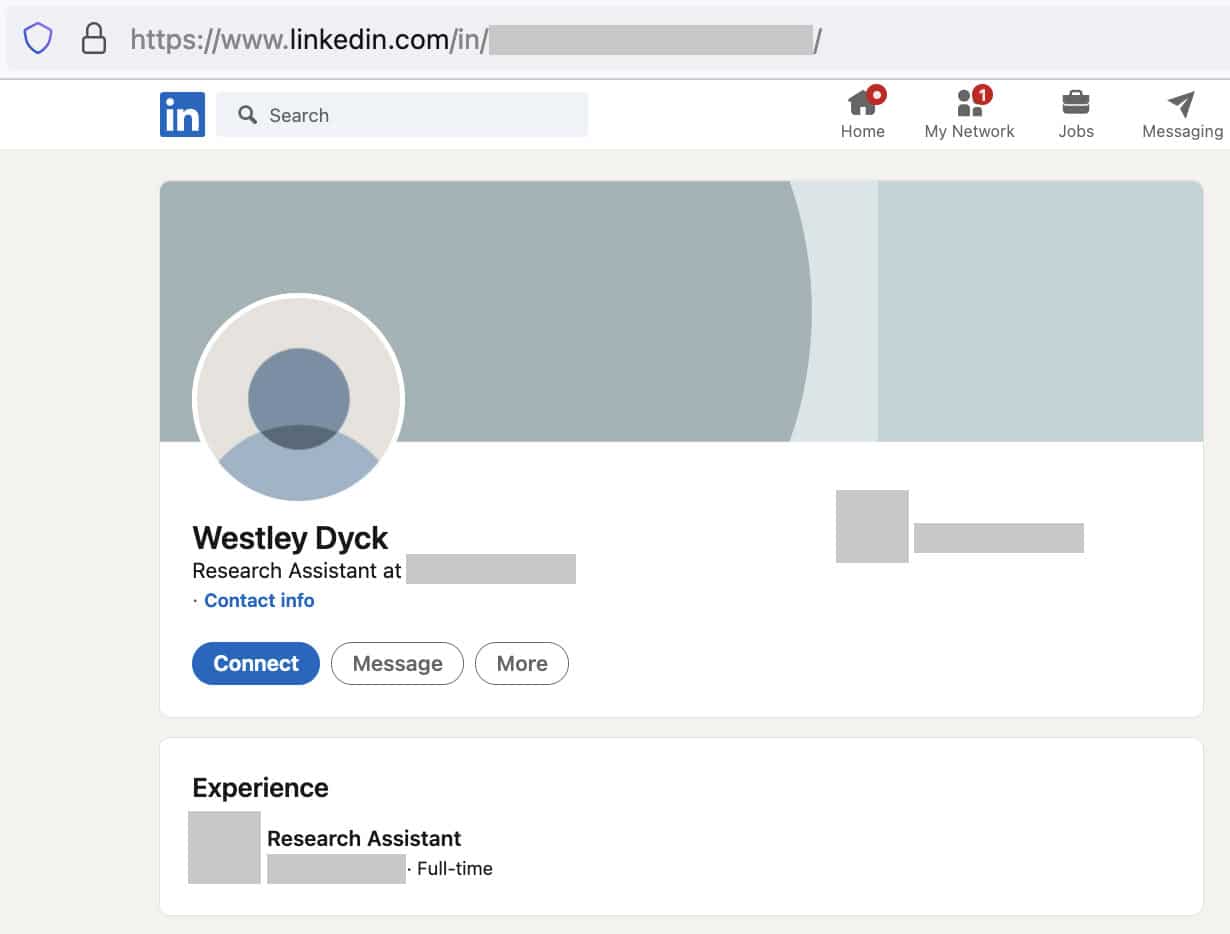
Source: Microsoft
SEABORGIUM also opens new e-mail accounts at various consumer e-mail providers that are configured to have their e-mail address or alias match legitimate aliases or the names of impersonators.
In personal or consumer targeting situations, MSTIC has often observed that the actor begins the conversation with a bona fide email message, typically chatting about a topic of interest to the target before referring to a non-existent attachment. If the target responds, SEABORGIUM continues to send an armed e-mail.
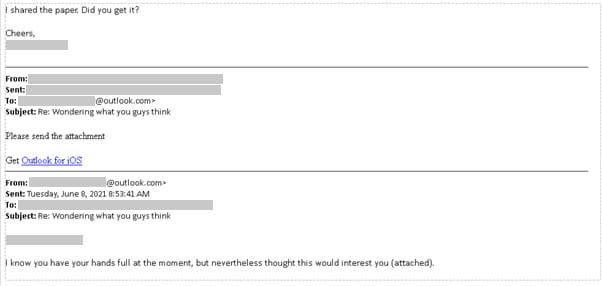
Source: Microsoft
“SEABORGIUM directly adds a URL to the body of their phishing email. Occasionally, the actor leverages URL shorteners and open redirects to obfuscate their URL from the target and inline protection platforms.” Microsoft explained.
SEABORGIUM uses OneDrive to embed PDF files with links to the malicious URL. This does not indicate a security issue with OneDrive.
It convinces the victim to click the link that will be redirected to the infrastructure that steals their credentials. Sometimes it uses explicit redirects within the PDF file to further hide its operational infrastructure.
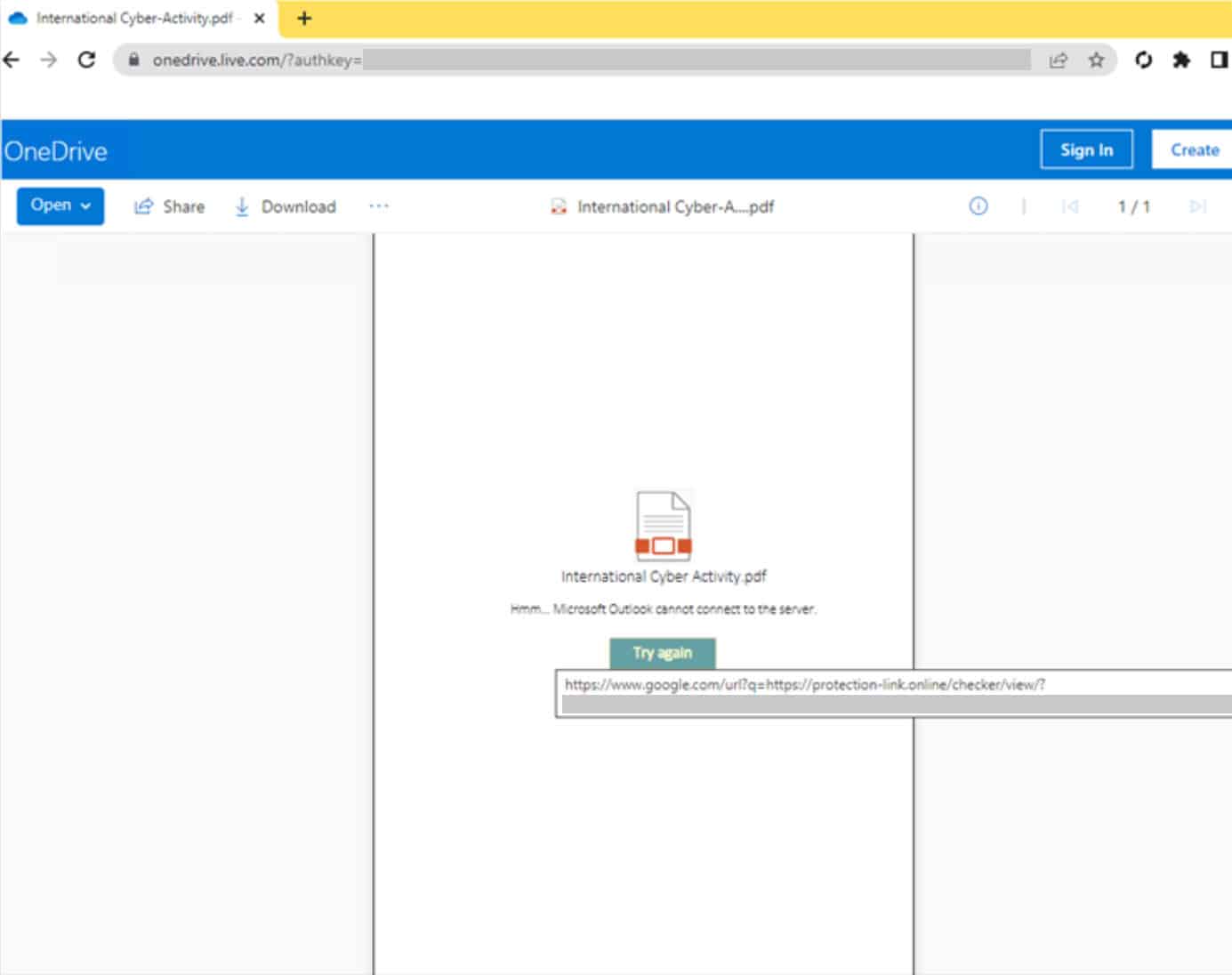
Source: Microsoft
When he clicks on the target URL, he is taken to an actor-controlled server, often hosting a phishing framework like EvilGinx. It requests authentication from the target, capturing all credentials. Once the credentials are received, they are redirected to a target website or document to complete the interaction.
In May 2022, Reuters announced that SEABORGIUM, together with Google TAG, were building a narrative that participants were plotting a coup, by leaking emails/documents allegedly stolen from consumer Protonmail accounts of top Brexit advocates. The narrative was amplified using social media and certain politically themed media sources that gave quite a bit of reach.
Here are some customer actions recommended by Microsoft.
- Check your Office 365 email filtering settings to block spam and malicious emails.
- Configure Office 365 to disable automatic email forwarding.
- All accounts require MFA and FIDO security keys for added security.
- Use IOCs to investigate possible security breaches.
References:







